Phishing Email Alerts
Catch of the Day: Forwarded Phish
Chef’s Special: Cyrillic Phish
Examples of clever phish that made it past my spam filters and into my Inbox, or from clients, or reliable sources on the Internet.
I would be delighted to accept suspicious phishing examples from you. Please forward your email to phish@wyzguys.com.
My intention is to provide a warning, examples of current phishing scams, related articles, and education about how these scams and exploits work, and how to detect them in your own inbox. If the pictures are too small or extend off the page, double-clicking on them will open them up in a photo viewer app.
Forwarded Email Attachment
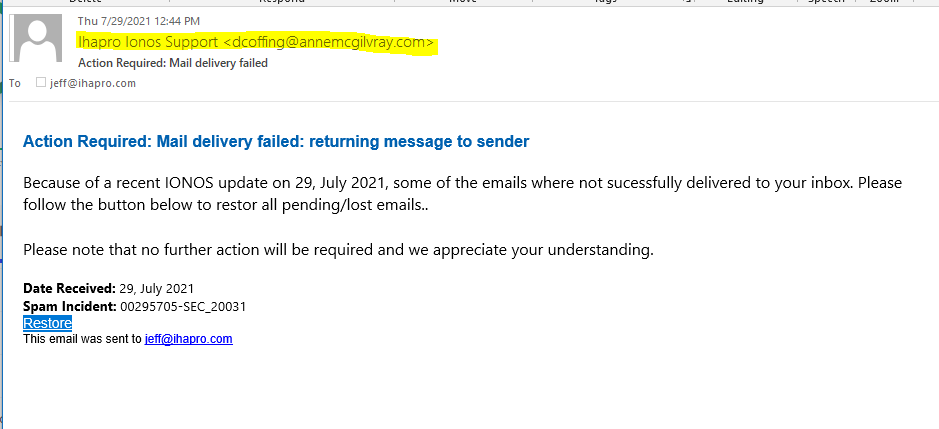
A suspicious email was send to me as an email attachment by a reader named Jeff Larkin. What was especially nice is that the email was sent as a .MSG attachment, instead of just a forward. This left all the links on the original email active for investigation, as well as the email headers. Here is the email Jeff sent to me.
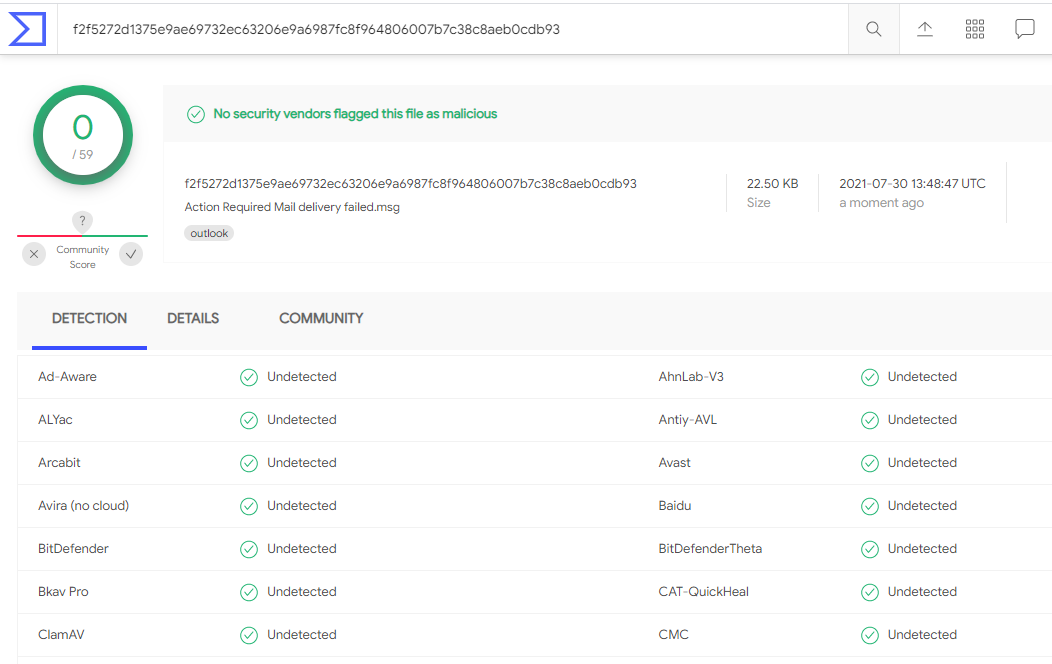
I wanted to open the attachment in Kali, but I did not have a suitable email client on my VM (Thunderbird?). So I tested the attachment using VirusTotal, and it came back as clean.
So I opened it normally in Windows. And here is what Jeff was sent, and then passed on to me.
The email headers showed that the email was send by dcoffing@annemcgilvray.com, which is probably a hijacked email account.
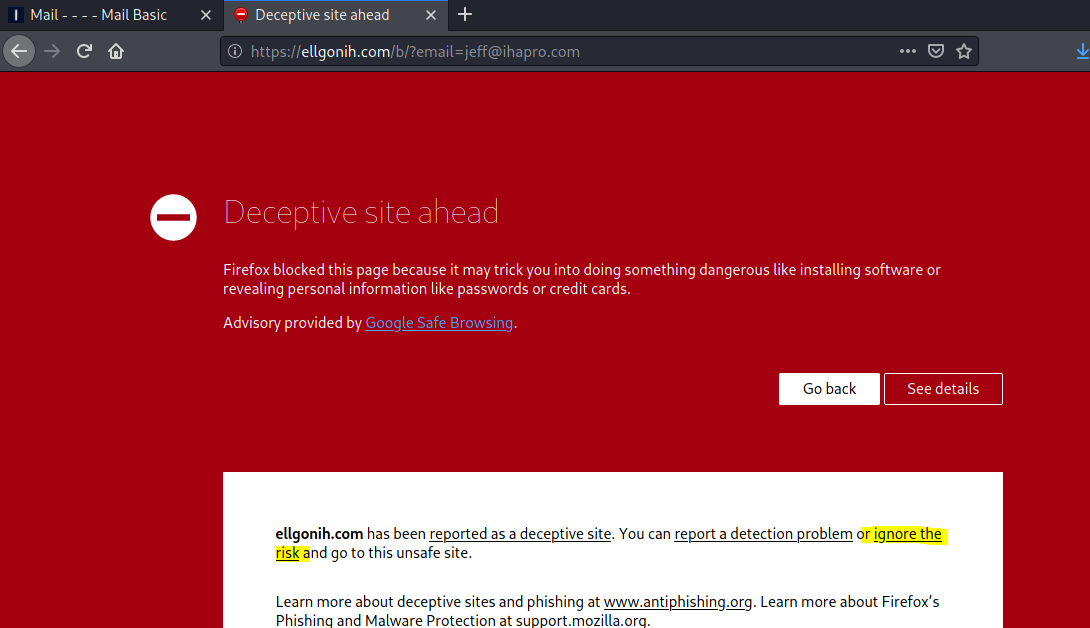
The Restore link resolved to https://ellgonih.com/b/?email=jeff@ihapro.com which redirected to https://ellgonih.com/b/login/?id=2327&utm_term=2327&utm_campaign=mail&utm_medium=inbox&utm_source=login_frontend_hosting&utm_err=0
The Firefox browser in Kali first identified this web site as deceptive but i went ahead and ignored this risk. Don’t do this at home, smart people stay behind the red warning window.
This finally got me to the actual landing page, which of course turned out to be a credential stealing page targeting his email account credentials.
Cyrillic Letters Phish
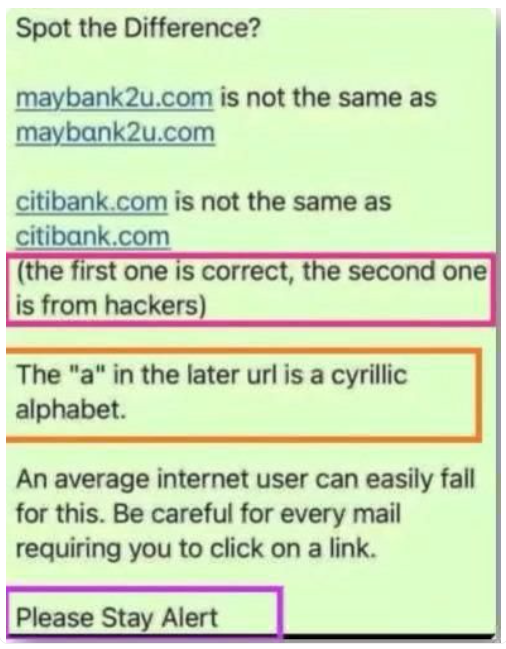
One way to register look-a-like domains to make URLs look more authentic is by swapping in a few letters from other alphabet sets, such as Greek or Cyrillic. Check out the attached image. Compare the letter “a” in both URLs. Could you spot this trick?
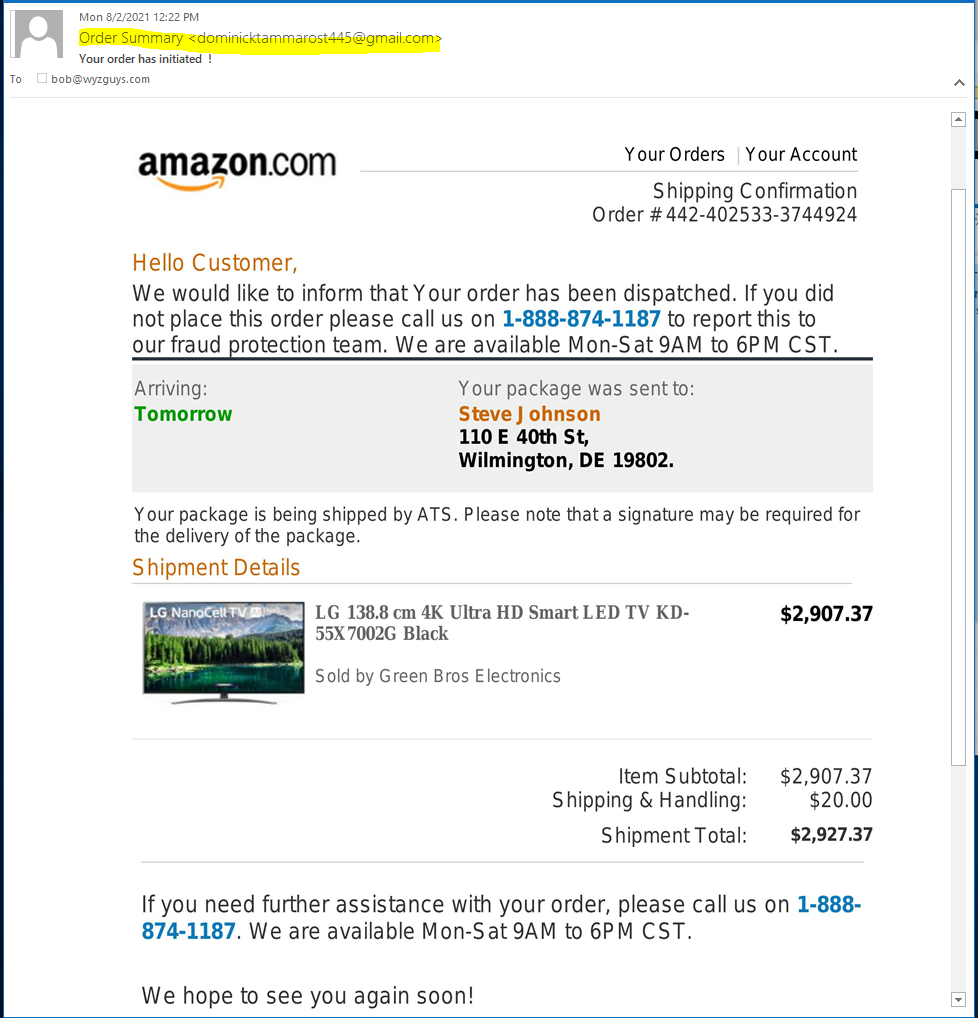
Amazon Order Phish
Is this a phish or is it a vish? This hybrid exploit starts as an email. informing you that some guy names Steve J ohnson (notice extra space between J and ohnson) is getting a $2000 TV from your Amazon account. Only the email did not come from Amazon, and the friendly help desk number is bogus, and the help desk personnel are probably just after your personal and credit card information. Do not fall for scams like these.
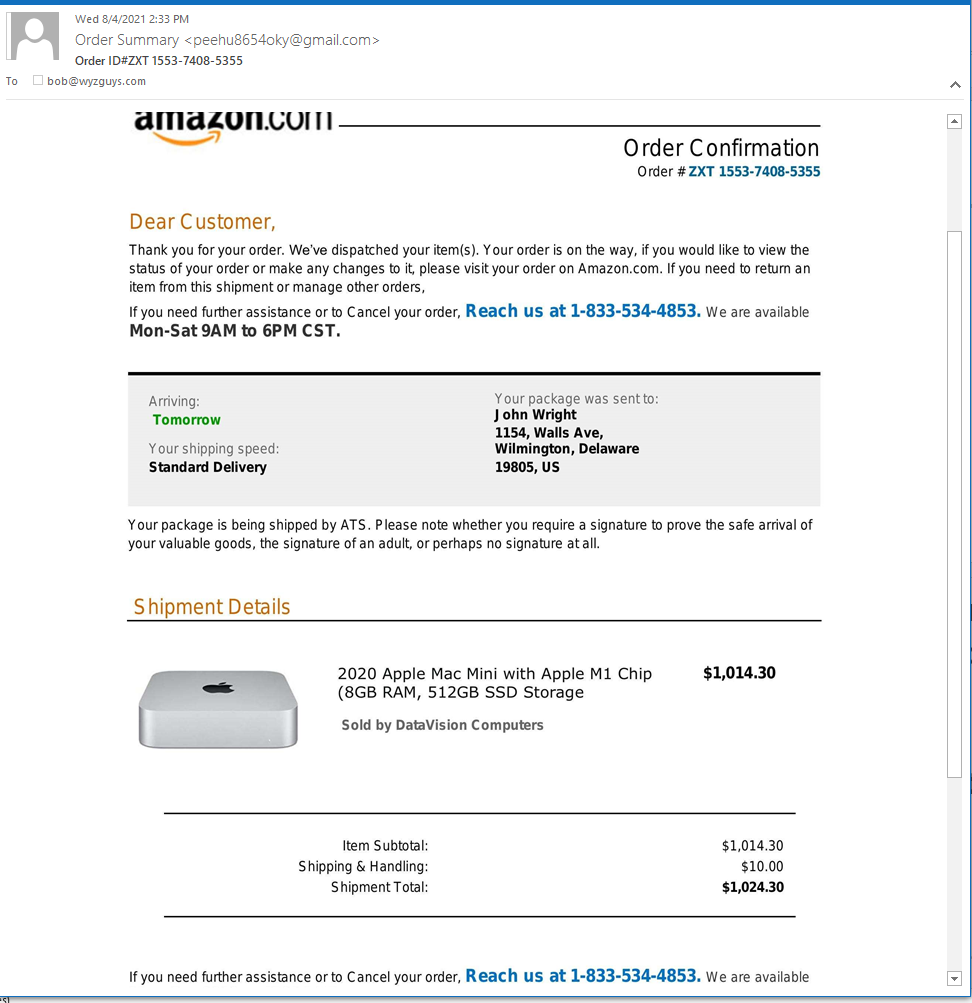
An Another From Amazon
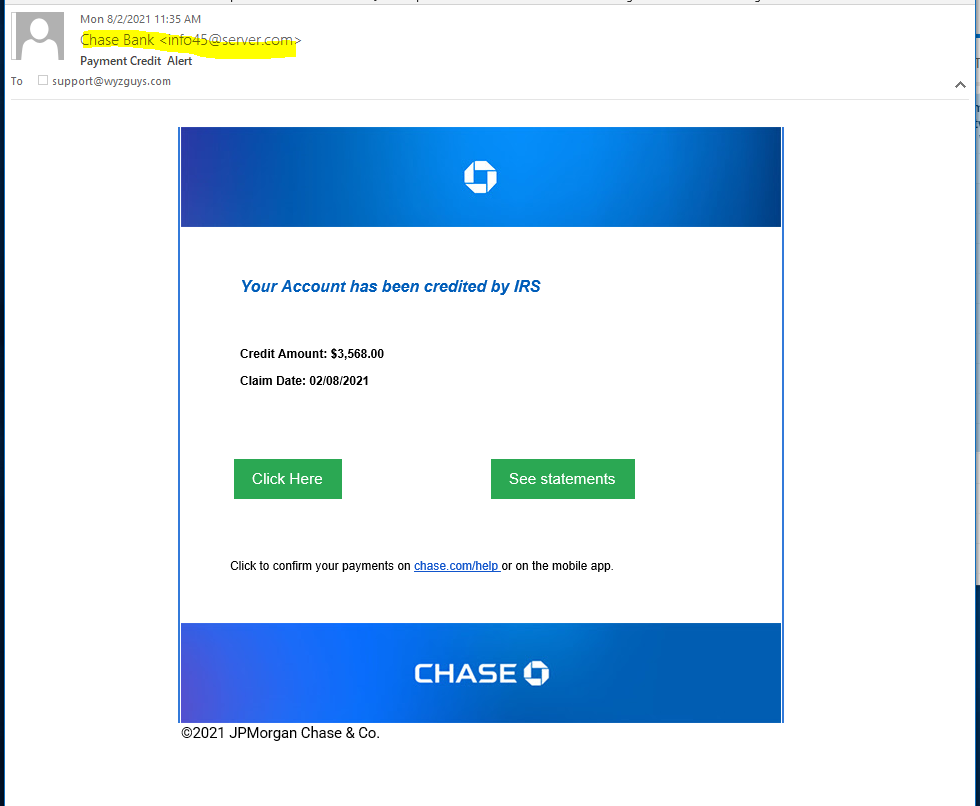
Chase IRS Deposit Phish
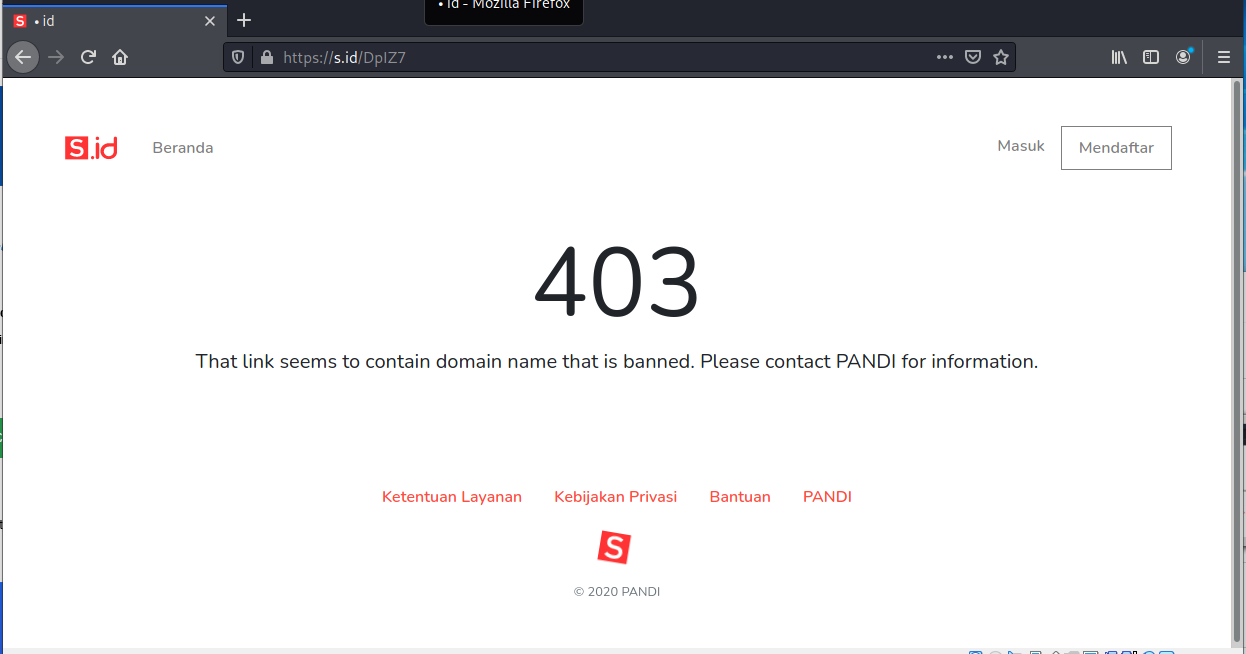
I wasn’t able to investigate this email until 8-3-2021, and in that span of 24 hours the landing site had evidently been taken down. This email looks like especially good news, a refund of $3500 from the IRS. But the email was sent from a dodgy domain (server.com?) and the three links CLick Here, See Statements and chase.com/help all resolved to https://s.id/DpIZ7.
Virustotal had nothing on the URL and the landing page was gone and replaced by a 403 page.
Even good news needs a grain of salt or two.
Image Inversion as a New Phishing Technique
Researchers at WMC Global have found that a phishing kit is using images with inverted colors to avoid detection.
“PhishFeed analysts recently discovered a novel way some threat actors are tricking these scanning engines, and this avoidance mechanism in particular has been deployed on multiple Office 365 credential phishing websites,” the researchers write. “WMC Global threat analysts attribute the use of this method to a single threat actor selling the phishing kit to multiple users.”
Many security scanners and web crawlers are able to identify phishing pages by their appearance. If a site appears identical to the Office 365 login portal but doesn’t have an Office 365 domain, then the scanner concludes that it’s likely a phishing page.
“Because image recognition software is improving and becoming more accurate, this new technique aims to deceive scanning engines by inverting the colors of the image, causing the image hash to differ from the original,” the researchers write. “This technique can hinder the software’s ability to flag this image altogether.
However, a victim visiting the website would likely recognize that the inverted picture is illegitimate and exit the website. As a result, the threat actor has stored the inverted image and, within the index[dot]php code, has used a CSS method to revert the color of the image to its original state.”
The researchers conclude that this is a simple but effective way to deploy a convincing phishing page while avoiding detection.
“This approach results in the final website’s appearing legitimate to users who visit, while crawlers and scanning engines are highly unlikely to detect the image as being an inverted copy of the Office365 background,” the researchers write. “It is notable that the inverted image was discovered within a deployed Office 365 credential phishing kit.
Blog Post with links:
https://blog.knowbe4.com/image-inversion-as-a-phishing-technique
BazarCaller – the malware gang that talks you into infecting yourself
Vishing exploits are on the rise. Calling someone back feels safer than clicking an unknown link… but it isn’t! Remind your friends and family.
ShareAUG







About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com