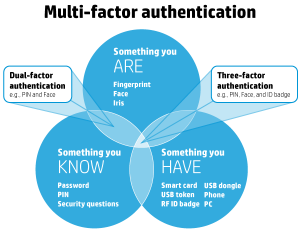
 In our last post we looked at several problems you might encounter using two-factor or multi-factor authentication. If you have two-factor authentication, or are thinking about using it, there are some additional steps you should take in case you lose your second factor and have to re-establish access.
In our last post we looked at several problems you might encounter using two-factor or multi-factor authentication. If you have two-factor authentication, or are thinking about using it, there are some additional steps you should take in case you lose your second factor and have to re-establish access.
- How do I recover my account? Learn this in advance of actual need. Dig into your account profile find the instructions for recovering your account. You might even want to give it a dry run to see what obstacles you might face.
- Backup email address – Just have the one email address? You need a second email address as a backup. Often, it is the email address associated with your Android or iPhone account. Or create one on Yahoo, Gmail, or Outlook.com.
- Answers to knowledge based questions – These are the familiar “grandpa’s middle name” or “name of my elementary school” questions. Set up the answers and write them down in your password manager.
- A list of printable backup codes – Google Authenticator provides this opportunity, as well as other 2FA systems. These can be helpful in the event your battery dies too.
- Create a trusted computer – This is really a “trusted location” that includes information not only about your computer but also the public IP address of your Internet router. Logging in from a trusted computer does not usually require the second factor, and that can give you the access you need to re-establish your account.
- Create a trusted third party – Some two-factor services allow you to get help from an person you nominate to help in case of emergency.
- Back up the Master Secret – This is the QR code or 16 digit alphanumeric security key that you use to set up your account in the first place. Take a picture of the QR code or a copy of the security key and save it in your password manager.
- Recovery codes – These are shorter one-time passwords you can use to recover an account. Again, saving them in your password manager keeps them secure
- Add an additional second factor – This may seem crazy – crazy like a fox. Many sites allow you to register more than one second factor. Lose your phone? If you have also enrolled a USB security key, you can switch to that while your phone is being replaced.
- Limit your use. – Not every account needs two-factor authentication. You should definitely protect your email account, web hosting account, social network accounts and financial accounts, and shopping accounts where you have a credit card on file. Basically anything having to do with your money or your identity. Do you need 2FA on a news, sports, or general interest account? Probably not. Just use 2FA where it makes sense.
I understand, perhaps better than many, that cybersecurity is basically a PITA – a pain in the backside. None the less, in the world we live in, it has become an indispensable part of everyday life. Hopefully we have not scared you off from using multi-factor authentication. But with a little planning, you can make the experience easier for you if things go wrong.
ShareNOV




About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com