Phishing Email Alerts
Catch of the Day: FedEx Shipping Phish
Chef’s Special: Bit.ly Link Phish
Examples of clever phish that made it past my spam filters and into my Inbox, or from clients, or reliable sources on the Internet.
I would be delighted to accept suspicious phishing examples from you. Please forward your email to phish@wyzguys.com.
My intention is to provide a warning, examples of current phishing scams, related articles, and education about how these scams and exploits work, and how to detect them in your own inbox. If the pictures are too small or extend off the page, double-clicking on them will open them up in a photo viewer app.
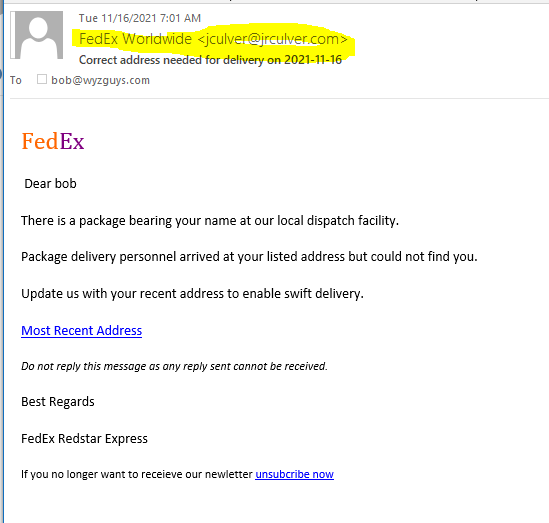
FedEx Shipping Phish
‘Tis the season for holiday scams, and wayward shipping scams are part of the usual types. I received this email from FedEx Worldwide but the email was from jculver@jrculver.com. The Most Recent Address link resolves to http://bob722322708.aut1.top/#Ym9iQHd5emd1eXMuY29t and is redirected to https://webnyx.in/sk/check.php?tap=1DLtqCkMZmXtIC61k0JkWfmKGXJEGpatsZZzUgNqeroftkl7AHkbtIXK0GNCYVRnXeoRKEl1J4GcVsNlM4ZeIfIryxF7yqU9Zq3o51XqU1VgouXC7hs63BS5BYMdP9Vy.
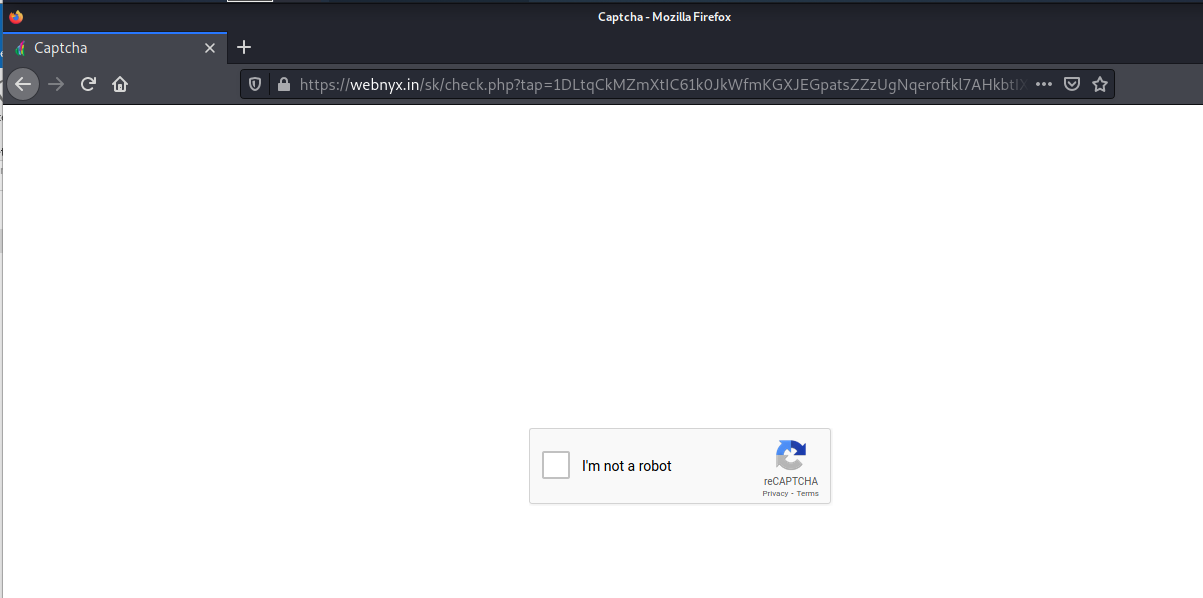
The landing pages used standard “I am not a robot” CAPTCHA images to lull the recipient into a false sense of security. Lets take a look, first at the email
Here is the first landing page with the I am not a robot check box
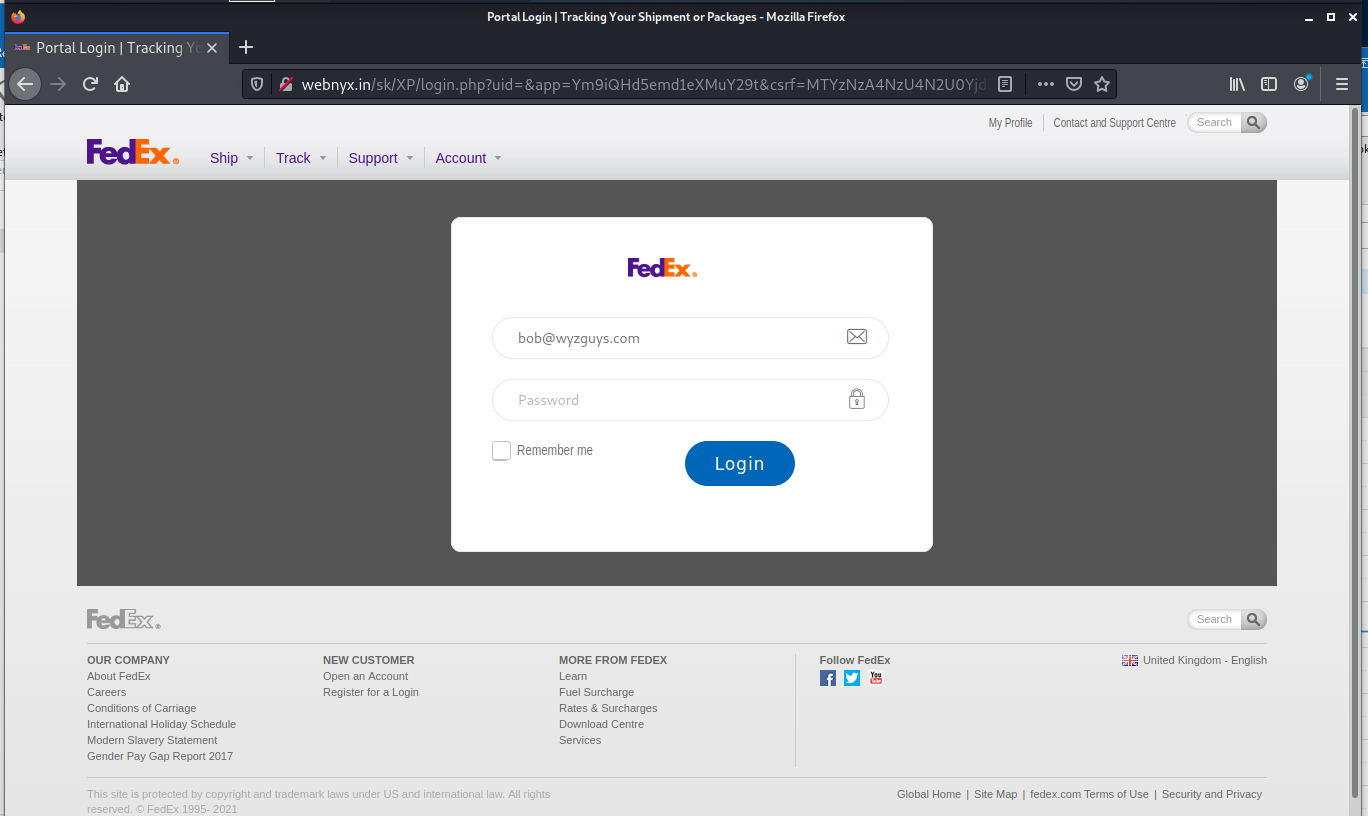
Then the images. I actually got two different pages.
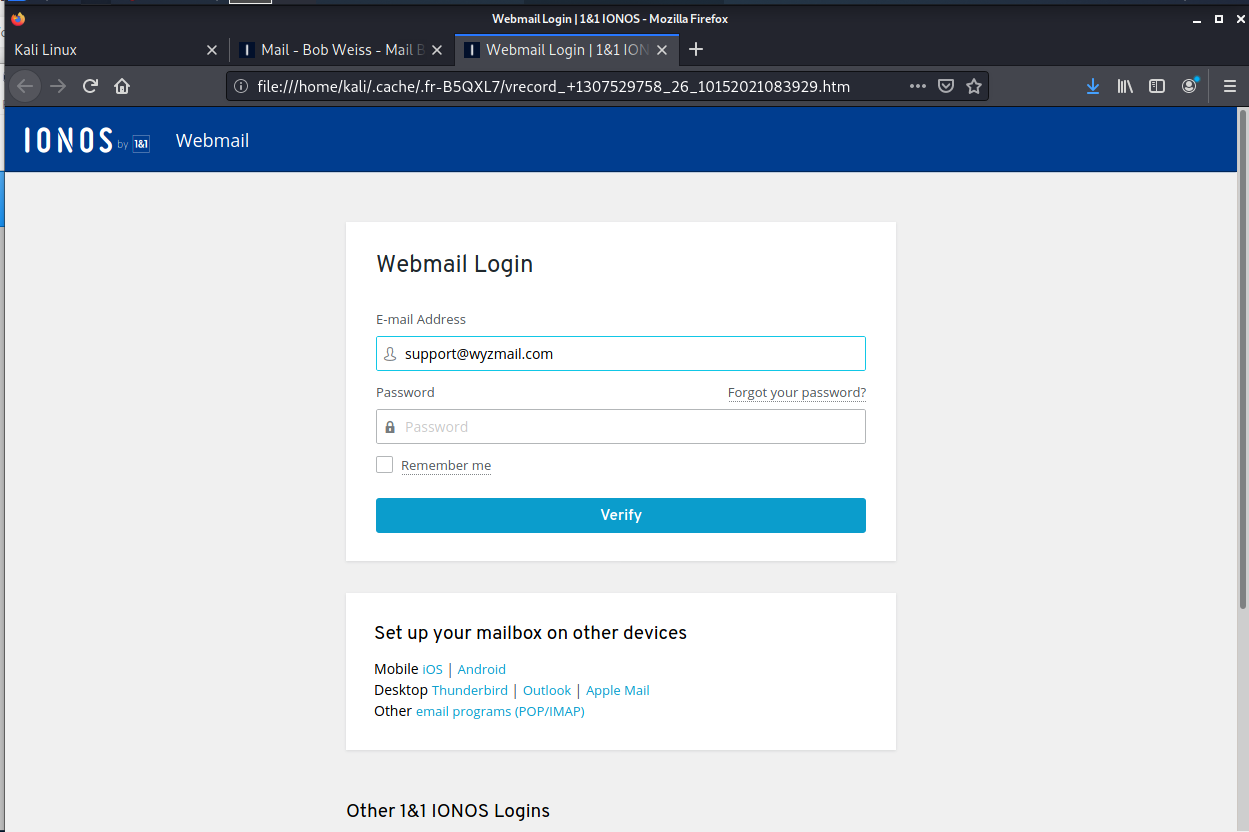
And finally the credential stealing page.
I tried to enter a fake passwords, but was warned off by my web browser. Pay attention to these warnings. They are there to save your bacon.
The Bitly Phish
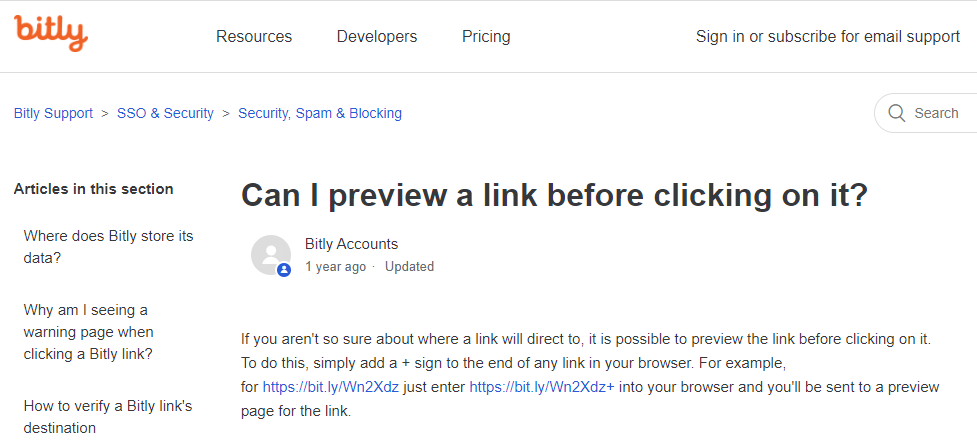
I hate bit.ly links. There is no easy way to resolve the real destination of a bit.ly link by simply hovering over the link and waiting for the tool tip box. Or is there? I received an email with a bit.ly link in it and I wanted to track this exploit down to see what it was trying to accomplish. So I Googled to find out if there was an easy way to resolve this link and found this topic. Simply adding a plus sign to the bit.ly link would reveal it’s destination
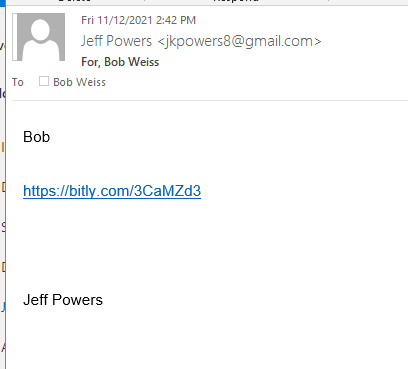
Here is the phishing email. It appeared to come from Jeff Powers <jkpowers9@gmail.com>. According to the email headers, the source is really jkpowers8@essay.docotor. So there is some sort of email account hijacking and/or spoofing going on here.
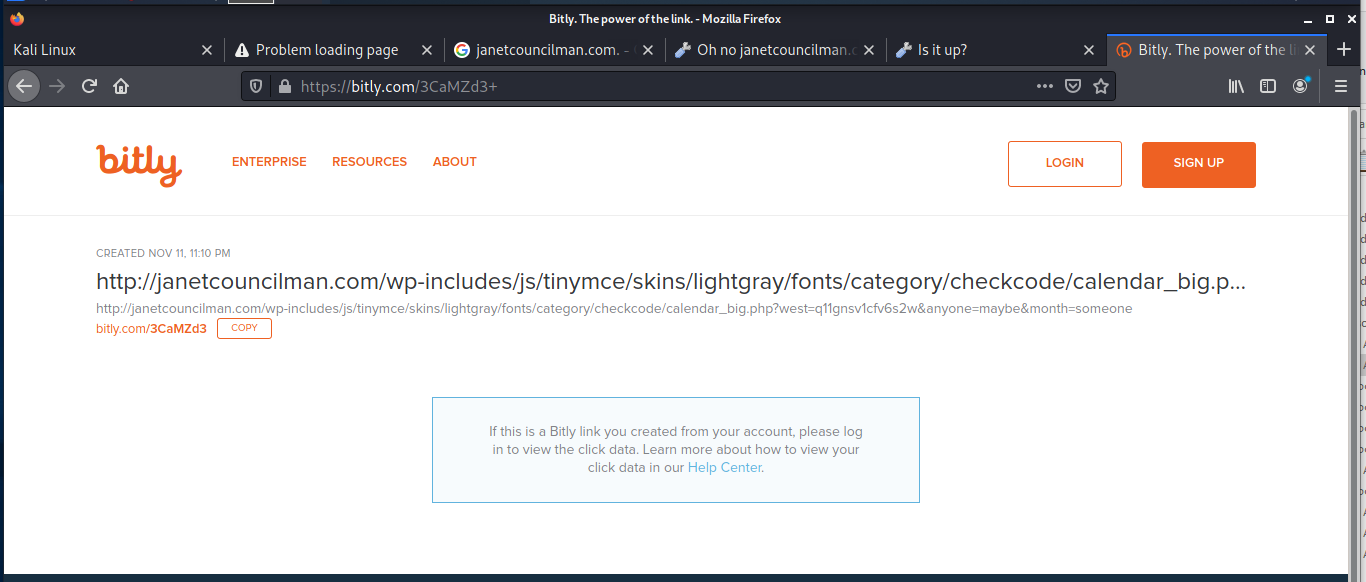
So just where does this link resolve? I tried the solution from Bit.ly Support
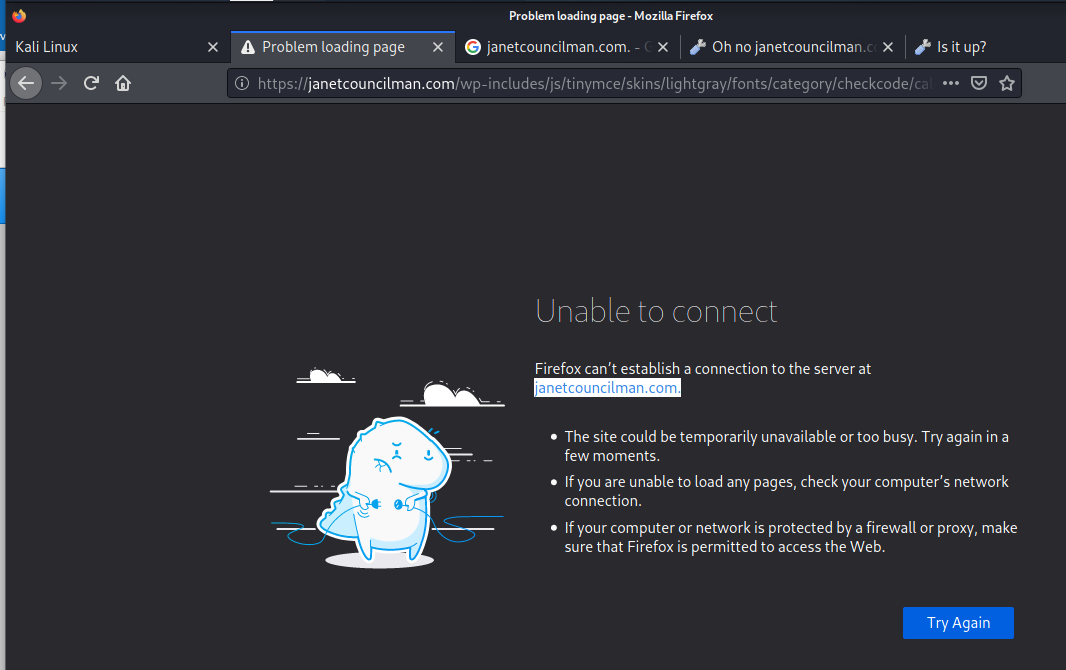
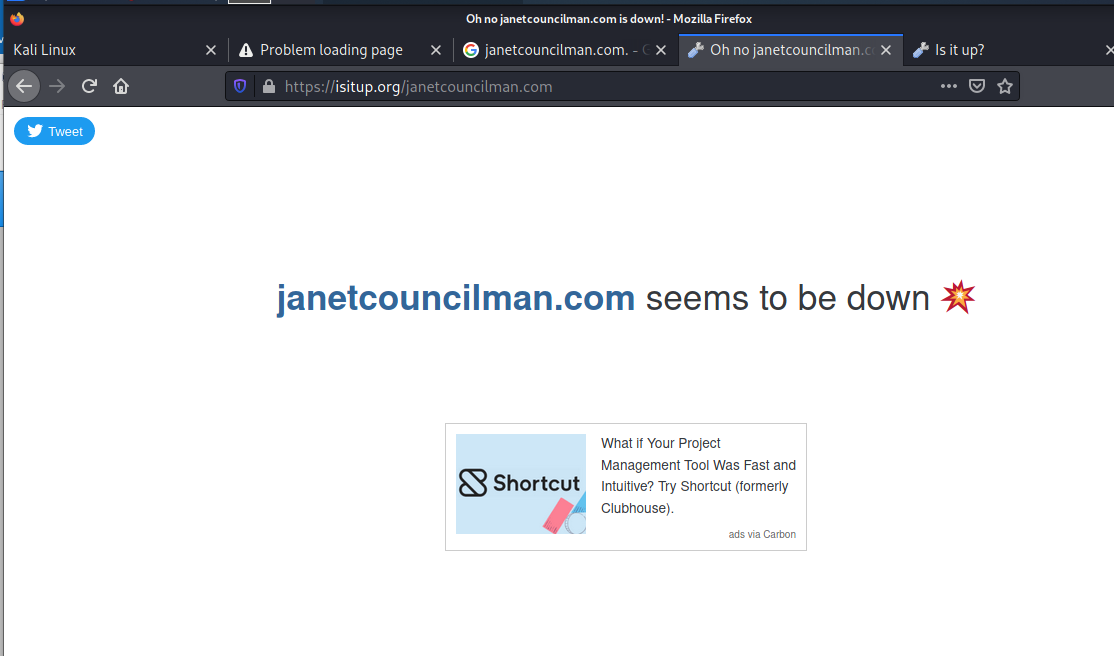
The plot thickens. This destination looks like Janet Councilman had her website hijacked. This location is pretty typical for hosting phishing landing pages. So I opened Kali and tried to look for this exploit’s pages, But it was not to be.
This sort of error page usually indicates that the hijacked site was already taken down, and is undoubtedly being cleaned, or restored from a backup copy. So who is Janet Councilman?
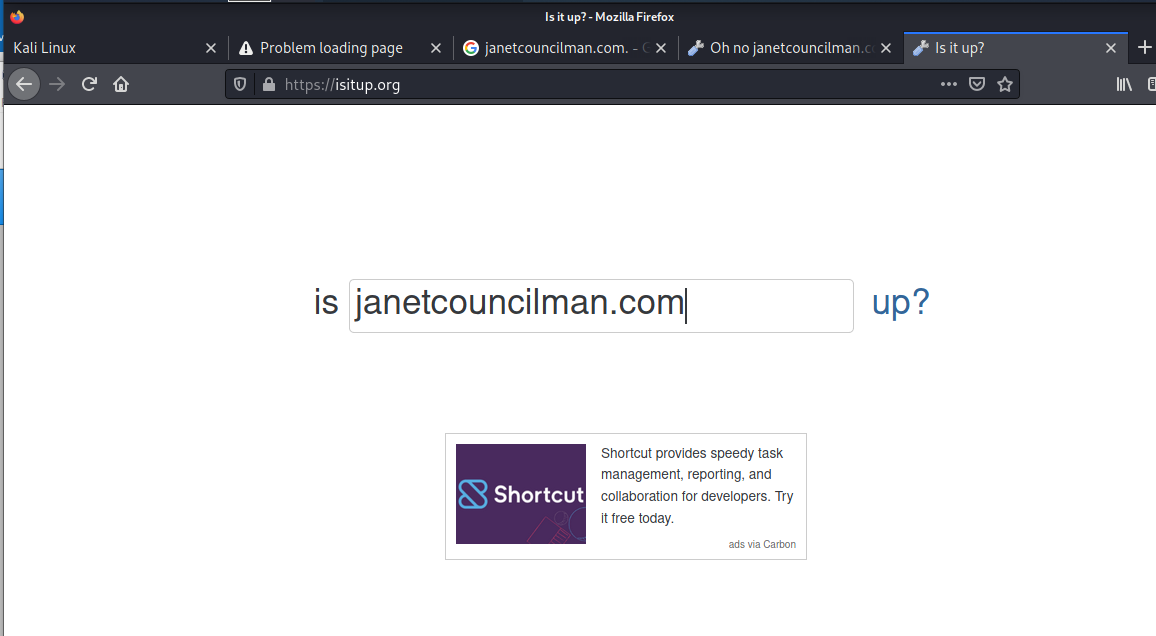
Janet is the author of children’s books. I wanted to know if her website was really down, so it checked that out on isitup.org.
And the result showed the site to be down.
Bit.ly link emails are designed to appeal to our natural curiosity in order to get us to click on the link. Since there is no other information than the link and the name of the sender, i am led to the conclusion that the pages probably contained so sort of malware download, instead of the usual credential stealing page.
I know many business entities ban shortened URLs from any source in order to prevent attacks on their networks. This is a good policy for the rest of us. Do not click on Bit.ly links or other shortened links.
Later tonight or tomorrow I will check to see if janetcouncilman.com has returned to the Internet.
Four days later this website is still down, and its reputation has been compromised. Not a good sign for Janet Councilman.
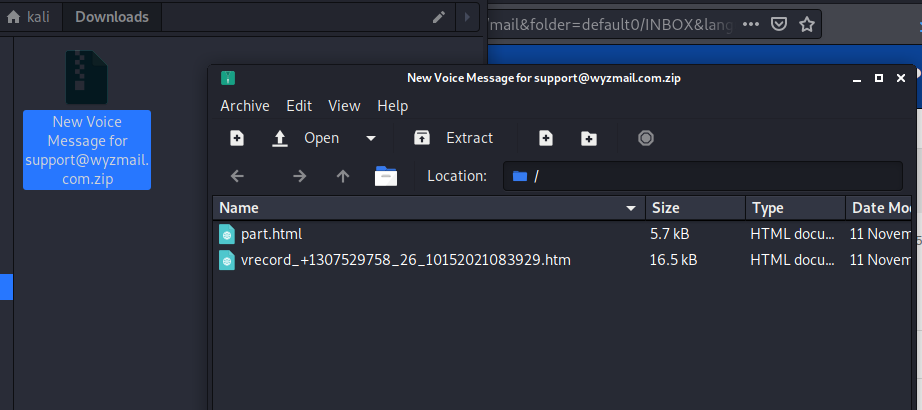
Voice Message Phish
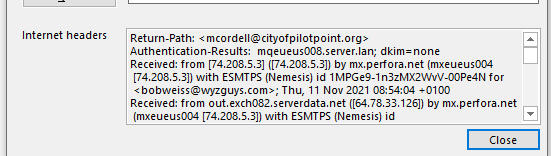
This credential stealer uses the popular webpage as an attachment technique. The sender is evidently a hijacked email account for the small Texas city of Pilot Point. Here’s the email:
The email headers shows the source was an exchange server at 64.78.33.126, which is Sunnyvale CA. Evidently a cloud-based email server.
The attachment contained the landing page for this exploit.
And here is the credential stealing landing page
Multi-Stage Vishing Attacks Are Coming to an Inbox Near You
I have seen a lot of these attacks over the last few months, and reported them on earlier episodes of Friday Phish Fry.
New attacks initially coming in via email are directing victims to make phone calls to attacker-controlled call centers in order to provide banking and credit card details.
I’ve brought these kind of phishing-turned-vishing attacks to your attention previously with examples of fake Amazon password resets or fake orders for expensive items – both pointing recipients to call phone numbers. But new examples of these kinds of increasingly frequent attacks are coming to light.
Rather than sending an email referencing an invoice attachment (usually for the purposes of installing malware), these scams simply use the email as the invoice or payment notice and drive readers towards calling a phone number to dispute the charge.
These scams are intent on getting recipients to divulge their credit card or banking details – all in the name of “getting you a refund”.
Once again, this very-much unsolicited email should raise a red flag with anyone that receives it, erring on the side of “this is utter garbage” instead of “Oh my! I don’t owe that!” (which is exactly what the scammers want.)
Security awareness training is your secret weapon to train your users to stay in that ever-vigilant mode when interacting with email and the web. Instead of taking everything at face value and believe it by default, your users will interact with unfamiliar content far more skeptically and are less likely to become victims.
Blog post with links and example screenshot:
https://blog.knowbe4.com/multi-stage-vishing-attacks-are-coming-to-an-inbox-near-you
Hoax Email Blast Abused Poor Coding in FBI Website
The Federal Bureau of Investigation (FBI) confirmed today that its fbi.gov domain name and Internet address were used to blast out thousands of fake emails about a cybercrime investigation. According to an interview with the person who claimed responsibility for the hoax, the spam messages were sent by abusing insecure code in an FBI online portal designed to share information with state and local law enforcement authorities.
Share
NOV










About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com