 Almost all cyber-crime is about making money for the crooks. Often this involves stealing valuable information that can be sold. But many criminal gangs are going straight for the cash, and often this involves bank and financial account fraud or financial account access.
Almost all cyber-crime is about making money for the crooks. Often this involves stealing valuable information that can be sold. But many criminal gangs are going straight for the cash, and often this involves bank and financial account fraud or financial account access.
Below we have a list of strategies you can use to protect your financial resources.
- Use a credit card ...
MAR

 2017 is promising to be another difficult year for cyber-defenders who are protecting company and government networks from attack. Here are what I think will be the top attack vectors this year.
2017 is promising to be another difficult year for cyber-defenders who are protecting company and government networks from attack. Here are what I think will be the top attack vectors this year.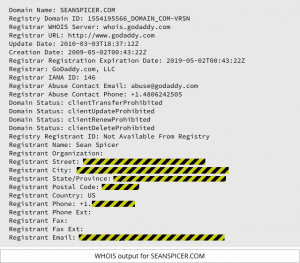 I will start out by admitting that I hate Domain Privacy. But I just read a story in
I will start out by admitting that I hate Domain Privacy. But I just read a story in  On Wednesday we talked about a phishing exploit that used malware to provide remote access and steal the personal information of the victims. Today we continue the story with a similar exploit, called “Fareit” to “ferret out” the user credentials and other personal information the victims.
On Wednesday we talked about a phishing exploit that used malware to provide remote access and steal the personal information of the victims. Today we continue the story with a similar exploit, called “Fareit” to “ferret out” the user credentials and other personal information the victims.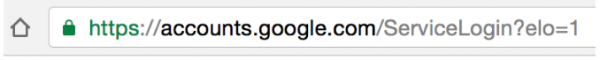
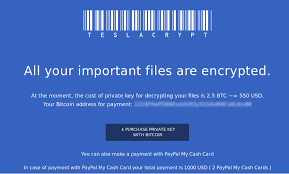 Crypto-ransomware continues to be one of the most popular money making exploits for cyber criminals. The reason for this is simple; its works, and the return on investment is quite high. According to a recent article in
Crypto-ransomware continues to be one of the most popular money making exploits for cyber criminals. The reason for this is simple; its works, and the return on investment is quite high. According to a recent article in  The United States recently accused the Russian government of trying to influence US elections last November, and has expelled 35 Russian diplomatic officials and closed two Russian diplomatic facilities, one in New York City, and the other in Maryland, near Washington DC.
The United States recently accused the Russian government of trying to influence US elections last November, and has expelled 35 Russian diplomatic officials and closed two Russian diplomatic facilities, one in New York City, and the other in Maryland, near Washington DC. This is the time of the year everyone writes either a year in review article, or a what’s coming in the new year post. Guess which one this is? I’ve been reading the pundits, and considering my own findings as a cybersecurity professional. I pulled together the following list for your review, and to help you plan where to spend your time, talent, and budget in 2017.
This is the time of the year everyone writes either a year in review article, or a what’s coming in the new year post. Guess which one this is? I’ve been reading the pundits, and considering my own findings as a cybersecurity professional. I pulled together the following list for your review, and to help you plan where to spend your time, talent, and budget in 2017. One of the hardest types of phishing emails to defend against are those that come from the email account of a friend or trusted business associate, such as your dentist, lawyer, realtor. The sender’s email address is not spoofed, because the malefactor has tricked them into providing their email address password. The bad guys are actually logged into your friend’s email account, and now they are trying to do the same thing to ...
One of the hardest types of phishing emails to defend against are those that come from the email account of a friend or trusted business associate, such as your dentist, lawyer, realtor. The sender’s email address is not spoofed, because the malefactor has tricked them into providing their email address password. The bad guys are actually logged into your friend’s email account, and now they are trying to do the same thing to ...