Catch of the Day: Fund Transfer Phish
Chef’s Special: Browser Based Phish
Also serving: Remote Desktop Phish
Examples of clever phish that made it past my anti-spam nets and into my inbox. Some are contributed by clients or readers like you, and other reliable sources on the Internet.
You can send phishing samples to me at phish@wyzguys.com.
My intention is to provide a warning and show current examples of phishing scams, related articles, and education about how these scams and exploits work, and how to detect them in your inbox. If the pictures are too small or extend off the page, double clicking the image will display them in a photo viewer app.
Fund Transfer Phish
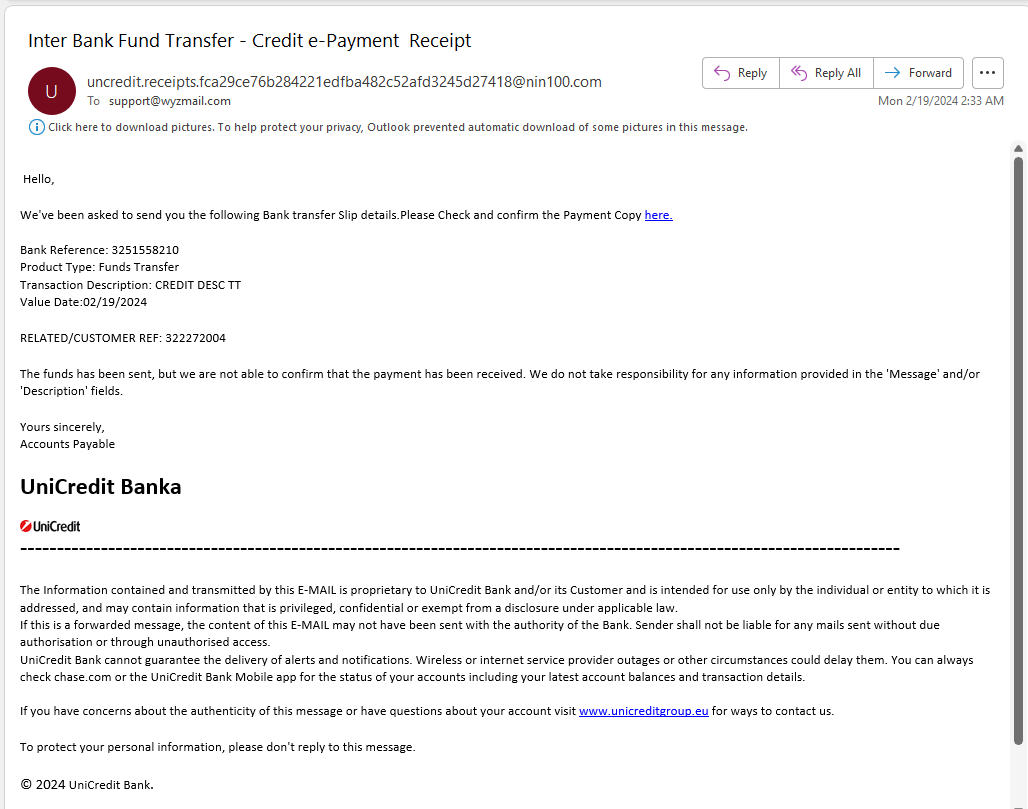
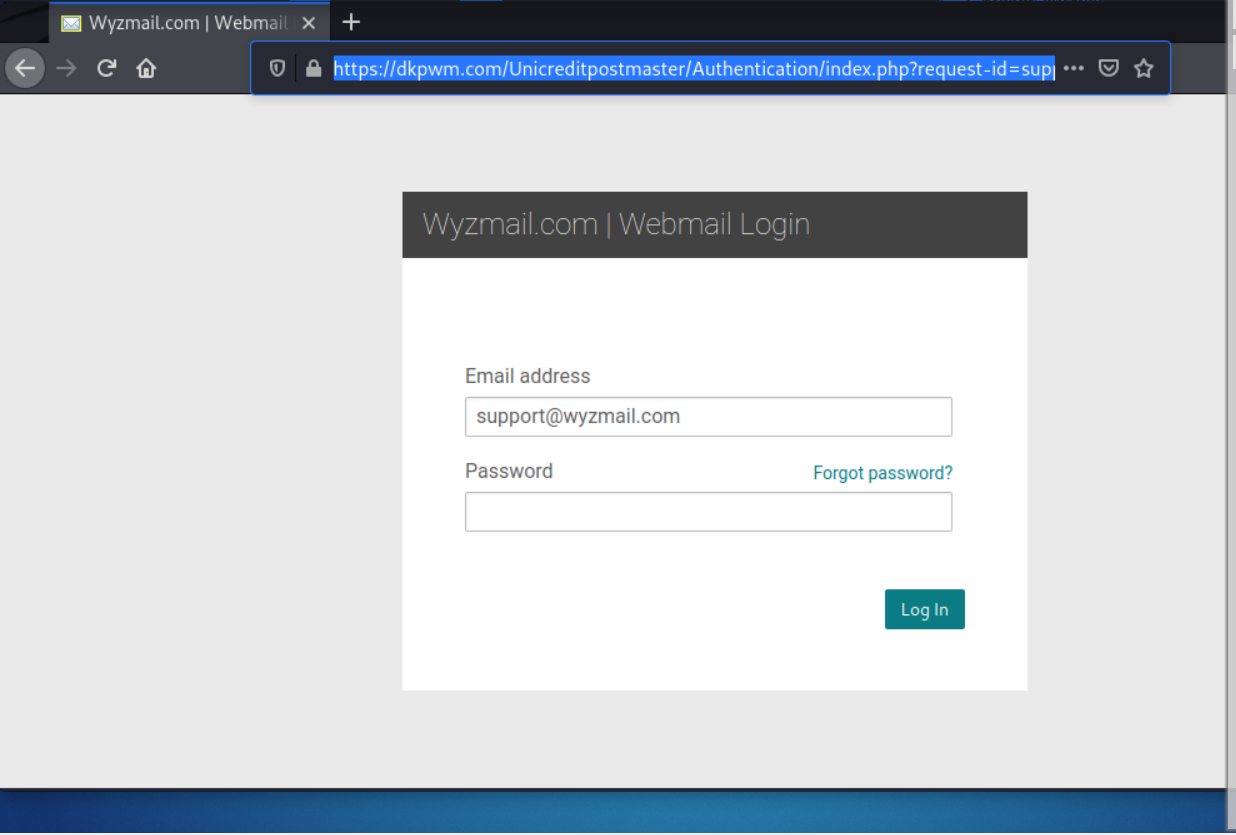
Here is an email I received Monday Feb 19 at 2:33 am CST. Since this arrived from a bank I have never heard of, I was able to avoid this exploit. The here link at the end of the first sentence resolves to http://tracking.nin100.com/tracking/click?d=M1SsPoXHFnxUC37foXMkemC8pt7C-K4I6v-SQGVfFM5kIRzgpDuatclA33I9btTNuO0Clhdp-uZMUSDH_emjEV-Qe_H4cpu_xXS84gVvSc9Sp2o6u5r_RvUgW_wklfRrU6mpD3tdWSSnpVXAYHtEbmNjZj2sfi-PNu3xuiA1Vl5ISu3sqAruOJKC6NVMpjiEWIb6SSqDT6yfoJGT3ZTkZCWgpYx5NUWZsOrltJ7QN8Zh0 and was redirected to the landing page at https://dkpwm.com/Unicreditpostmaster/Authentication/index.php?request-id=support@wyzmail.com#url=https%3A%2F%2Fsalesagreement.adobesign.actions.auth.A5ElylDNyz4gqN9hJXrAamp.wyzmail.com%2Flogin%2F.
Here is the email:
And here is the landing page. Just another example of a credential stealing exploit designed to provide the attackers with the password to my email account. Account hijacking would allow the attacker to impersonate me by using a legitimate email account of mine.
Browser-Based Phishing Attacks Increase 198%, With Evasive Attacks Increasing 206%
A new report shows massive increases in browser attacks in the second half of 2023, with over 31,000 threats specifically designed to bypass security solution detection.
But when cybercriminals target browser users, there’s an entirely different level of trust. With email, there’s a level of expectation around how an email should look, where it’s from and what it should contain.
But when it’s a browser, all it takes is a convincing webpage or the misuse of an exploit to potentially invoke and start off an attack. And according to security vendor Menlo Security’s State of Browser Security report, these browser-based phishing attacks are very much on the rise — remember, when we’re talking about 200% increases.
That’s huge.
Menlo Security detected over 550,000 browser-based attacks in 2023 — something organizations typically have little visibility into. And the use of evasive techniques is also growing. Menlo provides the example of Legacy URL Reputation Evasion (LURE), where URLs are either hijacked trusted sites, or domains left dormant until their URL reputation builds over time.
Phishing Campaign Exploits Remote Desktop Software
A phishing campaign is attempting to trick users into downloading remote monitoring and management (RMM) software like AnyDesk, Atera and Splashtop, according to researchers at Malwarebytes.
While these tools are legitimate, they can be exploited by threat actors to carry out many of the same functions as malware. These tools may also be less likely to be flagged as malicious by antivirus software.
“The modus operandi of these threat actors involves deceiving employees through sophisticated scams and deceptive online advertisements,” the researchers write. “Unsuspecting employees, misled by these tactics, may inadvertently invite these criminals into their systems.
“By convincing employees to download and run these seemingly benign RMM applications under the guise of fixing non-existent issues, these fraudsters gain unfettered access to the company’s network.”
The scammers trick users into visiting a phishing site that impersonates the user’s bank. “We believe victims are first targeted and then contacted via phishing emails or text messages (smishing) based on their position in the company,” the researchers write.
“Attackers could trick them by sending them to a typical phishing page or making them download malware, all of which are good options. However, they are instead playing the long game where they can interact with their victims.
“Users are directed to newly registered websites that mimic their financial institution. In order to get support, they need to download remote desktop software disguised as a ‘live chat application.'”
The phony live chat application is actually a version of the AnyDesk remote desktop software. “In this instance they are using a legitimate (although outdated) AnyDesk executable which would not be detected as malicious by security products,” Malwarebytes says. “Running the program will show a code that you can give to the person trying to assist you. This can allow an attacker to gain control of the machine and perform actions that look like they came directly from the user.”
Blog post with links:
https://blog.knowbe4.com/phishing-campaign-abuses-remote-desktop-software
Share
FEB





About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com