Phishing Email Alerts for April Fool’s Day 2022
Catch of the Day: Wells Fargo Smish
Chef’s Special: Current Events Phish
Examples of clever phish that made it past my spam filters and into my Inbox, or from clients, or reliable sources on the Internet.
I would be delighted to accept suspicious phishing examples from you. Please forward your email to phish@wyzguys.com.
My intention is to provide a warning, examples of current phishing scams, related articles, and education about how these scams and exploits work, and how to detect them in your own inbox. If the pictures are too small or extend off the page, double-clicking on them will open them up in a photo viewer app.
Current Events Lead Phishing Attacks
Malicious email and phishing scams are usually topical and follow a pattern of current events. They are usually crafted around calendar and/or trending issues as attackers realize that victims are interested in all things relevant to the moment. Threat actors are aware that not all recipients will bite, but some will, hence the origination of the term “phishing.”
Included topics: IRS-themed tax scams, W-8 form submission via fax , Ukrainian war scams, and Bitcoin scams. More…
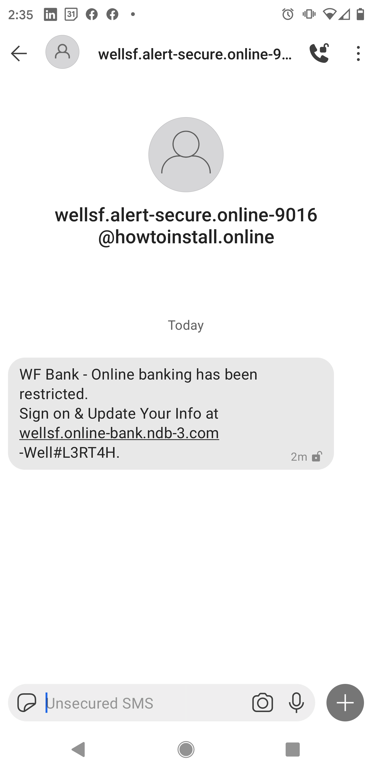
Wells Fargo Smishing Exploit
I’ve seen a variation of this attack in a traditional phishing email. This one arrived via the SMS text messaging app on my phone.
You have to be careful reading this link because it looks plausibly like a Bitly style short link. The actual domain is ndb-3.com, and online-bank and wellsf are subdomains. If I own a domain I can create as many subdomains as I need. But check out how realistic this looks in a couple of slides.
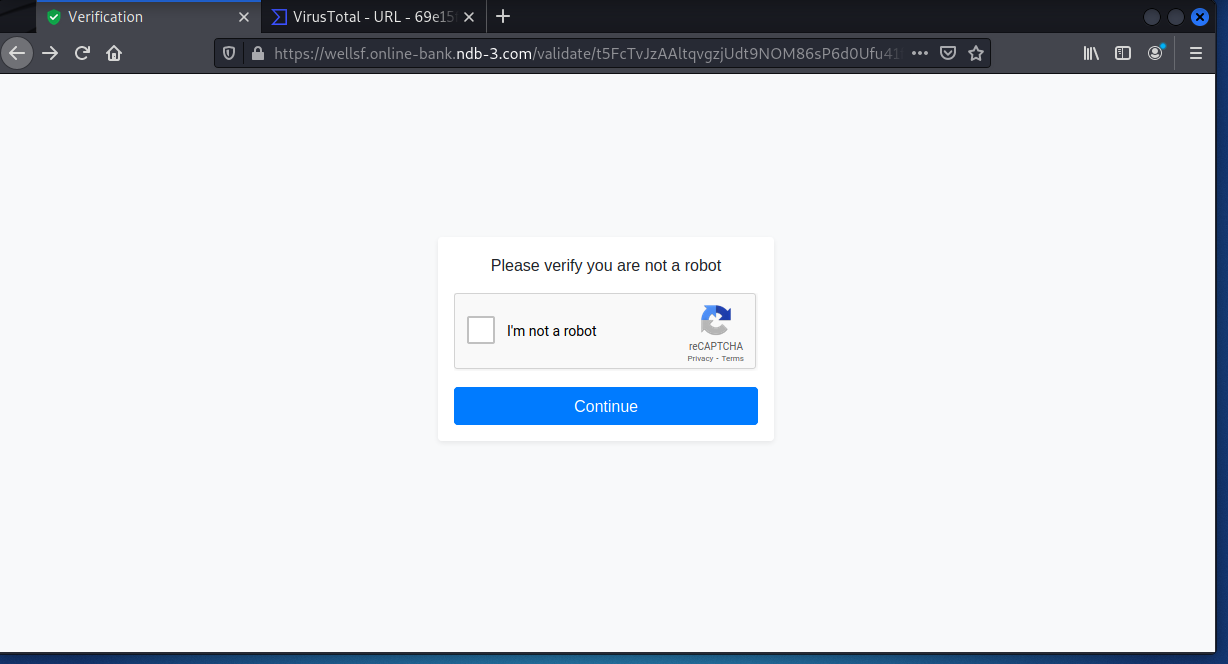
Here’s another hallmark of current phishing campaigns – the CAPTCHA panel. This of course lends a bit of realistic stagecraft to this exploit. I had to find all the motorcycles.
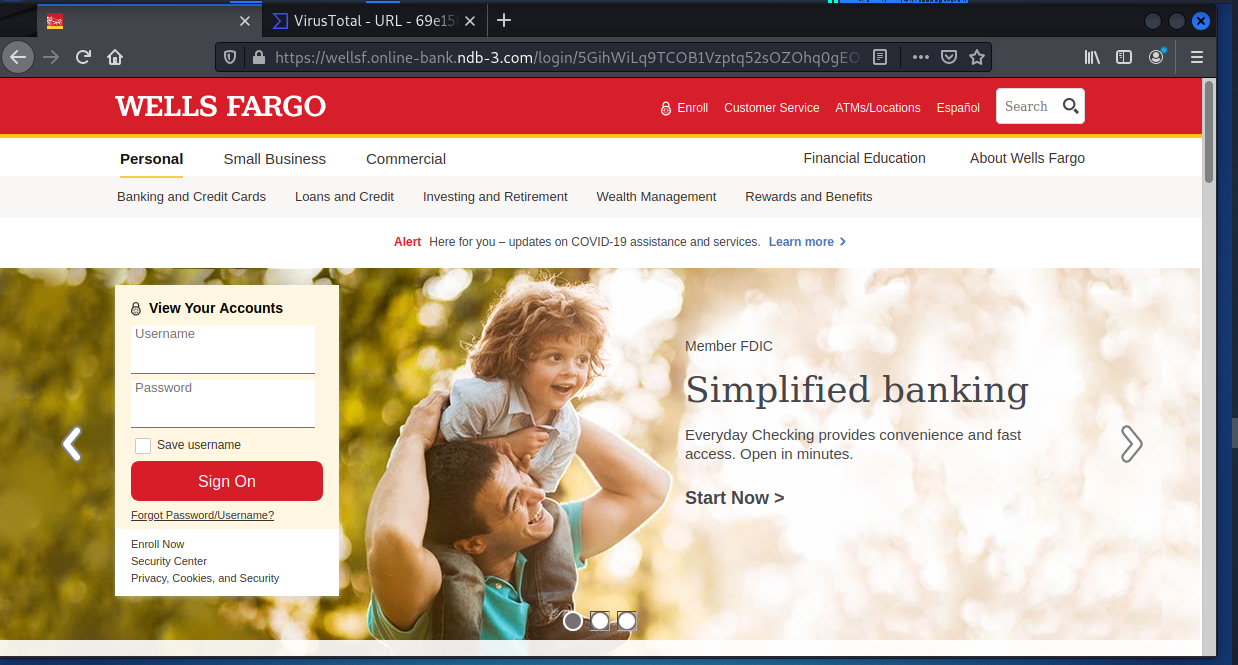
The CAPTCHA sends us to a very realistic Wells Fargo branded landing page. Just enter your user name and password and your credentials are sent to the attackers
But wait – there’s more. Now to collect some choice personal information
Ans why would wells Fargo need the password to my email account? With this information the attacker can engage in impersonation attacks against people on your contact list using your legitimate but compromised email account.
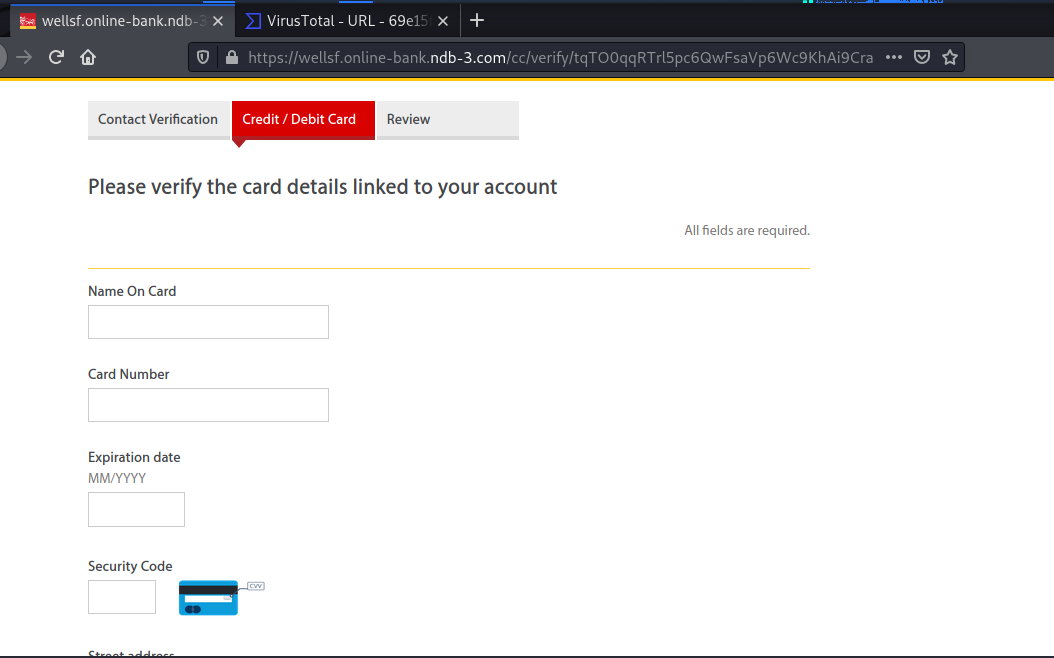
The next screen is as far as I could go, because it required the use of a real credit card number. I tried using variations and made-up CC numbers, but they are actually using credit card verification logic in their exploit code.
My assumption at this point is that the attackers would finally forward you to the legitimate Wells Fargo home page, just as they did in the Wells Fargo example I’ve show before in this blog. This allows them to cover their tracks and extend the life of the exploit.
Spoofed Invoice Used to Drop IcedID
Spearphishing crafted with industry-specific terms derived from intelligence gathering techniques to trick a recipient into opening a file is especially difficult to identify. This is especially true when an adversary has knowledge of how a business works and the processes that underpin it. Using this knowledge, a lure can be crafted that takes advantage of these day-to-day processes – for example, settling the cost of a fuel transaction.
FortiGuard Labs recently encountered such a scenario, where a fuel company in Kyiv, Ukraine received a spearphishing e-mail that contained an attached invoice—seemingly from another fuel provider—that was spoofed. The attachment is a zip file that contains the IcedID Trojan. More…
Morphisec Labs has detected a new wave of Remcos trojan infection. The theme of the phishing emails is again financial, this time as payment remittances sent from financial institutions. The attacker lures a user to open a malicious Excel file that contains “confidential information” which starts the infection chain.
Morphisec’s analysis has identified several services used for these phishing campaigns. They include Wells Fargo (see above example), FIS Global, and ACH Payment notifications. More…
Share
APR







About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com