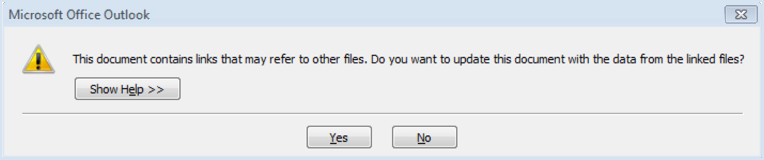
People often ask me if it is dangerous to simply open an email, if it is possible to get a malware inflection just by reading an email. My answer has been a qualified “not at this time.” Unfortunately, this is no longer true. It is possible to get a malware installation from the new DDE (Dynamic Data Exchange) exploits reveal by Sophos Labs on October 13 2017. This can be accomplished without an attachment or link if the email is written in Rich Text format. The only clue you will get that this is happening to you are the dialog boxes below. The only correct answer is NO!
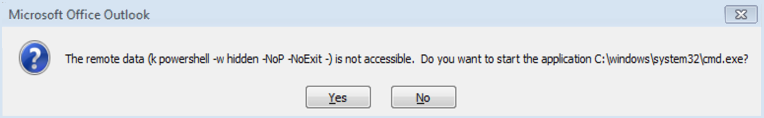
If your some reason you click yes, you get one more chance to choose wisely when the following dialog opens.
Dynamic Data Exchange is a 24 year old feature of the Microsoft Office suite of productivity applications. This feature allows a user to do things such as embed an Excel chart from a spreadsheet into a Word document, and have the chart in the Word document connected to the Excel spreadsheet so whenever you change values in the spreadsheet, the chart in the Word document is automatically updated.
This exploit was originally discovered to be using infected Word, Excel or other Office document attachments in email. What was unique is that the exploit did not require macros to run. This exploit works by calling out to a document that is actually located on a web server the attacker controls.
What makes the Outlook email attack variety so powerful is that no attachment is required. This attack will appear as an email (or an Outlook Meeting Request) without an attachment or link. The email will appear to be safe, since bad stuff only happens when you open attachments or click links, right? Not so any more. The trick is that the email is written using Rich Text format. RTF allows DDE to execute without the user ever seeing the code, since it is embedded in the email itself.
The good news is the DDE attack in Outlook isn’t completely automated. The user will see the dialog boxes shown above. Clicking NO on either of them stops the attack.
In the example above, clicking yes on both dialog boxes will launch a Windows Command dialog, allowing the attacker to inject commands directly to the operating system, and download more malware from command and control servers on the Internet. Often the first step of this exploit is to install a remote access Trojan horse program, or RAT, to give the attacker access to and control of the compromised computer.
What can you do? For Office attachments and Outlook emails, here are our recommendations:
- Read and understand popup messages! If you receive an email and either of the dialog boxes appears, you have a problem. In the worst case DDE attack scenario, users are still prompted twice before the attack can happen. The older macro-fueled version of this exploit will ask you to enable macros, which you should not do either. If you don’t understand the message from the dialog box, a quick Google search will explain the meaning. Do not just click yes.
- Don’t open attachments. If you receive a Word, Excel, PowerPoint or other Office document by email and you aren’t expecting it or don’t know the person who sent it, it’s better to leave it unopened. Even if you know the sender, if the email was sent from a hijacked email account, it will be a fake email from a genuine email account. Call the sender to confirm the authenticity of the email and attachment.
- Use an endpoint anti-malware with real-time protection. This product will protect you between system scans by examining all incoming traffic for malware. This can help you block this exploit.
- Configure stronger email gateway and filter settings. This may create some additional work for staff as some legitimate email may be directed in spam, junk, or quarantine folders, but the inconvenience is less expensive than the risk of infection.
- Receive emails in plain text only. Emails viewed in plain text will stop RTF code from executing. Unfortunately this breaks HTML formatted emails as well, and makes them difficult to read. This will not be popular with your user base.
- Train your staff. Even if it is nothing more than sharing a link to this article or the others included below, it is important that your staff be aware of this new exploit.
More information:
- Sophos Labs – DDE Zero-day
- Sophos Labs – DDE works in Outlook
- Tech Republic
- WyzGuys – Hijacked Email Account
Share
NOV




About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com