 Russian cyber-criminals are hard to arrest, because there is no extradition treaty between the US and Russia. The Russian government allows them to prosper as long as they do not attack anything in Russia. The Russian government also contracts with these criminal groups when they need some state sponsored hacking done, a la Grizzly Steppe. In Russia, these guys are considered to be just very successful business men. They have achieved ...
Russian cyber-criminals are hard to arrest, because there is no extradition treaty between the US and Russia. The Russian government allows them to prosper as long as they do not attack anything in Russia. The Russian government also contracts with these criminal groups when they need some state sponsored hacking done, a la Grizzly Steppe. In Russia, these guys are considered to be just very successful business men. They have achieved ...
APR


 Social networks are a tremendous source of personal information leakage. Actually, more like a waterfall. As we learned in the last post, attackers use social networks to perform reconnaissance against their chosen targets. Since few of us are going to delete all our social network accounts and move of the grid, we have to find a way to live ...
Social networks are a tremendous source of personal information leakage. Actually, more like a waterfall. As we learned in the last post, attackers use social networks to perform reconnaissance against their chosen targets. Since few of us are going to delete all our social network accounts and move of the grid, we have to find a way to live ... 2017 is promising to be another difficult year for cyber-defenders who are protecting company and government networks from attack. Here are what I think will be the top attack vectors this year.
2017 is promising to be another difficult year for cyber-defenders who are protecting company and government networks from attack. Here are what I think will be the top attack vectors this year.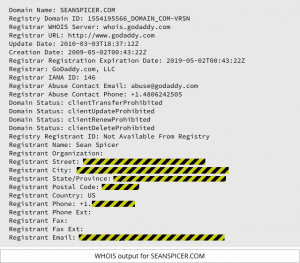 I will start out by admitting that I hate Domain Privacy. But I just read a story in
I will start out by admitting that I hate Domain Privacy. But I just read a story in  I read an interesting article on Naked Security the other day about how Hamas had used Facebook and social engineering tactics to trick Israeli soldiers into installing surveillance malware. The malware allowed Hamas to track the soldiers using the phone’s GPS, and to turn on the microphone and video to actually listen in and and watch their targets. Hamas undoubtedly picked up the ...
I read an interesting article on Naked Security the other day about how Hamas had used Facebook and social engineering tactics to trick Israeli soldiers into installing surveillance malware. The malware allowed Hamas to track the soldiers using the phone’s GPS, and to turn on the microphone and video to actually listen in and and watch their targets. Hamas undoubtedly picked up the ...