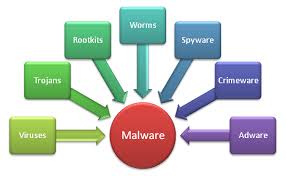
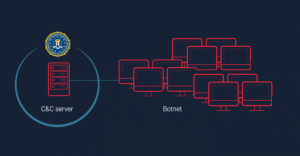
I have been fortunate to have had time to pursue a couple of information technology certifications recently. I have added CompTIA’s Network+ and CASP (Certified Advanced Security Professional), and I am working on the brand new CompTIA Pentest+. The certification is so new there are no text books yet, and the exam was just released on July 31. I have been taking the ...
I have been fortunate to have had time to pursue a couple of information technology certifications recently. I have added CompTIA’s Network+ and CASP (Certified Advanced Security Professional), and I am working on the brand new CompTIA Pentest+. The certification is so new there are no text books yet, and the exam was just released on July 31. I have been taking the ...
AUG