 2017 is promising to be another difficult year for cyber-defenders who are protecting company and government networks from attack. Here are what I think will be the top attack vectors this year.
2017 is promising to be another difficult year for cyber-defenders who are protecting company and government networks from attack. Here are what I think will be the top attack vectors this year.
Business Email Compromise
CEOs and other C suite officers will increasingly be targeted for email account hijacking. This is an easy exploit to run because high ranking employees and officers often are ...
Continue Reading →MAR

 US-CERT just released more information about the Grizzly Steppe cybercrime group who has been fingered for hacking the DNC and US voter registration databases. The short report, titled
US-CERT just released more information about the Grizzly Steppe cybercrime group who has been fingered for hacking the DNC and US voter registration databases. The short report, titled 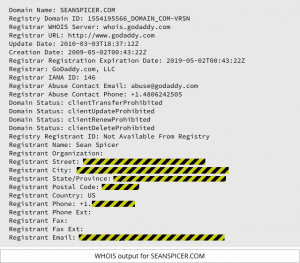 I will start out by admitting that I hate Domain Privacy. But I just read a story in
I will start out by admitting that I hate Domain Privacy. But I just read a story in  I read an interesting article on Naked Security the other day about how Hamas had used Facebook and social engineering tactics to trick Israeli soldiers into installing surveillance malware. The malware allowed Hamas to track the soldiers using the phone’s GPS, and to turn on the microphone and video to actually listen in and and watch their targets. Hamas undoubtedly picked up the ...
I read an interesting article on Naked Security the other day about how Hamas had used Facebook and social engineering tactics to trick Israeli soldiers into installing surveillance malware. The malware allowed Hamas to track the soldiers using the phone’s GPS, and to turn on the microphone and video to actually listen in and and watch their targets. Hamas undoubtedly picked up the ... As a regular reader of this blog, you are probably using a long, unique, 20 character password with two-factor authentication, and a password manager to keep it all straight. But let’s say that you fall for a phishing scam, and give away the password to your email account. The attacker can now use your email account to request password reset emails from your other online accounts, and you have yourself one ...
As a regular reader of this blog, you are probably using a long, unique, 20 character password with two-factor authentication, and a password manager to keep it all straight. But let’s say that you fall for a phishing scam, and give away the password to your email account. The attacker can now use your email account to request password reset emails from your other online accounts, and you have yourself one ... NIST is working on
NIST is working on 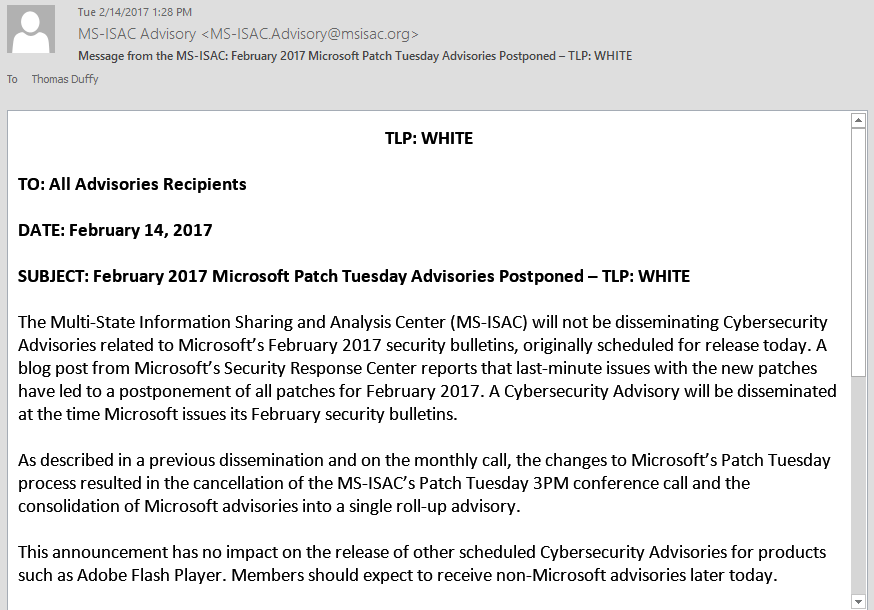
 Passwords are not dead – not yet. But they are on life support. They are no longer enough to truly secure anything on their own.
Passwords are not dead – not yet. But they are on life support. They are no longer enough to truly secure anything on their own. On Wednesday we talked about a phishing exploit that used malware to provide remote access and steal the personal information of the victims. Today we continue the story with a similar exploit, called “Fareit” to “ferret out” the user credentials and other personal information the victims.
On Wednesday we talked about a phishing exploit that used malware to provide remote access and steal the personal information of the victims. Today we continue the story with a similar exploit, called “Fareit” to “ferret out” the user credentials and other personal information the victims.