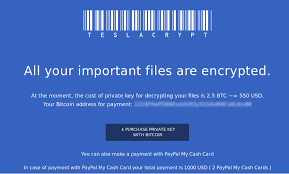
 Crypto-ransomware continues to be one of the most popular money making exploits for cyber criminals. The reason for this is simple; its works, and the return on investment is quite high. According to a recent article in Naked Security, the score will reach $1 billion in 2017.
Crypto-ransomware continues to be one of the most popular money making exploits for cyber criminals. The reason for this is simple; its works, and the return on investment is quite high. According to a recent article in Naked Security, the score will reach $1 billion in 2017.
A poll by the IBM company found that nearly 50% of the businesses polled had been hit by ransomware, and of those 70% paid ...
Continue Reading →JAN

 There are a number of great frameworks for developing your cybersecurity plan. Two of our favorites are the
There are a number of great frameworks for developing your cybersecurity plan. Two of our favorites are the  The Federal Trade Commission recently released an warning about fraudulent mobile apps. These apps are designed to steal personal information such as user names, passwords, credit card numbers, and other personal information.
The Federal Trade Commission recently released an warning about fraudulent mobile apps. These apps are designed to steal personal information such as user names, passwords, credit card numbers, and other personal information. The United States recently accused the Russian government of trying to influence US elections last November, and has expelled 35 Russian diplomatic officials and closed two Russian diplomatic facilities, one in New York City, and the other in Maryland, near Washington DC.
The United States recently accused the Russian government of trying to influence US elections last November, and has expelled 35 Russian diplomatic officials and closed two Russian diplomatic facilities, one in New York City, and the other in Maryland, near Washington DC. The House Judiciary Committee’s Encryption Working Group has released a
The House Judiciary Committee’s Encryption Working Group has released a  This is the time of the year everyone writes either a year in review article, or a what’s coming in the new year post. Guess which one this is? I’ve been reading the pundits, and considering my own findings as a cybersecurity professional. I pulled together the following list for your review, and to help you plan where to spend your time, talent, and budget in 2017.
This is the time of the year everyone writes either a year in review article, or a what’s coming in the new year post. Guess which one this is? I’ve been reading the pundits, and considering my own findings as a cybersecurity professional. I pulled together the following list for your review, and to help you plan where to spend your time, talent, and budget in 2017. Cybersecurity professionals are in agreement. The Russians appear to have been actively engaged in influencing the outcome of our recent Presidential election. Specifics include compromising and taking over Hilary Clinton’s chief of staff, John Podesta’s personal Gmail account. This spear phishing exploit used a “near-miss” domain name of “accounts.googlemail.com” to trick John into clicking on a link and and entering his email credentials. The real domain name is accounts.google.com.
Cybersecurity professionals are in agreement. The Russians appear to have been actively engaged in influencing the outcome of our recent Presidential election. Specifics include compromising and taking over Hilary Clinton’s chief of staff, John Podesta’s personal Gmail account. This spear phishing exploit used a “near-miss” domain name of “accounts.googlemail.com” to trick John into clicking on a link and and entering his email credentials. The real domain name is accounts.google.com. The FBI recently reported on arrests of a number of lottery scammers in what they call
The FBI recently reported on arrests of a number of lottery scammers in what they call