 Monday we looked at issues with the business class routers at Juniper Networks and Cisco Systems. Today we are going to look at an exploit affecting the Ubiquiti brand of cable modems.
Monday we looked at issues with the business class routers at Juniper Networks and Cisco Systems. Today we are going to look at an exploit affecting the Ubiquiti brand of cable modems.
Cable and DSL “modems” are used by most consumers, and many small businesses to connect their home or business network to the Internet. These “modems” are really routers.
(It has been a personal pet peave of mine that these devices were called modems ...
Continue Reading →FEB

 At the end of December last year Juniper Networks discovered that some malicious actors had added code to the firmware and software that run their routers, creating a back door that would allow attackers to access the router remotely, assume administrator privileges, and view and decrypt VPN traffic running through the routers. As the story unfolded, it turns out that Juniper was using a random number generator from NIST, and that the ...
At the end of December last year Juniper Networks discovered that some malicious actors had added code to the firmware and software that run their routers, creating a back door that would allow attackers to access the router remotely, assume administrator privileges, and view and decrypt VPN traffic running through the routers. As the story unfolded, it turns out that Juniper was using a random number generator from NIST, and that the ...


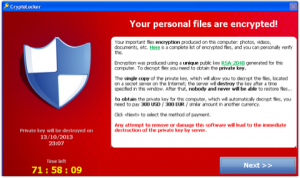 This is hot off the press. Yesterday
This is hot off the press. Yesterday  Another story from my friends at
Another story from my friends at  A virtual private network, or VPN, is a type of network computer connection that creates a private encrypted communications channel, commonly called a “tunnel,” when using insecure networks, such as in hotels and coffee shops, or when communicating over the Internet. Many businesses provide a VPN connection for their mobile and traveling employees. This means that when out of the office, a worker can open the VPN and be connected to ...
A virtual private network, or VPN, is a type of network computer connection that creates a private encrypted communications channel, commonly called a “tunnel,” when using insecure networks, such as in hotels and coffee shops, or when communicating over the Internet. Many businesses provide a VPN connection for their mobile and traveling employees. This means that when out of the office, a worker can open the VPN and be connected to ...