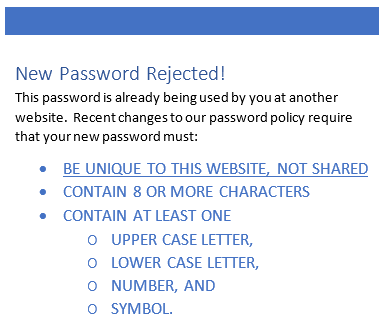
Did you know that the most popular passwords can be cracked in minutes? And that passwords with 8 characters or fewer can be cracked in a few seconds? This is why I say that passwords by themselves are no longer a useful form of security. Today is the second of a five part series on password security, and focuses on the methodology used by password cracking software programs.
Cyber-criminal groups who specialize in password cracking generally harvest huge lists of user ...
Continue Reading →JUN