 A new exploit that uses a PowerPoint feature that enables “mouse-over actions.” This feature allows a PowerPoint slide show to initiate activity without having to actually click on a link. Just hovering on a link is enough to advance to the next step. Since we have been teaching people for years to reveal a link destination by hovering over a link to show the top tip box, this exploit would take advantage of that security practice.
A new exploit that uses a PowerPoint feature that enables “mouse-over actions.” This feature allows a PowerPoint slide show to initiate activity without having to actually click on a link. Just hovering on a link is enough to advance to the next step. Since we have been teaching people for years to reveal a link destination by hovering over a link to show the top tip box, this exploit would take advantage of that security practice.
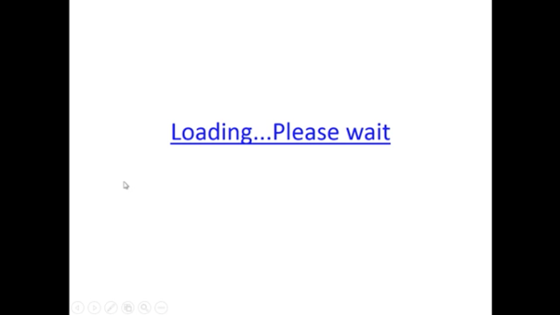
This exploit is usually delivered in a phishing email as an attachment, using subject lines like “Purchase Order #XXXXXX” and “Confirmation”. When opening the PowerPoint attachment, a single slide appears that says, “Loading…Please wait. Clicking on or even just hovering over the link will run a PowerPoint shell command to launch the malware payload.
Fortunately, Microsoft Office users running updated version of PowerPoint should be protected by the Protected View security feature. PowerPoint will spawn a security warning window that requires users to override the security feature to run the shell code. Many users would be put off by the warning and stop at this step. Hopefully this applies to your user group.
This exploit is delivering updated versions of the Tinba banking Trojan, such as Zusy and Gootkit. These banking Trojans are known to spawn realistic looking browser pop-up windows such as the one below. These forms are used to steal information and send it to the attacker.
Your best defense is to make sure the Protected View is enabled in your Office installations. Then alert your user group to this new threat. The bank account balance they save may be their own. Please refer your user group to this article if you wish.
More information:
- Barkly blog
- Security Affairs blog
- Mouse-over effect tutorial (In case you are curious about what this feature was really designed to do.)
JUN






About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com