Two weeks ago when we started this series on password security, we revealed some sad statistics. 60% of people use the same password on multiple accounts. The average person has 26 password protected accounts, but only used 5 passwords across those accounts. And 85% of people keep track of passwords through memorization.
People reuse passwords just because it is easier. I get it, I have over 100 password protected accounts (not 26) and it is not possible for me to keep track of 100 unique passwords through memorization. So where does that leave us?
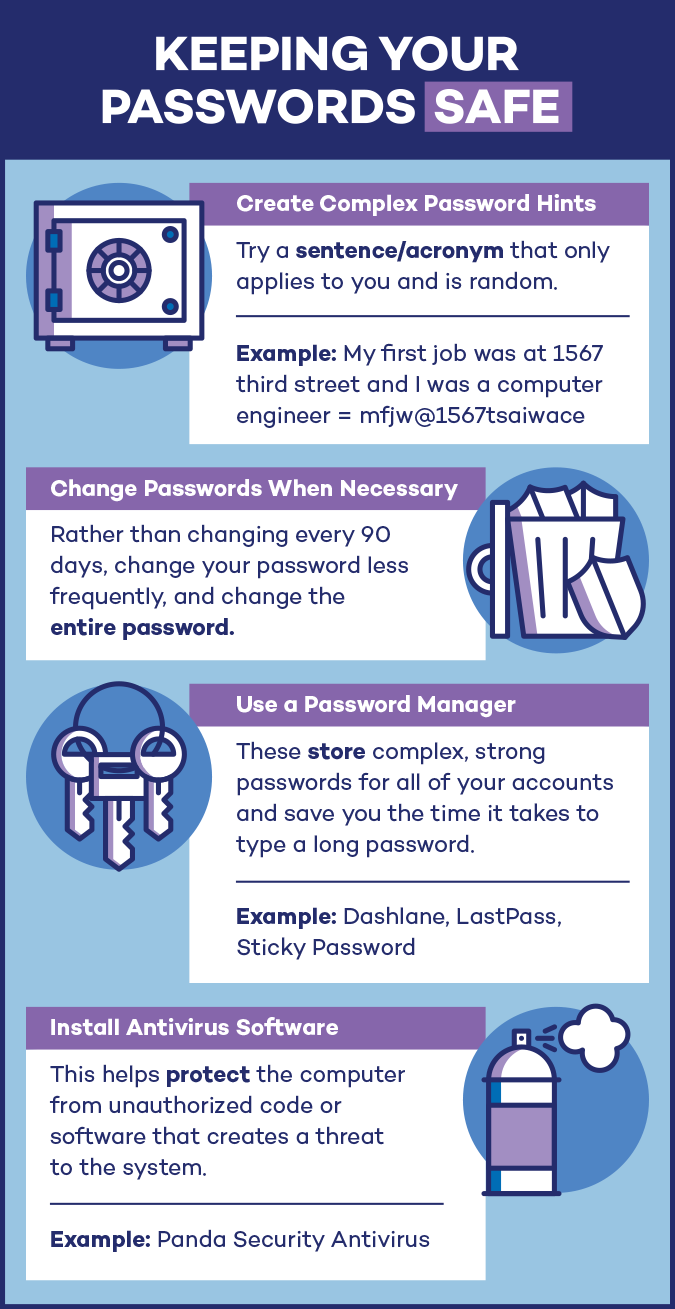
- Lists – When I am working with a client, and we need a password for some rarely accessed account, it is quite common for the client to pull out a handwritten list on a couple sheets of paper, or in a spiral notebook. This is not terribly secure, but as I like to say, if someone has your list, you have other problems. They are in your home or office. Some hyper-organized people have everything on an Excel spreadsheet. The problem with this if your computer is breached or stolen, the criminal has all your passwords. If you are going with a list, keep it on paper.
- The passphrase – in order to avoid using words, some people will develop a passphrase, something like “Tony is number 87 and plays Right Guard for the Ponies.” This produces the password Ti#87&pRG4tP. This is a good solution for the most part and can be coupled with “the system” to produce long an unique passwords.
- The ”system” – Many people, myself included, have a system for creating unique passwords by coupling a base or root password with some characters that identify the site. So I only have to remember the root password, and be able to guess my location text. When I was using this method, my base password was 14 characters, and the additional 3 to 5 characters pushed the final size out to 20 sometimes. The problem here is with predictability. If an attacker has one password, they may be able to see that there is a possible system in use and try other combinations on other websites. A system is predictable and guessable.
- Password manager – All of these solutions have some merit, but there is a better way to create long, random, and site unique passwords and keep them both available to use from anywhere, on any computer, and safely encrypted so the loss of a single password does not create a risk for guessing the remaining passwords. This option is a password manager.
I use LastPass, but there are others. LastPass stores all my passwords in an encrypted account on their website. The password cache is protected by a long password coupled with two-factor authentication. It also features a random password generator, so I no longer have to rely on my passphrase or system to create new passwords. For people who are leery of trusting their passwords to another company, or putting them online in the cloud, there are device local software solutions such as KeePass. Yubikey is another locally stored by portable option, keeping all your passwords on an encrypted USB key.
So the best recommendation I have for you for creating and storing truly strong passwords is:
- Longer is stronger – 12 characters is a good minimum size. Go longer if you can.
- Two-factor authentication – use 2FA everywhere it is offered. If your password is breached, an attacker still needs your smartphone to get the PIN code.
- Password manager – put it all together in a password manager.
- Use a random password generator – your password manager makes that pretty easy to do. Since you have no chance of memorizing these random passwords, its a good thing that the password manager takes care of logging you in. Might as well go to 20-characters if you go random.
So that wraps up our series on passwords. I hope you found the information useful, and were inspired to try out a few of the solutions we offered.
A special thanks to Panda Security for inspiring the content of this series and providing us with the infographics used in this series.
ShareJUN




About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com