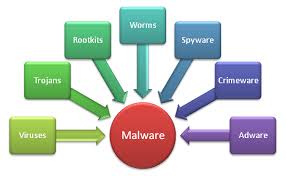
 Most of the small business clients I work with do not have a huge budget for a cybersecurity program, and something like a managed security service program (MSSP) is beyond their reach. They have money for a firewall, and endpoint security, but that is about it. Sound like your business? Then read on.
Most of the small business clients I work with do not have a huge budget for a cybersecurity program, and something like a managed security service program (MSSP) is beyond their reach. They have money for a firewall, and endpoint security, but that is about it. Sound like your business? Then read on.
There are eight simple, free or low-cost things that small business IT professionals or IT support providers can do ...
Continue Reading →JUL



