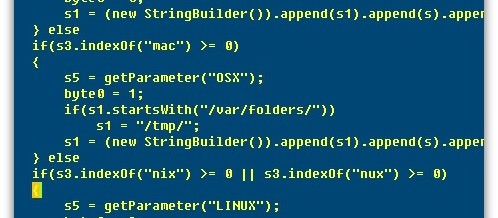
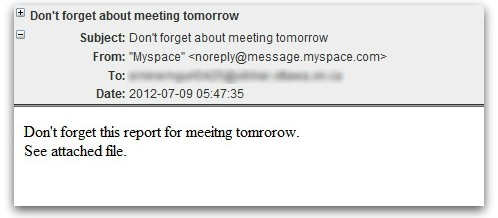
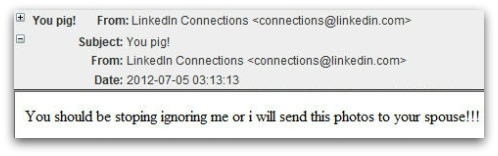
Microsoft has issued a security warning to users of the Gadget sidebar in Windows Vista and Gadgets in Windows 7. Gadgets are the little applets like a clock, news headline feed, or weather feed that can be added to the desktop area. Apparently a method has been developed to allow for the creation of custom gadgets, that when added to their computer system by users, would allow the providers of the gadget remote access and control of the computer, and ...
Continue Reading →JUL