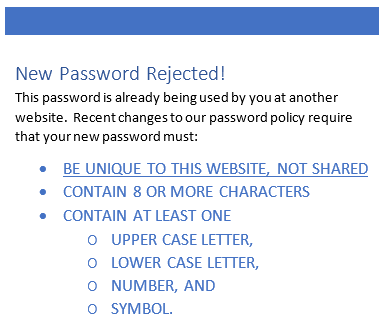
In our last post we looked at the frighteningly short amount of time that it takes to crack a typical password. Today we will look at all the different password cracking methods that a clever attacker can use to compromise your password, and how to defend against these attacks.
Password cracking
There are several types of automated password attacks that can be combined to make the process quicker, or to configure for a certain type of password attack.
- Dictionary attack – This is ...
JUN