One of these URLs will open your Gmail account. The other will take you to a replica phishing landing page to steal your Gmail password. Can you tell which is which?
![]()
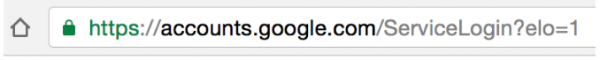
If you chose the first one as fake, and the second one as genuine, you are ...
Continue Reading →JAN

 As we approach year-end, many small and medium sized business owners and managers are coming to the realization that their best intentions for creating a cybersecurity program in their organization have fallen short. This was the year, you promised yourself, that we get a handle on computer and network security.
As we approach year-end, many small and medium sized business owners and managers are coming to the realization that their best intentions for creating a cybersecurity program in their organization have fallen short. This was the year, you promised yourself, that we get a handle on computer and network security. On Wednesday we looked at several of the important takeaways from this year’s Cyber Security Summit. Here are a few more.
On Wednesday we looked at several of the important takeaways from this year’s Cyber Security Summit. Here are a few more. Not trying to be rude here. Phishing has become the most prevalent form of cyber-attack, and the reason for that is that IT WORKS! It works because most people are very trusting and easily convinced, and are clicking on links and opening attachments without much concern. It also works because most people have not been trained
Not trying to be rude here. Phishing has become the most prevalent form of cyber-attack, and the reason for that is that IT WORKS! It works because most people are very trusting and easily convinced, and are clicking on links and opening attachments without much concern. It also works because most people have not been trained  Research shows that over 90% of network breaches happen when an employee falls prey to a phishing email, clicking on the offered link or opening a file attachment, becoming infected with a remote access Trojan, and creating an entry point for the attacker. If only we could get people to stop falling for phishing emails!
Research shows that over 90% of network breaches happen when an employee falls prey to a phishing email, clicking on the offered link or opening a file attachment, becoming infected with a remote access Trojan, and creating an entry point for the attacker. If only we could get people to stop falling for phishing emails! On Wednesday we discussed the many, many ways your smartphone is vulnerable to attack. Today we will look at solutions. Smart mobile devices need to be secured just as you would a laptop or desktop computer The small size and easy portability of smartphones and tablets make them easier to steal or lose. Some of our recommendations:
On Wednesday we discussed the many, many ways your smartphone is vulnerable to attack. Today we will look at solutions. Smart mobile devices need to be secured just as you would a laptop or desktop computer The small size and easy portability of smartphones and tablets make them easier to steal or lose. Some of our recommendations: Although my very first PC user experience was on an Apple IIe back in 1984, I have really been a Windows guy for the most part. Got on my first Windows PC back around 1991, and bought my first Windows PC (Windows 3.11) in 1994. I do have an iMac in my current computer collection. But lately I have been playing around more and more in the Linux platform, both Ubuntu ...
Although my very first PC user experience was on an Apple IIe back in 1984, I have really been a Windows guy for the most part. Got on my first Windows PC back around 1991, and bought my first Windows PC (Windows 3.11) in 1994. I do have an iMac in my current computer collection. But lately I have been playing around more and more in the Linux platform, both Ubuntu ... If you are in high school (or junior high) or college, attracted to technology, and looking for a career with a future, then you should give serious consideration to the field of Cybersecurity. A recent press release from
If you are in high school (or junior high) or college, attracted to technology, and looking for a career with a future, then you should give serious consideration to the field of Cybersecurity. A recent press release from  Last week we took an in depth look at social engineering, and looked a phone and email examples in depth.
Last week we took an in depth look at social engineering, and looked a phone and email examples in depth.