 I am admittedly a huge proponent of two-factor and multi-factor authentication. For me, TFA, 2FA, and MFA have allowed the password some badly needed extended life as a secure authentication method. With multi-factor authentication, losing your password to an attacker is not enough for them to gain access to and compromise a system, resource, or account.
I am admittedly a huge proponent of two-factor and multi-factor authentication. For me, TFA, 2FA, and MFA have allowed the password some badly needed extended life as a secure authentication method. With multi-factor authentication, losing your password to an attacker is not enough for them to gain access to and compromise a system, resource, or account.
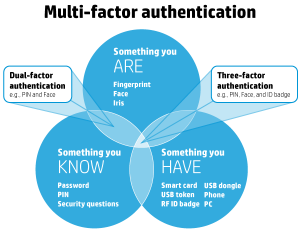
Multi-factor authentication requires a user to log into an account using two or more of the following factors:
- Something you know – This includes passwords, PINs, and KBA’s or knowledge-based answers to questions only you should know the answer to, such as grandma’s middle name.
- Something you have – Such as smartphone apps (Google Authenticator), RSA tokens, and USB security keys such as UbiKey.
- Something you are – AKA biometrics, these are finger, thumb, and palm prints, facial recognition, voice recognition, retinal or iris scans.
- Somewhere you are – A relative newcomer to MFA categories, this includes authentication by verifying your public IP address, or using GPS coordinates to confirm you are logging in from an approved location.
- Something you do – This newcomer includes actions that would be uniquely yours such as keyboard (typing) cadence and mouse movement patterns.
Stuart Schechter has written an article that examines some of the drawbacks or risks to using MFA, and how to mitigate those risks. We are summarizing some of those considerations below.
- Losing your second factor. – If you lose your phone with your authenticator app, or your RSA key or USB security key, you will not be able to log into your MFA protected accounts until you resolve the loss and replace your second factor. Even a dead phone battery could cause temporary access issues.
- Over-confidence. – You may become less concerned when you lose a password in a breach. You might not feel an urgent need to change a lost password. Or worse yet, you might fall back on old habits such as reusing the same password on several accounts, or using shorter, weaker passwords.
- Vulnerability to in-person attacks. – If someone you know (family, friend, coworker) has access to your second factor, they may be able to log in to your accounts using your password and security device. Or you may lose your phone, token or key to an attacker in a public place. If this person has already acquired your passwords using a keylogger, they would have access to your accounts, at least until you had a chance to shut them down.
Then there are issues with controlling access to your password. These include:
- Passwords lost in a data breach. – Through no fault of your own, one of your passwords is stolen by cyber-thieves and put up for sale on the Dark Web. Using Troy Hunt’s HaveIBeenPwned website can let you know if this has happened to any of your passwords.
- Phishing. – Phishing emails that link to credential-stealing replica login pages are a common way to lose a password. This can be more devastating if the attacker has focused in you exclusively.
- Malicious software. – Remote access Trojans and keyloggers can allow an attacker to acquire your passwords as you type them, or rummage around in your computer looking for password lists or log into your password manager app.
- Replay. – Once a bad actor has your password they can use it over and over, even from a different computer. If that password is for your email account, they can log into other accounts and request a password reset email to gain access to those accounts too.
- Change your security settings. – Once into an account, an attacker can change the security settings on the account to make it easier to log in a second time.
So there are definitely issues that can make using MFA a problem if things go awry. In our next post we will provide a plethora of solutions to help you use MFA more effectively and securely – even if things go wrong.
More information:
ShareOCT




About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com