Phishing Email Alerts
Catch of the Day: Norton Renewal Phish with Vishing Sauce
Chef’s Special: Loan Phish
Examples of clever phish that made it past my spam filters and into my Inbox, or from clients, or reliable sources on the Internet.
I would be delighted to accept suspicious phishing examples from you. Please forward your email to phish@wyzguys.com.
My intention is to provide a warning, examples of current phishing scams, related articles, and education about how these scams and exploits work, and how to detect them in your own inbox. If the pictures are too small or extend off the page, double-clicking on them will open them up in a photo viewer app.
Phishing + Vishing + Social Engineering
Many of this week’s Phish Fry combine a phishing email, a toll free phone call, and some convincing live social engineering. By pivoting in new directions, and combining exploits methods, the phishers hope to keep their exploits fresh, believable, and successful.
Norton Renewal Phish with Vishing Sauce
This is a simple enough exploit. The phishing email is designed to agitate the recipient. ($39.98 was “successfully renewed” after all) This is designed to trick the recipient into calling the “BIllingTeam” (their quotes, not mine) where with some additional tricks, lies, and social engineering. The goal for this exploit is to actually get paid, get a credit card number, and perhaps collect some personal information, as well. Here’s the email. If you call the toll free number, let me know how it went.
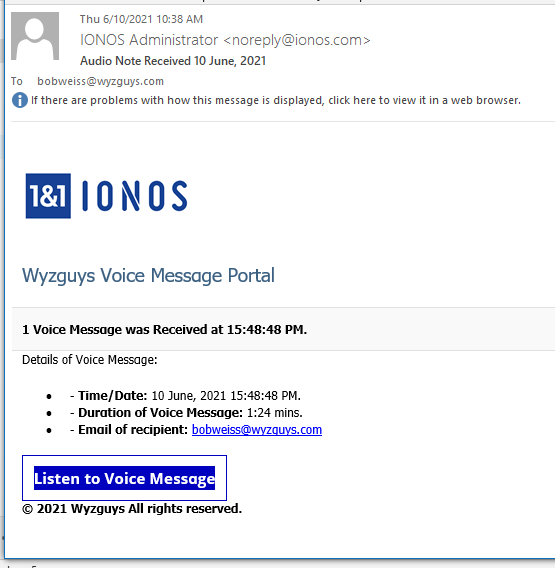
Voice Message Phish
We have seen a variant of this phishing email before. Unfortunately, by the time I was able to analyze this exploit, the landing page had already been taken down.
The source email address is nicely spoofed to appear to be coming from IONOS.
The email headers showed the email originated at walcarius.com.
Return-Path: <noreply@ionos.com>
Received: from mail.walcarius.com ([81.244.246.138]) by mx.perfora.net
(mxeueus003 [74.208.5.3]) with ESMTPS (Nemesis) id 1M6VF7-1lyEgD1N7J-006xul
for <bobweiss@wyzguys.com>; Thu, 10 Jun 2021 17:49:15 +0200
Received: from localhost (localhost [127.0.0.1])
by mail.walcarius.com (Postfix) with ESMTP id 82CD140617
for <bobweiss@wyzguys.com>; Thu, 10 Jun 2021 17:37:55 +0200 (CEST)
Received: from mail.walcarius.com ([127.0.0.1])
by localhost (zimbra.int.walcarius.com [127.0.0.1]) (amavisd-new, port 10032)
with ESMTP id vgKeYXhwdb3u for <bobweiss@wyzguys.com>;
Thu, 10 Jun 2021 17:37:47 +0200 (CEST)
Received: from localhost (localhost [127.0.0.1])
by mail.walcarius.com (Postfix) with ESMTP id 522BB40608
for <bobweiss@wyzguys.com>; Thu, 10 Jun 2021 17:37:45 +0200 (CEST)
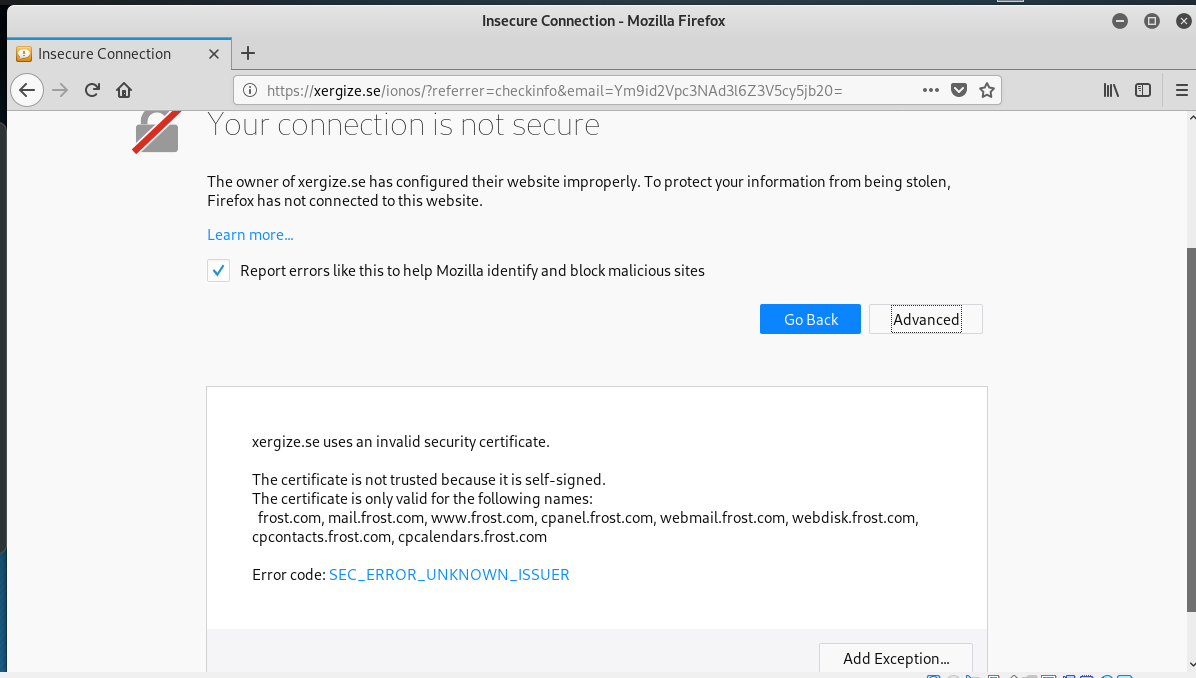
The button link resolved to https://xergize.se/ionos/?referrer=checkinfo&email=Ym9id2Vpc3NAd3l6Z3V5cy5jb20= The Firefox browser on my Kali VM warned of a digital certificate problem,
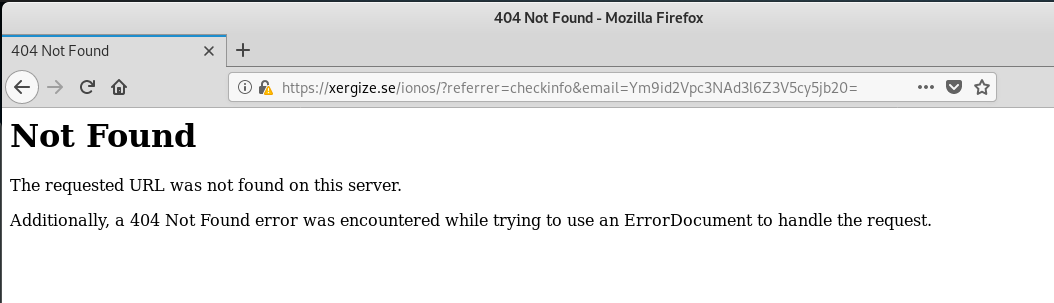
Pushing through, I was greeted by a 404 Not Found page.
This illustrates how quickly that the various security teams and security companies can disable or take down an exploit. The lesson is to be aware of browser warnings or 404 error messages, as these can indicate the possibility of an exploit.
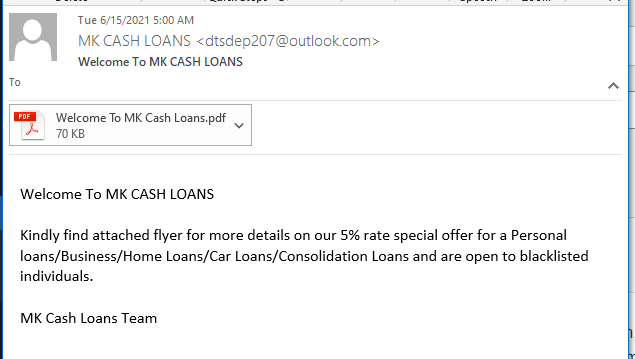
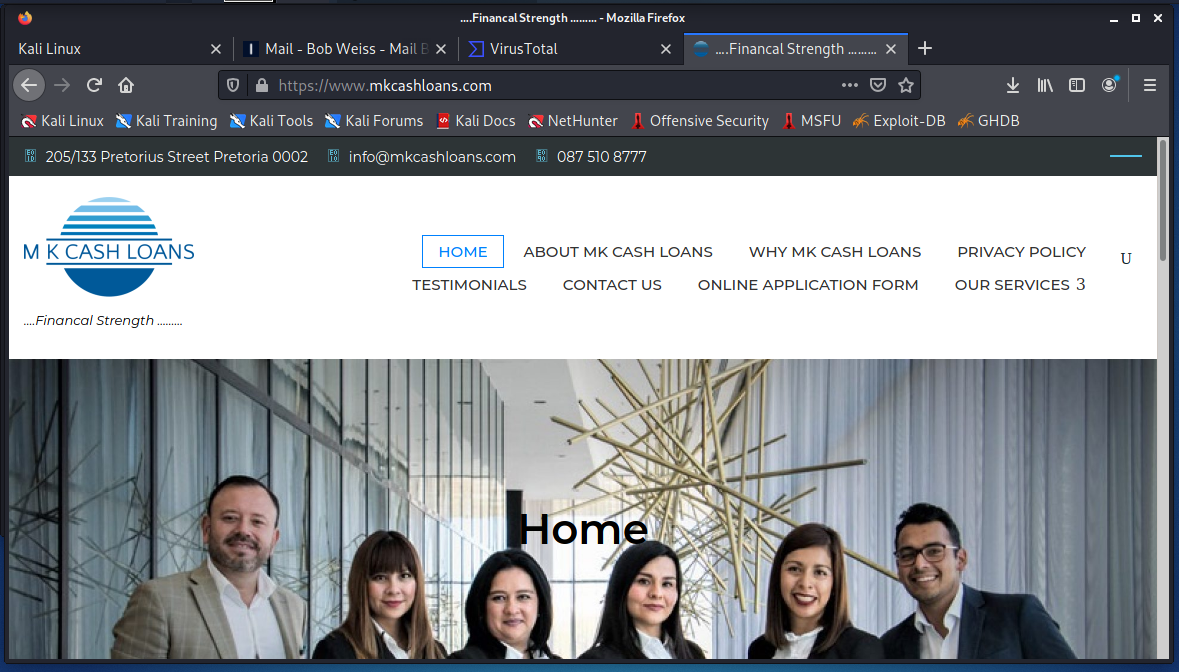
Loan Phish
There are a lot of angles to this loan solicitation phish. Everything appears to be legitimate, asside from the sender’s Outlook,com email address.
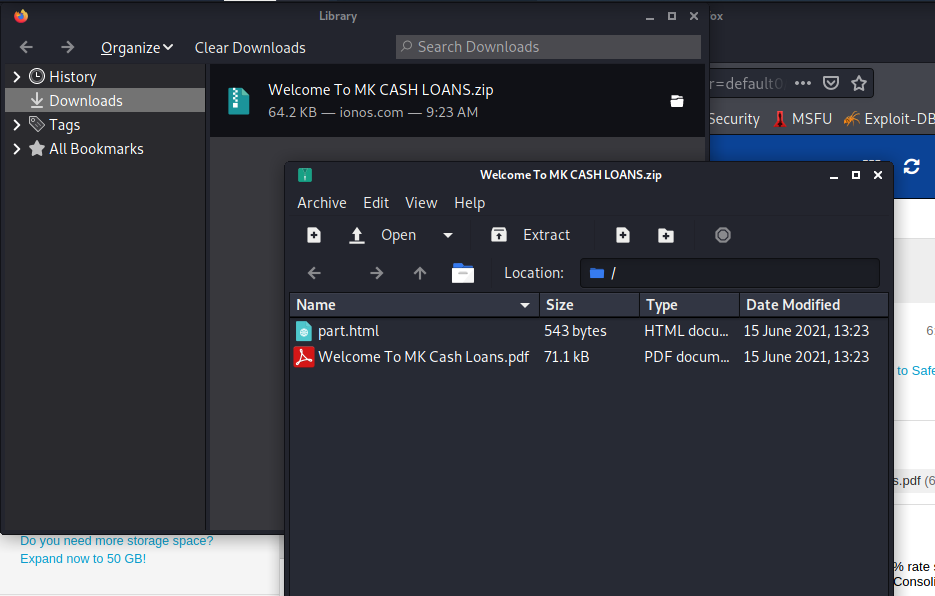
The first think I checked was the PDF file attachment. I downloaded and opened it using my Kali VM. By the way, I just upgraded the Kali experience from the 2019 version to the 2021 version, so the appearance is different.
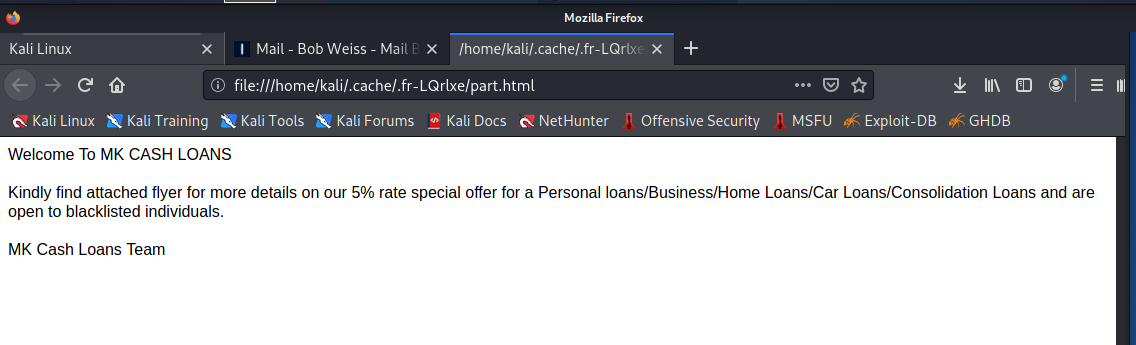
The HTML attachment was just a copy of the email message body.
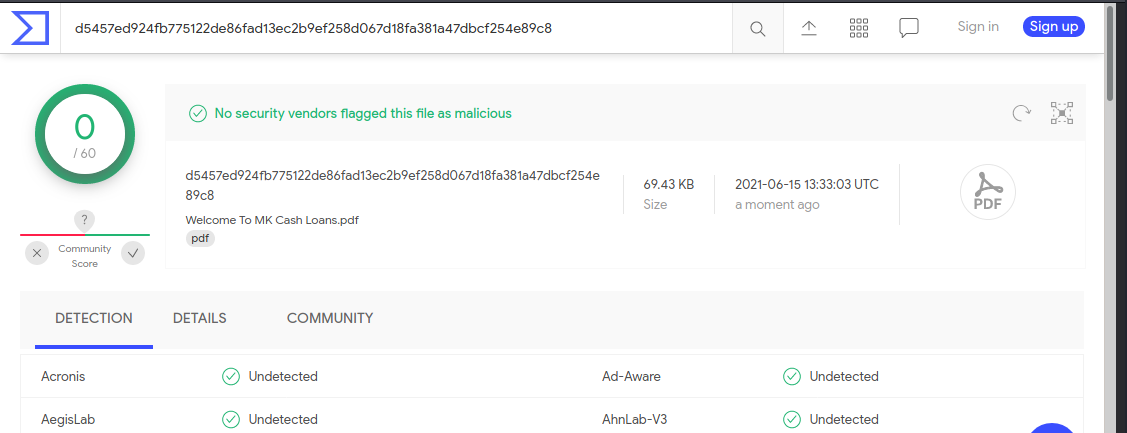
I tested the PDF file on VirusTotal and it came back clean.
I opened the 2021-06-15-Welcome To MK Cash Loans PDF File
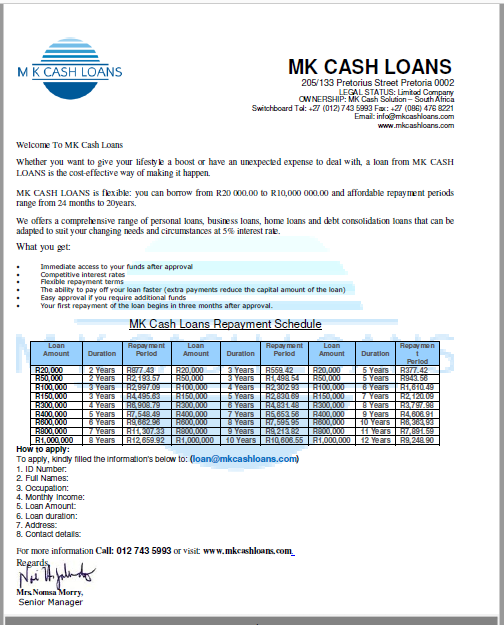
Following the instructions would provide the phisher with a wealth of personal information. The link on the PDF attachment resolves to the mkcashloans.com web site.
All around, this just seems like an loan offer from a loan company. But sharing your financial information with strangers could be back for your wealth.
New Email Attack Takes a Phishing-Turned-Vishing Angle To Steal Credit Card Info
Details on this new scam demonstrate how cybercriminal gangs are working to try use new angles and social engineering methods to trick users into becoming victims.
Receiving a bogus email pretending to be from Amazon is old news. We’ve seen countless impersonation emails over the last year alone. But this latest email-based attack documented by security researchers at Armorblox tells the tale of a phishing email that becomes a vishing (voice phishing) attack to trick potential victims into giving up personal details.
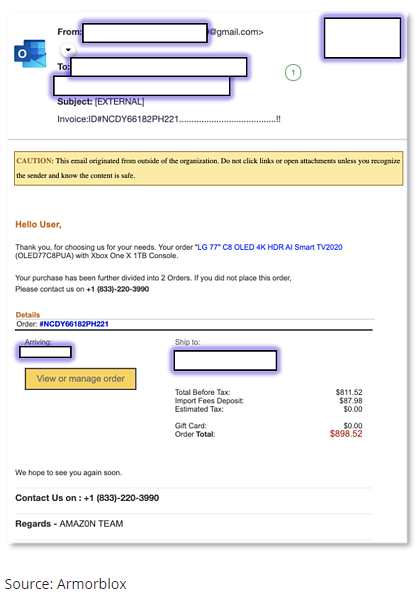
According to Armorblox, victims receive a realistic-looking Amazon email stating the recipient ordered a 77” TV (which are very expensive!).
The real brilliant part is with the “View or Manage Order” button – it’s nothing but an image with no URL linked to it whatsoever. Instead, you’ll note, there’s a message stating “If you did not place this order, please contact us at XXX-XXX-XXXX.”
This is where the phishing attack becomes a vishing attack.
When the victim calls the phone number (which is redirected to a disposable Google Voice number), a live person answers the call pretending to be from Amazon. They ask the victim for the order number, their name, and then verify credit card details before they cut the call short on purpose and block the victim’s number.
This kind of social engineering shows just how far the bad guys will go to establish credibility to lower someone’s defenses. Since most users are aware of phishing attacks, educating them via security awareness training about vishing attacks is also necessary to keep the organization safe from all attack vectors.
Blog post with links and screenshot:
https://blog.knowbe4.com/new-amazon-email-takes-a-phishing-turned-vishing-approach-to-steal-credit-card-information
How to hack into 5500 accounts… just using “credential stuffing”
Passwords – don’t just pay them lip service. We all ought to know by now that passwords that are easy to guess will get guessed. We recently reminded ourselves of that by guessing, by hand, 17 of the top 20 passwords in the Have I Been Pwned (HIBP) Pwned Passwords database in under two minutes…. More
Coronavirus phishing: “Welcome back to the office…”
While many are still working from home, hackers are already launching the next wave of phishing attacks. We take a look at coronavirus phishing emails claiming that offices are reopening post-pandemic.
Share
JUN







About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com