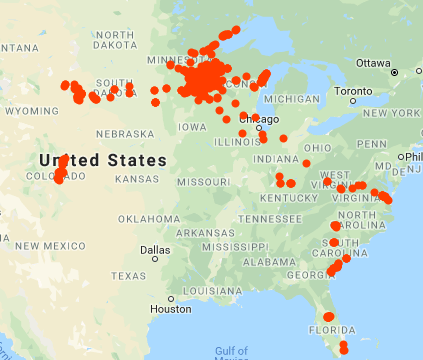
 A lot of very specific location information is being collected about you, me, and every other smartphone user. The image at left shows everywhere I have been in the last four years, courtesy of Google location services. If you would like to find out what is being collected about you, and how to make it stop, the last article and this article will ...
A lot of very specific location information is being collected about you, me, and every other smartphone user. The image at left shows everywhere I have been in the last four years, courtesy of Google location services. If you would like to find out what is being collected about you, and how to make it stop, the last article and this article will ...
JUL