Today’s post was provided by The Broadband Search. This is the conclusion of the article that was published Wednesday.
Today’s post was provided by The Broadband Search. This is the conclusion of the article that was published Wednesday.
Where, When, and How
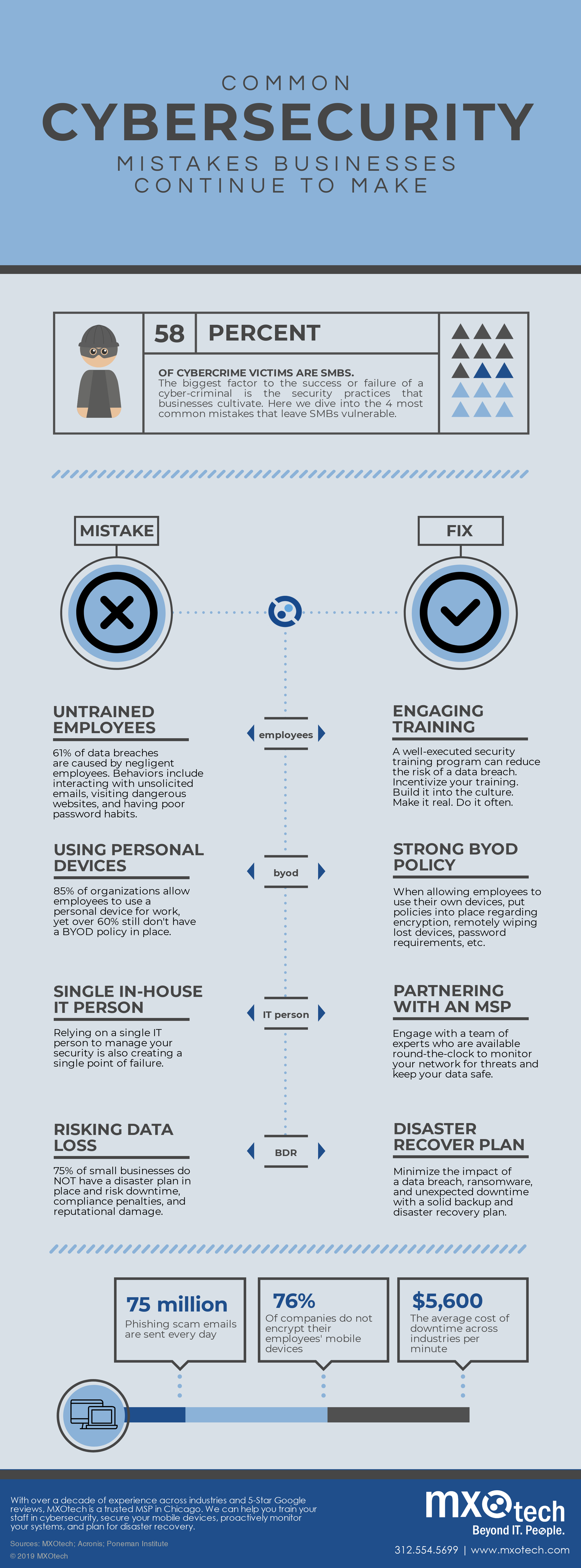
While your small business is a likely target, how do these attacks occur and what targets are used specifically? What are the more precise factors involved and what types of attacks might you expect? Once you ...
Continue Reading →MAR