 Phishing Email Alerts
Phishing Email Alerts
Catch of the Day: Google Search Fails Again
Chef’s Special: Sophos Phishing Top Ten
Examples of clever phish that made it past my spam filters and into my Inbox, or from clients, or reliable sources on the Internet.
I would be delighted to accept suspicious phishing examples from you. Please forward your email to phish@wyzguys.com.
My intention is to provide a warning, examples of current phishing scams, related articles, and education about how these scams and exploits work, and how to detect them in your own inbox. If the pictures are too small or extend off the page, double-clicking on them will open them up in a photo viewer app.
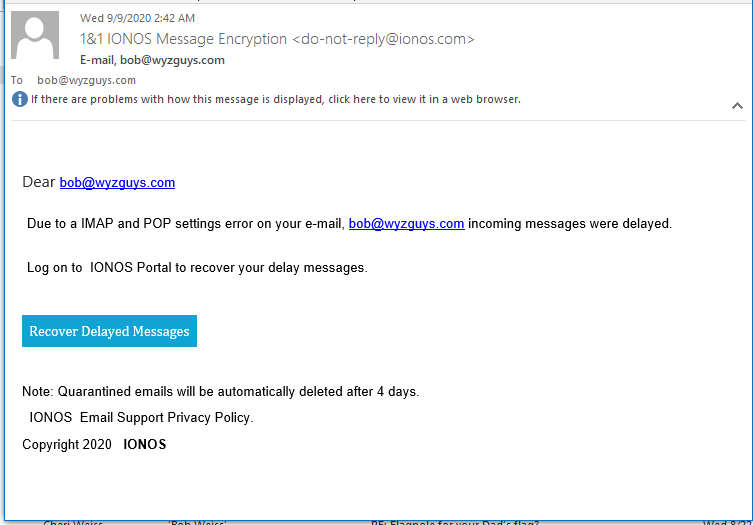
Another Credential Stealing Phish
I guess one of the benefits of publishing articles unmasking the Phishing Business is that the phisherphoke (new term that I maybe coined – fisherfolk = phisherphoke) seem to have given up sending me phishinig emails. This is the first one I’ve received in 5 days. And oh, so familiar.
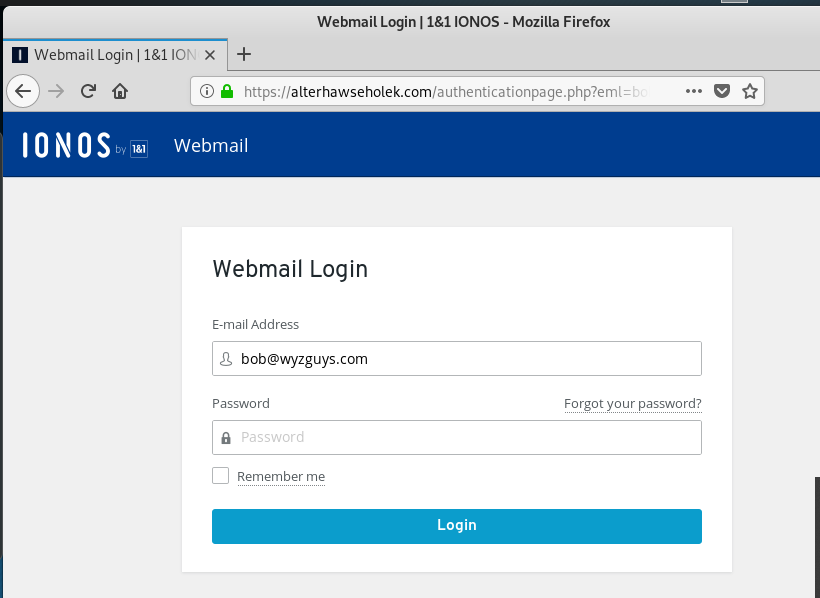
This email has a link with resolves to https://alterhawseholek.com/authenticationpage.php? It is another simple credential stealing web page on what appears to be a hijacked web site. The website is gone, or perhaps it never existed. VirusTotal detected nothing for the URL .
 Google Search Fails Again: Recent Black Hat SEO Attacks Lead To Malware And Porn
Google Search Fails Again: Recent Black Hat SEO Attacks Lead To Malware And Porn
This article on Forbes by David Balaban gives an excellent overview about how the malicious links to legitimate sites and the dodgy redirects to credential stealing forms and drive-by malware downloads work. This supports what I have been explaining in the Friday Phish Fry.
David will be our featured guest blogger on Wednesday Sept 21. His article, Apple Phishing Is an Escalating Threat will focus on Apple phishing exploits, and why Apple’s vaunted built-in security won’t protect you from these attacks.
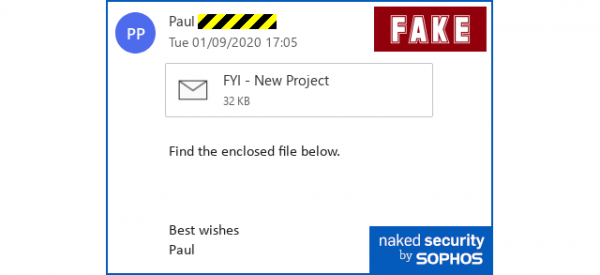
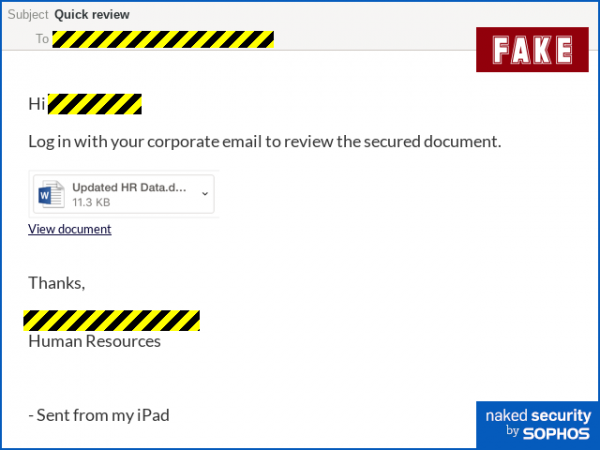
Phishing tricks – the Top Ten Treacheries of 2020
From Sophos – Here’s the Top Ten phishing tricks of the year, so far – or perhaps we mean The Worst Ten. How many would you fall for? Read entire article here. See examples below. Categories include:
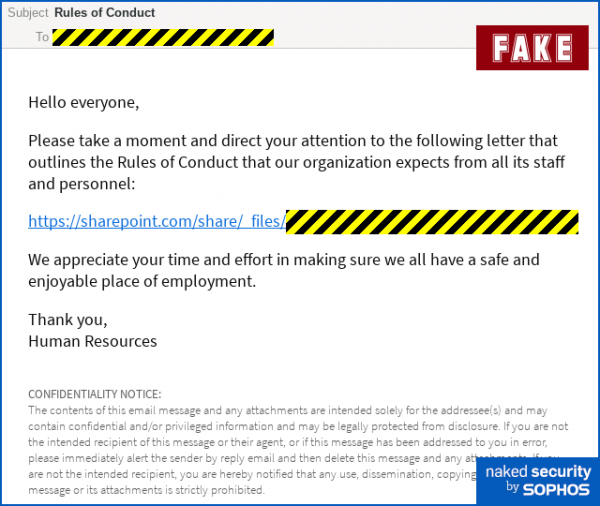
- Rules of Conduct email
- Delayed tax summary
- Scheduled server maintenance
- Task assignment
- Email system test
- Vacation policy update
- Car lights on
- Delivery failure
- Secure document
- Social media message
Phishing scam uses Sharepoint and One Note to go after passwords
Not all phishing links appear right in the email itself…
Organizations facing nearly 1,200 phishing attacks each month
A new study found that email phishing attacks have become more successful during the COVID-19 pandemic.
Vishing scams use Amazon and Prime as lures – don’t get caught!
How do you deal with scam calls on a phone number you keep for emergencies? Here are two examples. Click on the link above for the entire article.
Your Amazon order for [several hundred pounds ending in -99] has now been processed. Your [phone product] will soon be dispatched and you should receive it in [a small number] of days. For further information or to cancel the order, press 1 now to speak to an operator.
Your Amazon Prime subscription will auto-renew. Your card will be billed for [several tens of pounds ending in -.99]. To cancel your subscription or to discuss this renewal, press 1 now.
[Heads Up] How to Check Your Email Rules for Maliciousness. Do This Now.
This article is more about steps to an email account hijack or business email compromise (BEC). It explains one of the many things that an attacker can do with credentials they stole using a phishing exploit.
Roger Grimes wrote: “Email rules have been used maliciously for decades. Learn about email rules and what you need to do to defend your organization against their malicious misuse.”
Email Rules
Attackers have always been adept at using legitimate automation tools and features against us. The time-worn programmer’s credo, “Why do something manually when you can automate it?” apparently applies to malware writers as well.
Automating maliciousness makes it more effective in terms of both success, lower cost, and it makes the attacker far less likely to be caught. For decades, phishers and other attackers have used email automation functionality, such as rules, scripts, add-ons, templates, and configuration settings, against their victims. Read more…
Fake Phone and Other Device Alerts
Thanks to Sophos for advising us about these sorts of attacks. Please click through to their article to see all the examples. I’ve put one or two below.
How to “crack” Apple’s vaunted built-in security? Trick and Apple user. People are always the weakest link of the security chain.
ShareSEP







About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com