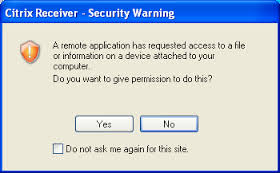
 A recent article from Naked Security said that people ignore legitimate security warnings on their computer a whopping 87% of the time. But on the flip side, I know from experience that a good percentage of people will fall for a pop-up of the fake tech support variety all too often. What is going on here?
A recent article from Naked Security said that people ignore legitimate security warnings on their computer a whopping 87% of the time. But on the flip side, I know from experience that a good percentage of people will fall for a pop-up of the fake tech support variety all too often. What is going on here?
What seems to be the consensus is that people are overwhelmed by the number of ...
Continue Reading →SEP

 The rare Tuesday post. I got an
The rare Tuesday post. I got an  When you lose your login credentials to an online account, it can be devastating. Depending on what was compromised and what was lost, you may have an expensive and time-consuming task on your hands. So the bad guys took your user ID and password, or some other personal information. Was it worth it? There is an active resale market for this information, and ...
When you lose your login credentials to an online account, it can be devastating. Depending on what was compromised and what was lost, you may have an expensive and time-consuming task on your hands. So the bad guys took your user ID and password, or some other personal information. Was it worth it? There is an active resale market for this information, and ... I read about this on
I read about this on  Phishing is still the overwhelming go-to choice for cyber-criminals launching an attack. Over 90% of computer system breaches start with a phishing email in an inbox. Finding ways to unmask these impostors is a good first step are protecting yourself from a phishing exploit. Let’s look at this first example, apparently from a law firm about a legal action.
Phishing is still the overwhelming go-to choice for cyber-criminals launching an attack. Over 90% of computer system breaches start with a phishing email in an inbox. Finding ways to unmask these impostors is a good first step are protecting yourself from a phishing exploit. Let’s look at this first example, apparently from a law firm about a legal action.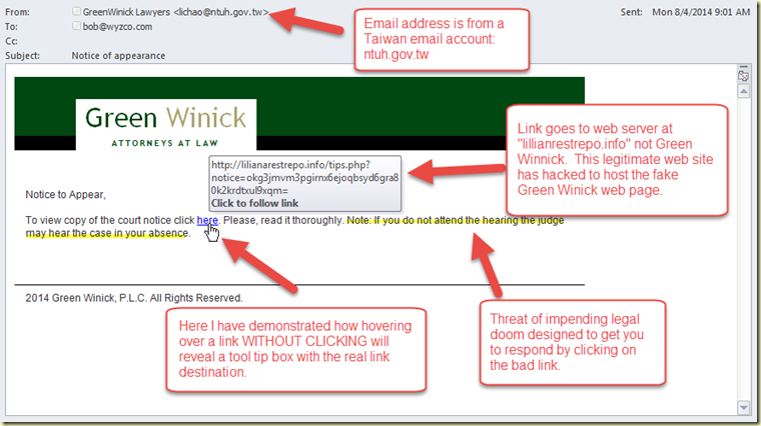
 Holy acronyms Batman! What the heck does this headline mean? Well, the National Institute for Standards and Technology (NIST) has removed two-factor authentication (TFA) via short-messaging service (SMS) from the approved list of two-factor authentication methods. The reason is that SMS is an unencrypted service, and the lack of encryption makes it too insecure for use in Federal authentication systems. NIST is recommending that all ...
Holy acronyms Batman! What the heck does this headline mean? Well, the National Institute for Standards and Technology (NIST) has removed two-factor authentication (TFA) via short-messaging service (SMS) from the approved list of two-factor authentication methods. The reason is that SMS is an unencrypted service, and the lack of encryption makes it too insecure for use in Federal authentication systems. NIST is recommending that all ... Bruce Schneier had an
Bruce Schneier had an 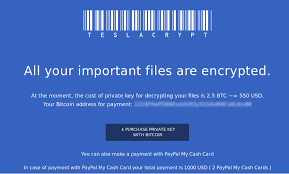 You have trained your staff and improved your defenses. In spite of your best efforts, you have an active case of crypto-malware running on a system in your business. How do you recover?
You have trained your staff and improved your defenses. In spite of your best efforts, you have an active case of crypto-malware running on a system in your business. How do you recover?