 Back on August 31 I received an email from the Department of Homeland Security about a set of FTC recommendations for people using rental cars. I have experienced this issue myself. Basically, it is simple and relatively convenient to connect a smartphone to the smart vehicle’s infotainment system in order to enjoy hands free phone calls, stored musical tracks, and the phone’s navigation application. The problem is that the car ...
Back on August 31 I received an email from the Department of Homeland Security about a set of FTC recommendations for people using rental cars. I have experienced this issue myself. Basically, it is simple and relatively convenient to connect a smartphone to the smart vehicle’s infotainment system in order to enjoy hands free phone calls, stored musical tracks, and the phone’s navigation application. The problem is that the car ...
OCT

 As we add more mobile and portable devices to our digital collection, cybersecurity for mobile devices becomes more important. Smartphones, tablets, wearable tech, and ultra-portable laptops are certainly convenient and easy to carry, but that makes them easy for a thief to carry off. When these devices are stolen, you lose much more than the hardware. Every bit of information on the device is up for grabs too, from contact lists, personal information, ...
As we add more mobile and portable devices to our digital collection, cybersecurity for mobile devices becomes more important. Smartphones, tablets, wearable tech, and ultra-portable laptops are certainly convenient and easy to carry, but that makes them easy for a thief to carry off. When these devices are stolen, you lose much more than the hardware. Every bit of information on the device is up for grabs too, from contact lists, personal information, ... When you lose your login credentials to an online account, it can be devastating. Depending on what was compromised and what was lost, you may have an expensive and time-consuming task on your hands. So the bad guys took your user ID and password, or some other personal information. Was it worth it? There is an active resale market for this information, and ...
When you lose your login credentials to an online account, it can be devastating. Depending on what was compromised and what was lost, you may have an expensive and time-consuming task on your hands. So the bad guys took your user ID and password, or some other personal information. Was it worth it? There is an active resale market for this information, and ... I read about this on
I read about this on  We warned our readers about the
We warned our readers about the  Phishing is still the overwhelming go-to choice for cyber-criminals launching an attack. Over 90% of computer system breaches start with a phishing email in an inbox. Finding ways to unmask these impostors is a good first step are protecting yourself from a phishing exploit. Let’s look at this first example, apparently from a law firm about a legal action.
Phishing is still the overwhelming go-to choice for cyber-criminals launching an attack. Over 90% of computer system breaches start with a phishing email in an inbox. Finding ways to unmask these impostors is a good first step are protecting yourself from a phishing exploit. Let’s look at this first example, apparently from a law firm about a legal action.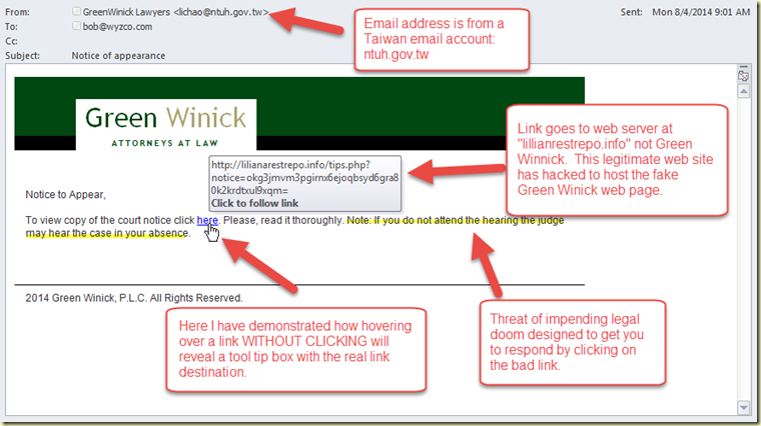
 I very rarely will publish a news item or statistics, because we focus on discussing vulnerabilities, exploits, and countermeasures and leave the cyber news to others. This report is important enough I had to share it.
I very rarely will publish a news item or statistics, because we focus on discussing vulnerabilities, exploits, and countermeasures and leave the cyber news to others. This report is important enough I had to share it. Mobile smart devices have all the capabilities of a laptop or computer. What this means from a cybersecurity perspective is that they are every bit as vulnerable as a laptop or desktop computer. The fact that they are small makes them easy for a thief to slip in a pocket or backpack and carry away, along with your personal information, contacts, pictures, geo-location history, and a raft of critical and revealing ...
Mobile smart devices have all the capabilities of a laptop or computer. What this means from a cybersecurity perspective is that they are every bit as vulnerable as a laptop or desktop computer. The fact that they are small makes them easy for a thief to slip in a pocket or backpack and carry away, along with your personal information, contacts, pictures, geo-location history, and a raft of critical and revealing ... One of the very worst breaches that can happen to you is for an attacker to be able to access your email account. If someone else can access your email, and read the messages you send and receive, and access your contact list and calendar, then they can learn many personal details about you that would make it easier to steal your identity, access other web accounts using the password reset ...
One of the very worst breaches that can happen to you is for an attacker to be able to access your email account. If someone else can access your email, and read the messages you send and receive, and access your contact list and calendar, then they can learn many personal details about you that would make it easier to steal your identity, access other web accounts using the password reset ... I read a couple of thought provoking articles recently on the subject of data security, and more directly, on how data destruction can serve to permanently “secure” the data that is destroyed. One article appeared in the
I read a couple of thought provoking articles recently on the subject of data security, and more directly, on how data destruction can serve to permanently “secure” the data that is destroyed. One article appeared in the