 Phishing Email Alerts
Phishing Email Alerts
Catch of the Day: Email Issue Phish
Chef’s Special: Payment Failed Phish
Examples of clever phish that made it past my spam filters and into my inbox. Some are sent by clients or readers like you, and other reliable sources on the Internet.
You can send phishing samples to me at phish@wyzguys.com.
My intention is to provide a warning and show current examples of phishing scams, related articles, and education about how these scams and exploits work, and how to detect them in your inbox. If the pictures are too small or extend off the page, double clicking the image will display them in a photo viewer app.
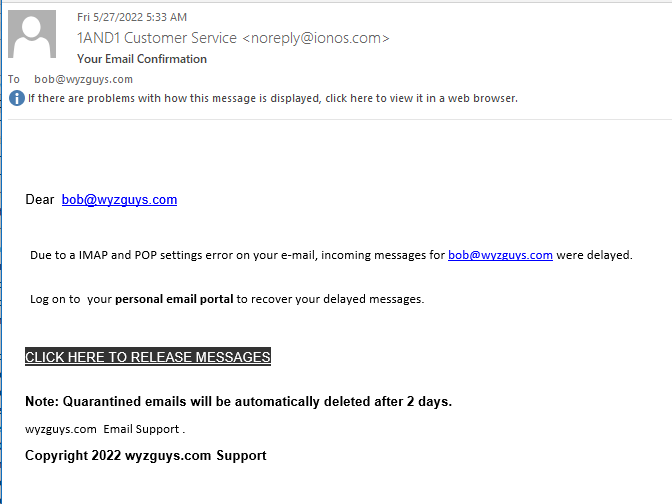
IONOS Email Issue Phish
We’ve seen and shown this sort of credential-stealing phishing exploit before, but here’s a refresher for you.
The Phish:
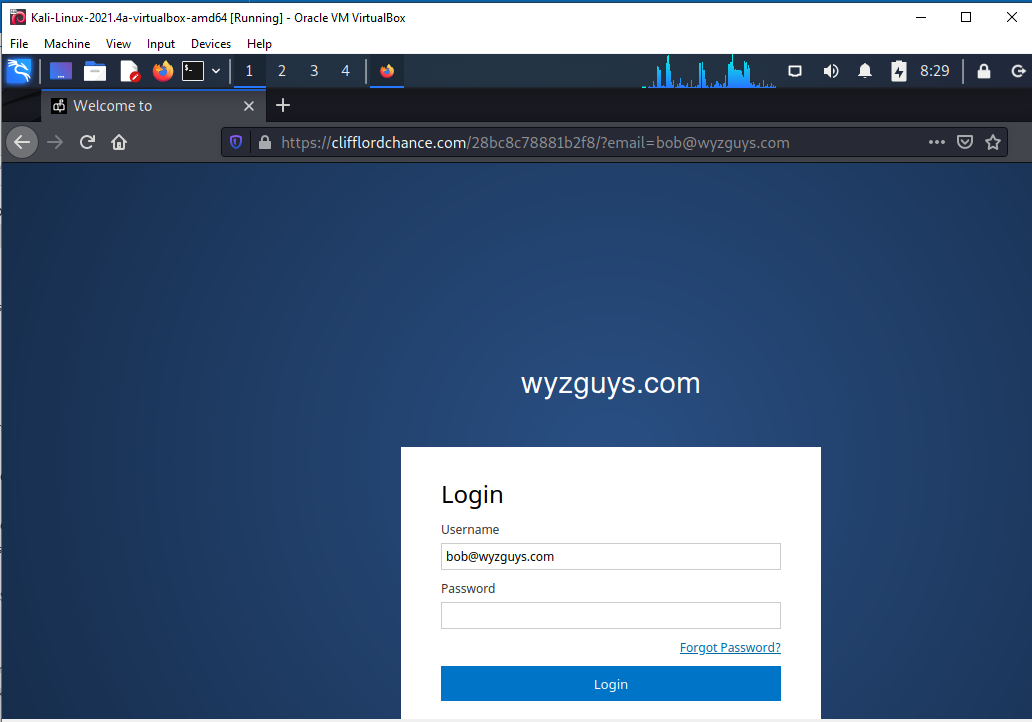
The button link resolves to https://clifflordchance.com/28bc8c78881b2f8/?email=bob@wyzguys.com
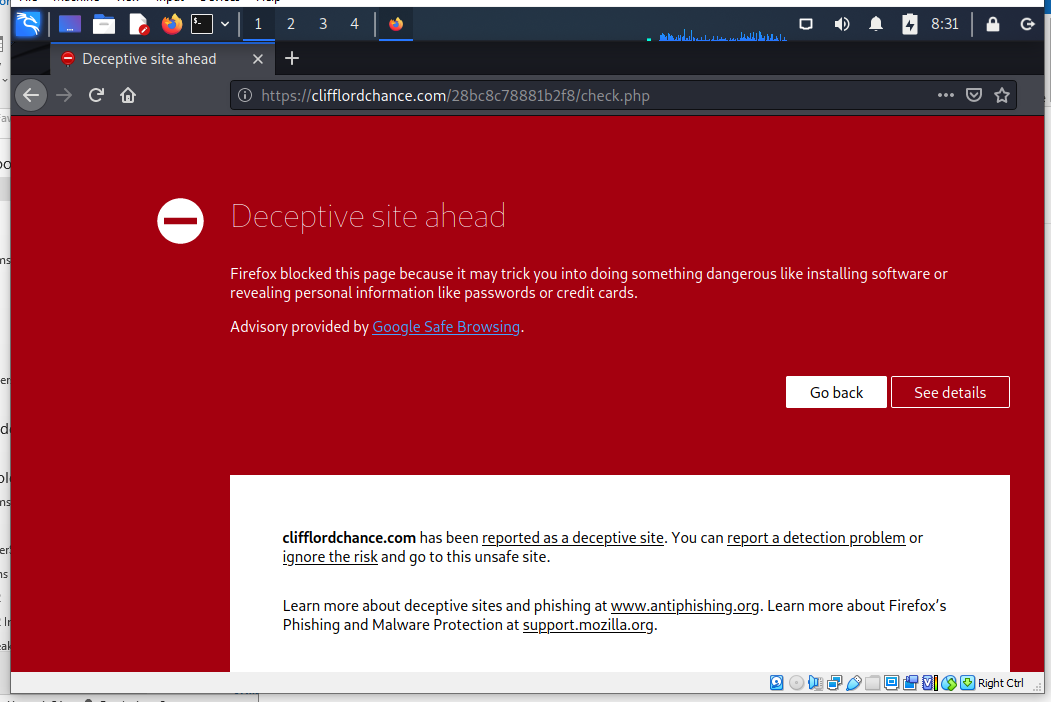
Entering a fake password took me here. Of course I ignored the warning
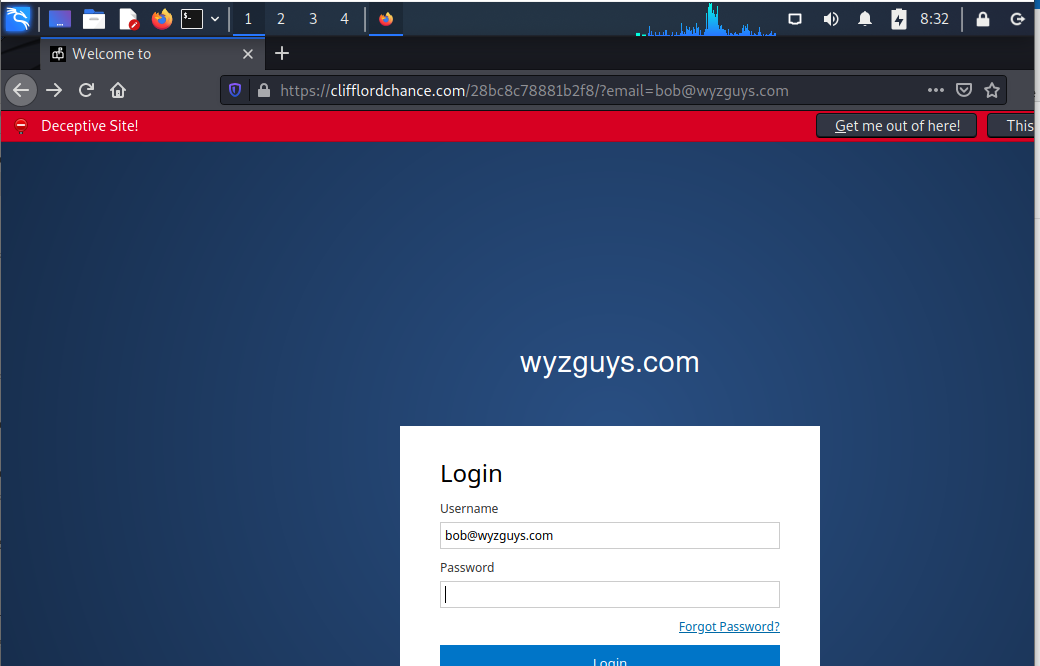
Weirdly enough this looped me back t the login form.
The reason cyber-crooks keep using these oldy-but-goody exploits is because there are always plenty of people who fall for them. Don’t let it be you.
Payment Failed Phish
This email appeared to come from a hosting company name Hostinger, and said that my credit or debit card failed to pay an invoice for a domain name renewal.
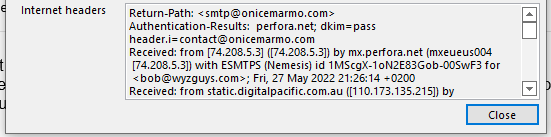
The email headers showed that the source was a mail server in Australia. The domain onicemarmo.com used for the sender address has been registered since 2008, so the email domain was spoofed, or has been hijacked.
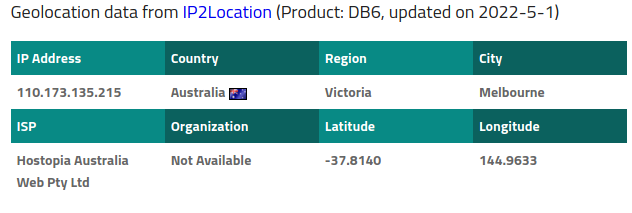
IP locator information shows the email orginating from Hostopia Austrailia, Melbourne.
The link 5976037 and the link for MyWix both resolved to http://mywyzguys.com-santa.evoluesystem.com/Enat-Hosingir?phish@wyzguys.com. I got this warning from Cisco Umbrella. Not sure where this warning is originating, it may be something new from my ISP.
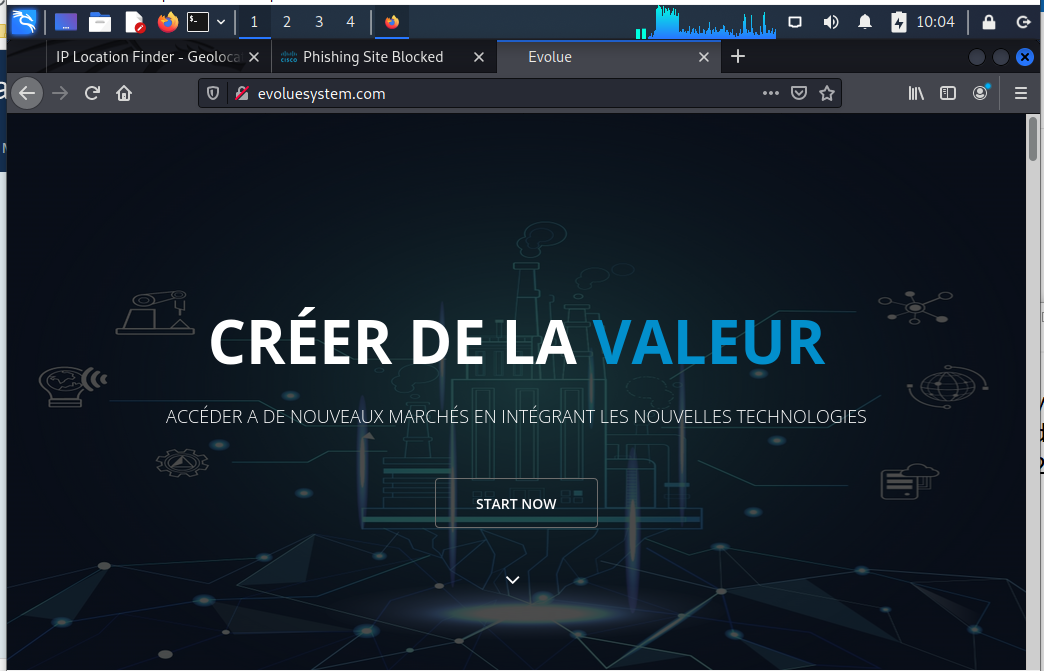
When I tested to domain root evoluesystem.com, I got the home page of a French cosmetics company. Evidently, their website was hijacked and being used to host the landing page I was unable to get to previously.
If I had to guess, and I am, it looks like this exploit is designed to get the victim to make a fake payment. The credit card information would then be in the hands of the cyber-criminals. Possibly some credentials as well.
Resist the urge to make these sorts of payments before you take time to check them out directly, without using the provided links.
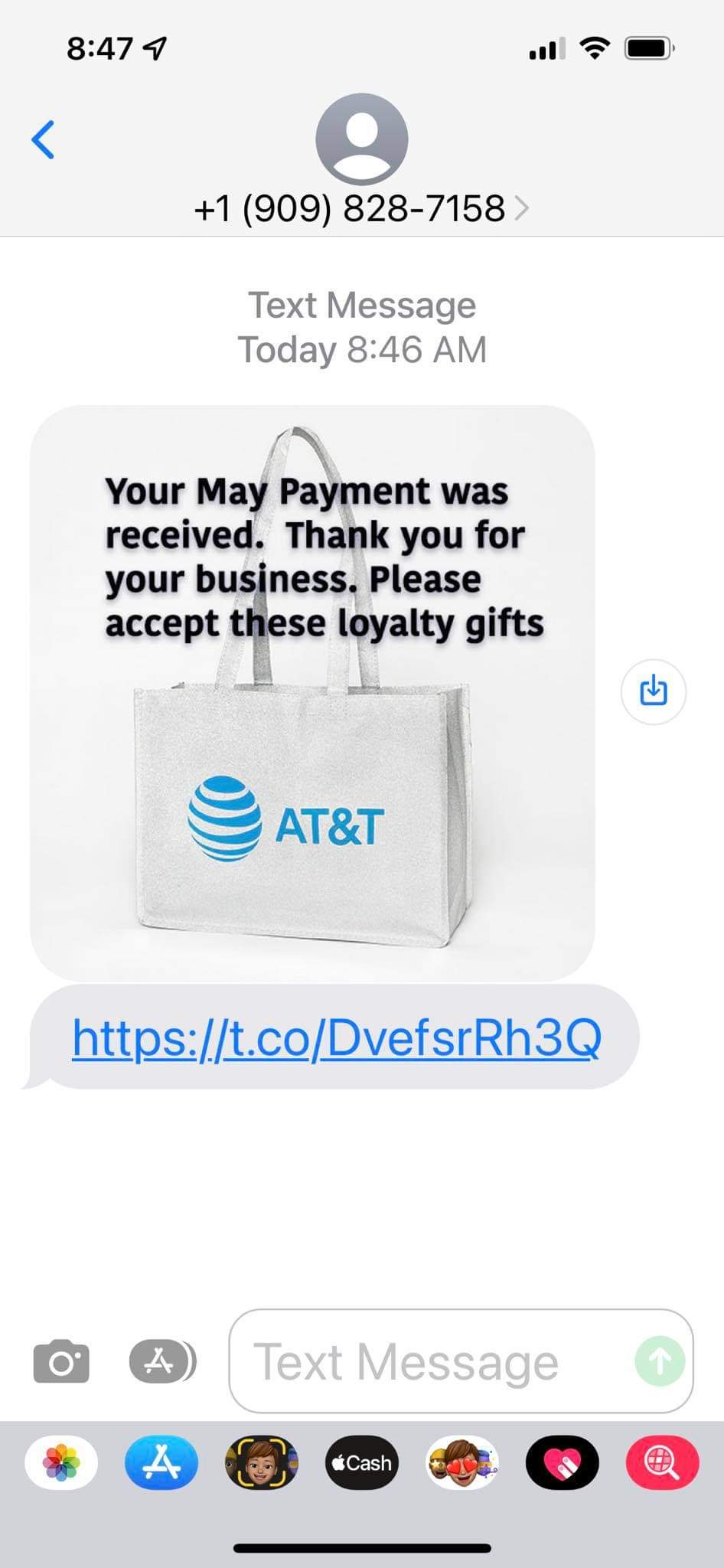
ATT Smish
Here is one that came from a Facebook Friend. This, and other variations are scams.
Voice phishing attacks reach all-time high
A study conducted by Agari and PhishLabs found a five-times increase in attempted vishing attacks from the beginning of 2021 to Q1 of 2022.
Cases of voice phishing or vishing have been reported to have risen a whopping 550% over the past 12 months alone, according to the Quarterly Threat Trends & Intelligence Report co-authored by Agari and PhishLabs. In March 2022, the amount of vishing attacks experienced by organizations reached its highest level ever reported, passing the previous record set in September of 2021.
As part of the study, it was found that the two companies had “detected and mitigated hundreds of thousands of phishing, social media, email, and dark web threats targeting a broad range of enterprises and brands”.
“Hybrid vishing campaigns continue to generate stunning numbers, representing 26.1% of total share in volume so far in 2022,” said John LaCour, principal strategist at HelpSystems. “We are seeing an increase in threat actors moving away from standard voice phishing campaigns to initiating multi-stage malicious email attacks. In these campaigns, actors use a callback number within the body of the email as a lure, then rely on social engineering and impersonation to trick the victim into calling and interacting with a fake representative.” More…
Beware the Smish! Home delivery scams with a professional feel…
Home delivery scams are getting leaner, and meaner, and more likely to “look about right”. Here’s an example to show you what we mean…
Share
JUN






About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com