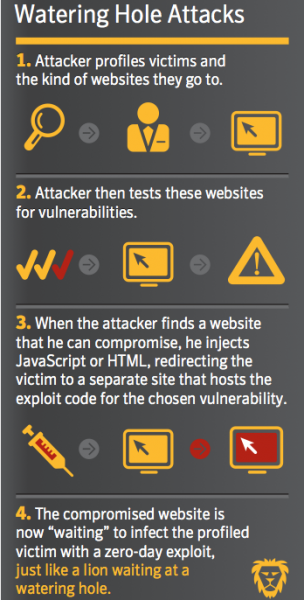
 We’ve all seen this on National Geographic. A lion, tiger, or other top predator hides near a water hole and waits for some sort of four-legged lunch to stop by for a drink. Cyber-criminals and other attackers are using a similar technique to download and install malware from niche or industry specific websites to computer systems at targeted businesses. Here’s how ...
We’ve all seen this on National Geographic. A lion, tiger, or other top predator hides near a water hole and waits for some sort of four-legged lunch to stop by for a drink. Cyber-criminals and other attackers are using a similar technique to download and install malware from niche or industry specific websites to computer systems at targeted businesses. Here’s how ...
JAN







