 Do the web sites your frequently visit offer two-factor authentication? Have you enabled 2FA where it is available to you? Is the particular implementation of 2FA or MFA security really adding any extra protection for you? Not sure? Please read on.
Do the web sites your frequently visit offer two-factor authentication? Have you enabled 2FA where it is available to you? Is the particular implementation of 2FA or MFA security really adding any extra protection for you? Not sure? Please read on.
Password management company Dashlane recently ranked 34 of the top websites for their implementation of two-factor or multi-factor authentication options for their customers. The results, as far as I am concerned, were less than stellar.
Dashlane found that instructions on how to set up two-factor authentication were often hard to find, and confusing, which would make them harder to deploy for an average non-technical user.
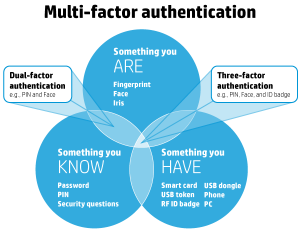
The criteria for analysis included three common 2FA offerings:
- SMS and/or email-based 2FA – If a website offered two-factor access by using SMS or email, they received a point. If is noteworthy that under the current NIST standards in Special Publication 800-63B, that SMS is no longer considered secure, because the channel is not encrypted and subject to man-in-the-middle attacks. Email is rarely encrypted either, and is vulnerable to email account hijacking. If your email account is compromised, the attacker will see your 2FA email response too, or can order one up on their own.
- Software token 2FA – This includes popular options such as Google Authenticator or Authy or a proprietary application offered by the site operator such as Facebook. Offering a software token was worth one point. I might have given this offering 2 points, since it is a significant improvement over SMS/email.
- Hardware token 2FA – This includes any of the popular FIDO based U2F (Universal Two Factor) hardware devices such as YubiKey or the new Google Titan USB security keys. Other options are an RSA token, or a proprietary offering by a site operator. This option was worth 3 points.
About 25% of the sites tested earned 5 stars, meaning that they offered the full array of 2FA options. The frightening fact is the were no 4 star or 3 star sites. This means that the remaining sites offered only one or two of the weaker methods (SMS/email or software token) for a single point, and too many offered nothing at all.
- 5 points – This is 25% of the sample. Kudos to Bank of America, Dropbox, E*TRADE, Facebook, Google, Stripe, Twitter, and Wells Fargo for leading the pack with 5 points each, which means they all offered all three of the tested methods.
- 4 points – None
- 3 points – None
- 2 points – This is 35% of the sample. Capital One, Evernote, Apple, Gemini, Coinbase, Instagram, Intuit (TurboTax), WhatsApp, Slack, GoDaddy, Square, Amazon, and Betterment. This group offered both SMS/email or a software token solution such as Google Authenticator.
- 1 point – This is 27% of the sample. These slackers only offered either SMS/email or a software token solution. Yahoo, Mint, Citibank, Discover, Airbnb, Chase, American Express, Venmo, and LinkedIn made this list. Yahoo and the financial service sites make me the queasiest.
- 0 points – And now for the losers who offer nothing in the way of two-factor authentication: Task Rabbit, NextDoor, BestBuy, and ZocDoc. This is 13% of the sample.
To see who is offering exactly what kind of 2FA support, check out the list on the Dashlane blog. Many popular websites were excluded from the report because it was not clear what sort of two-factor protections they offered, if any.
Personally, I found the report disturbing. I have been recommending 2FA and MFA solutions to my clients or years, but it seems like we are still waiting for many site operators to get off their backsides and implement something in addition to the password.
More information:
ShareNOV





About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com