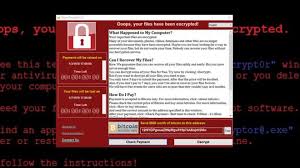
 Toward the end of last year I made a pair of bold predictions. The first, that ransomware exploits would start declining, because anti-malware software companies were bringing products online that would prevent the encryption from taking place. The second, there would be an increase in Business Email Compromise (BEC) exploits, as cyber-criminals turned to new income streams. I was only half right.
Toward the end of last year I made a pair of bold predictions. The first, that ransomware exploits would start declining, because anti-malware software companies were bringing products online that would prevent the encryption from taking place. The second, there would be an increase in Business Email Compromise (BEC) exploits, as cyber-criminals turned to new income streams. I was only half right.
BEC exploits have increased, because the potential returns are so ...
Continue Reading →JUL







 I read an interesting article on Naked Security the other day about how Hamas had used Facebook and social engineering tactics to trick Israeli soldiers into installing surveillance malware. The malware allowed Hamas to track the soldiers using the phone’s GPS, and to turn on the microphone and video to actually listen in and and watch their targets. Hamas undoubtedly picked up the ...
I read an interesting article on Naked Security the other day about how Hamas had used Facebook and social engineering tactics to trick Israeli soldiers into installing surveillance malware. The malware allowed Hamas to track the soldiers using the phone’s GPS, and to turn on the microphone and video to actually listen in and and watch their targets. Hamas undoubtedly picked up the ... On Wednesday we talked about a phishing exploit that used malware to provide remote access and steal the personal information of the victims. Today we continue the story with a similar exploit, called “Fareit” to “ferret out” the user credentials and other personal information the victims.
On Wednesday we talked about a phishing exploit that used malware to provide remote access and steal the personal information of the victims. Today we continue the story with a similar exploit, called “Fareit” to “ferret out” the user credentials and other personal information the victims.