Phishing Email Alerts
Catch of the Day: Wells Fargo Revisited
Examples of clever phish that made it past my spam filters and into my Inbox, or from clients, or reliable sources on the Internet.
I would be delighted to accept suspicious phishing examples from you. Please forward your email to phish@wyzguys.com.
My intention is to provide a warning, examples of current phishing scams, related articles, and education about how these scams and exploits work, and how to detect them in your own inbox. If the pictures are too small or extend off the page, double-clicking on them will open them up in a photo viewer app.
This week, my spam filters must be working better, no new phish at all! So this week I am going to repost the phishing exploit that is my very favorite. I had a student in one of my CISSP certification classes who worked at Wells Fargo say that this exploit is used in their employee cybersecurity awareness training. Share this with anyone you know with a Wells Fargo Account.
Wells Fargo Identity Theft Phish
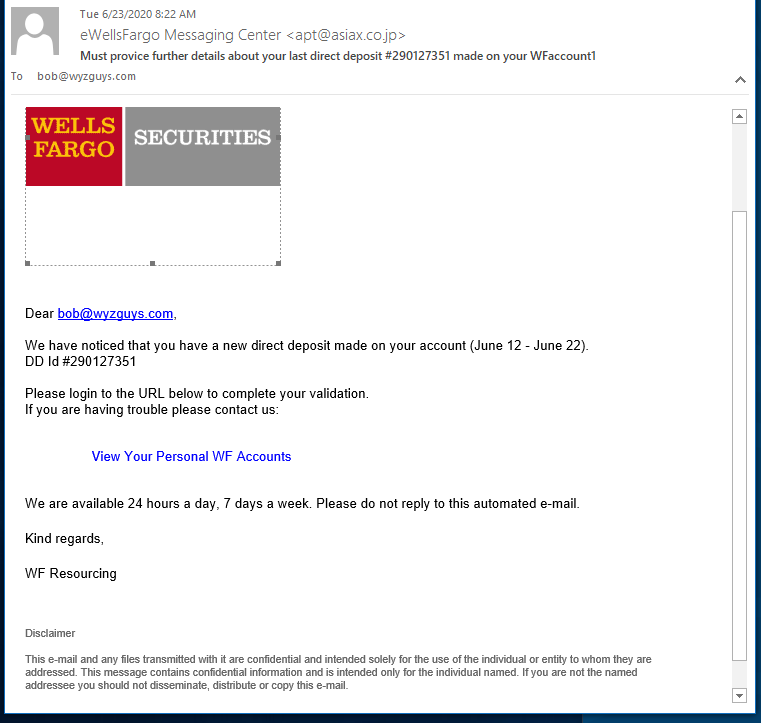
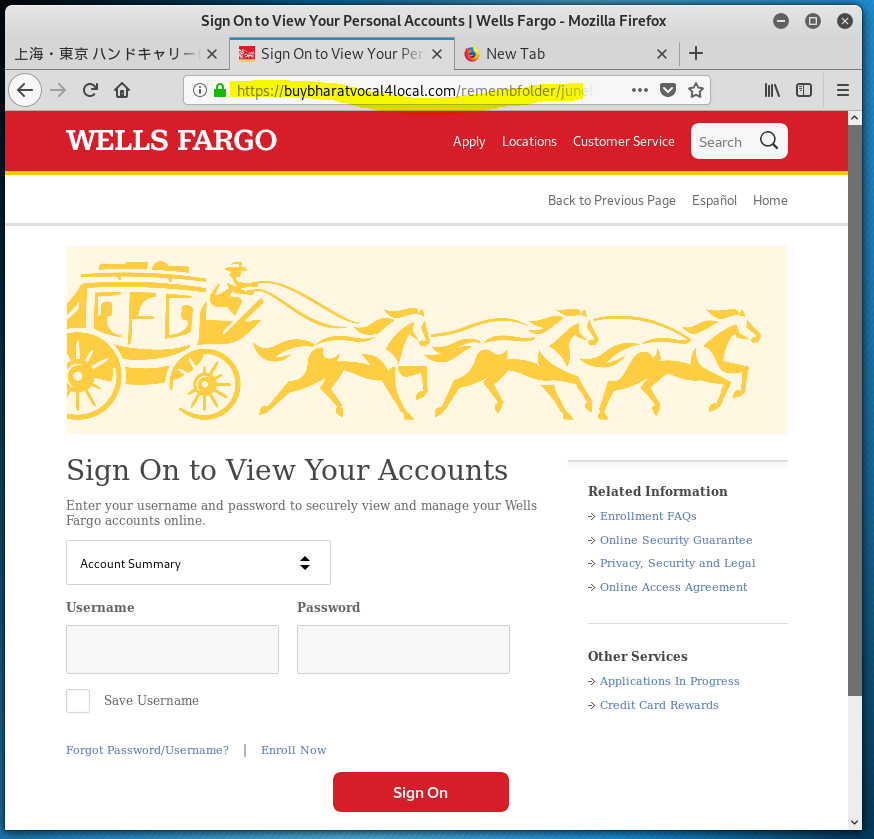
You don’t see one like this every day. This fabulously engineered phishing exploit starts out with good news, someone made a direct deposit in your account. Who doesn’t like free money? Click, and you’ve been pwned.
Not only does this phish want your Well Fargo Banking and Financial account credentials, but as I clicked through the multiple landing pages, this phishing exploit asked for personal information including street address, phone number, birth date, SSN, and driver’s license. On the next page they asked for credit card information. The fifth and final screen was an actual Wells Fargo login screen. If you followed all the way through, you coughed up every bit if information the attacker would need to log on to your Wells Fargo account and clean it out.
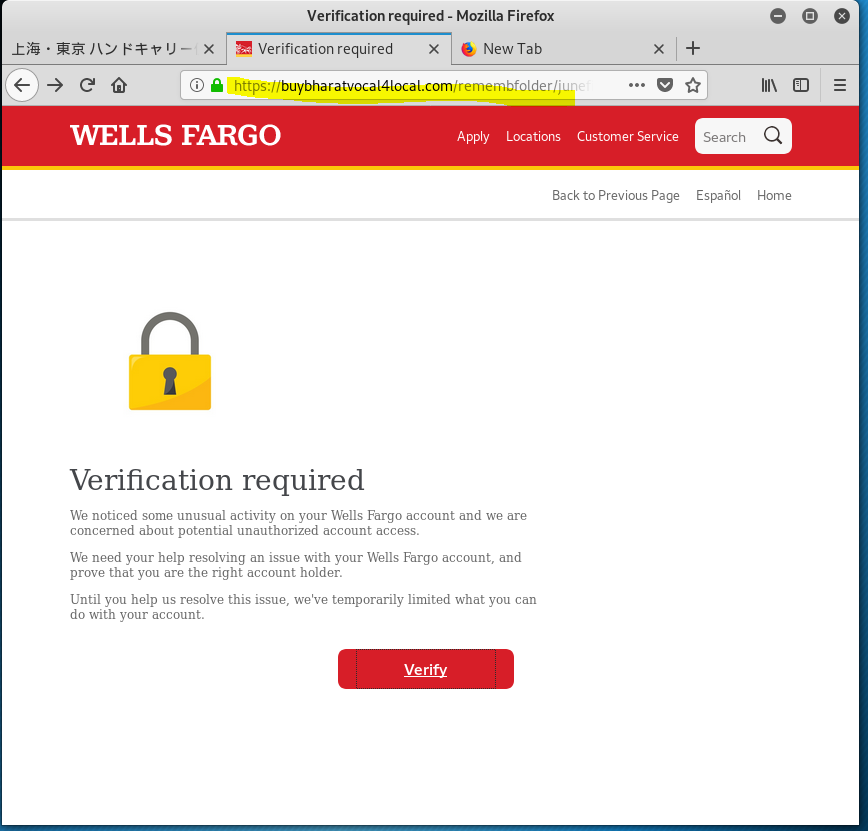
The email domain was hijacked from a Japanese air freight company. (WellsFargo Messaging Center <apt@asiax.co.jp>) The View Your Personal WF Accounts resolved to http://sagoodesign.com/firstgroupus. VirusTotal identified this as a phishing address. From there I was redirected to the first landing page at https://buybharatvocal4local.com/remembfolder/junefileswf/intro.html. From there I kept clicking, going deeper into this highly sophisticated identity theft and bank account hijacking exploit. The quality of the landing pages was very high, as you will see.
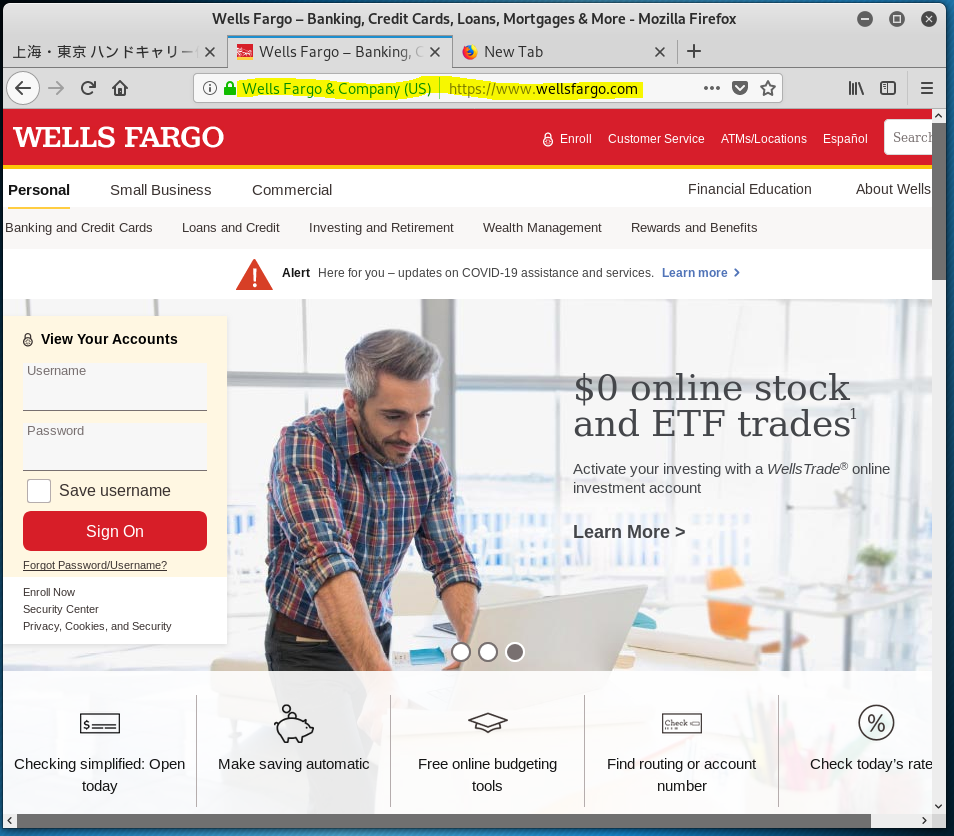
The website that is hosting these landing pages was hijacked. The last image in this case is the home page for https://buybharatvocal4local.com Buy Bharat V4L
The second landing page – user ID and password collected
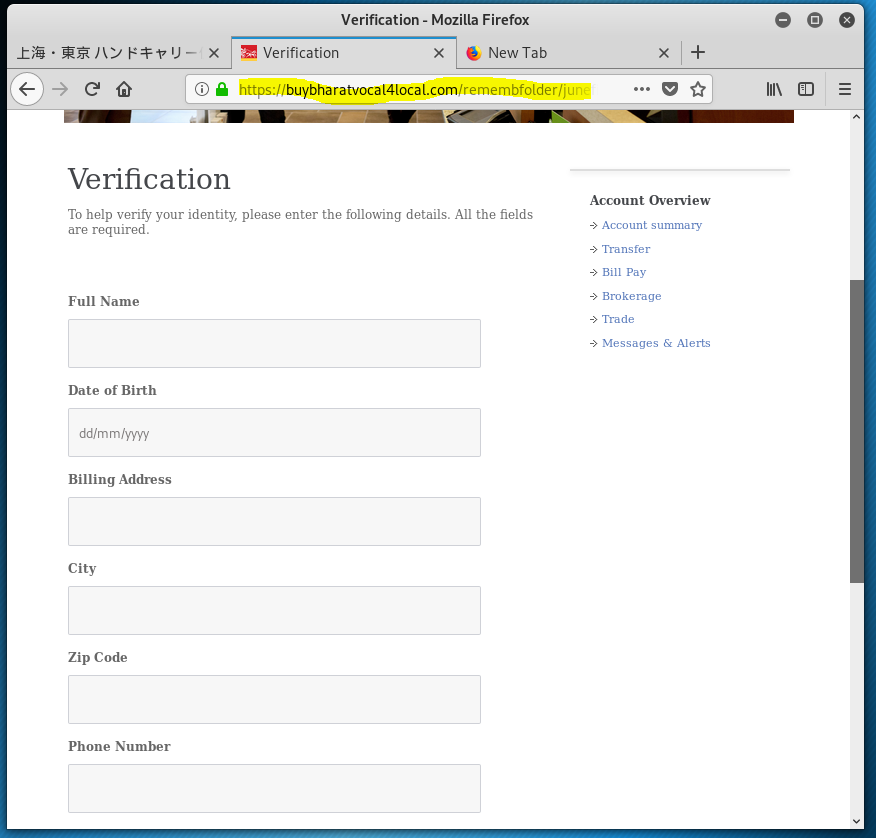
The third landing page – Name address, phone, birth date, SSN, and driver’s licence information collected.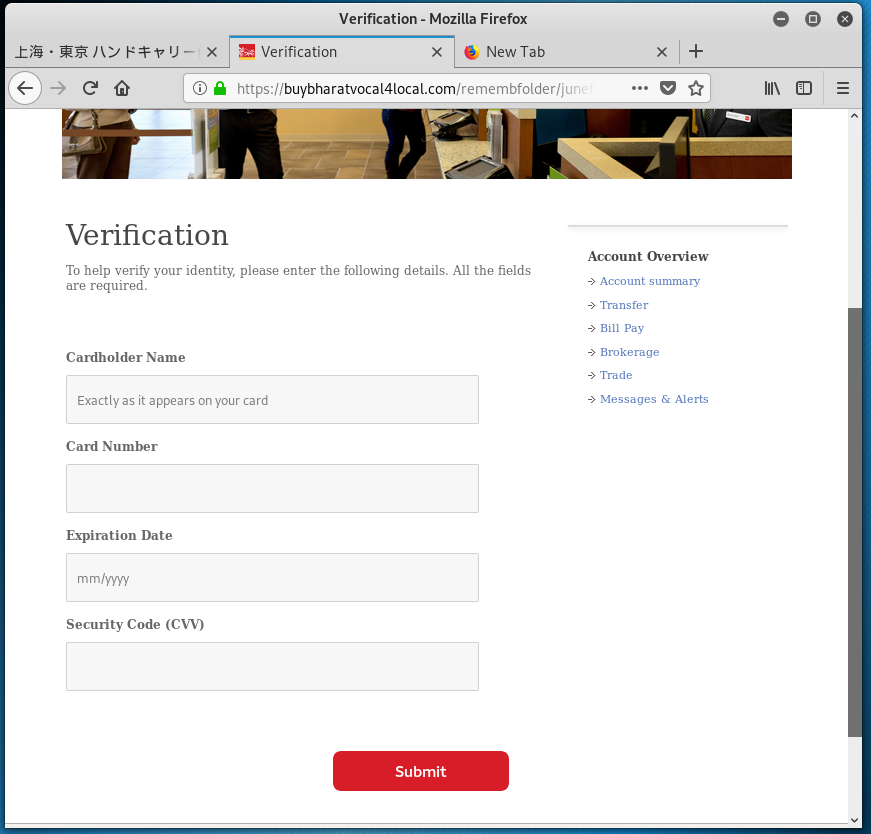
The fourth landing page – Got the credit card
The best for last – I was sent to a LEGITIMATE Wells Fargo login page.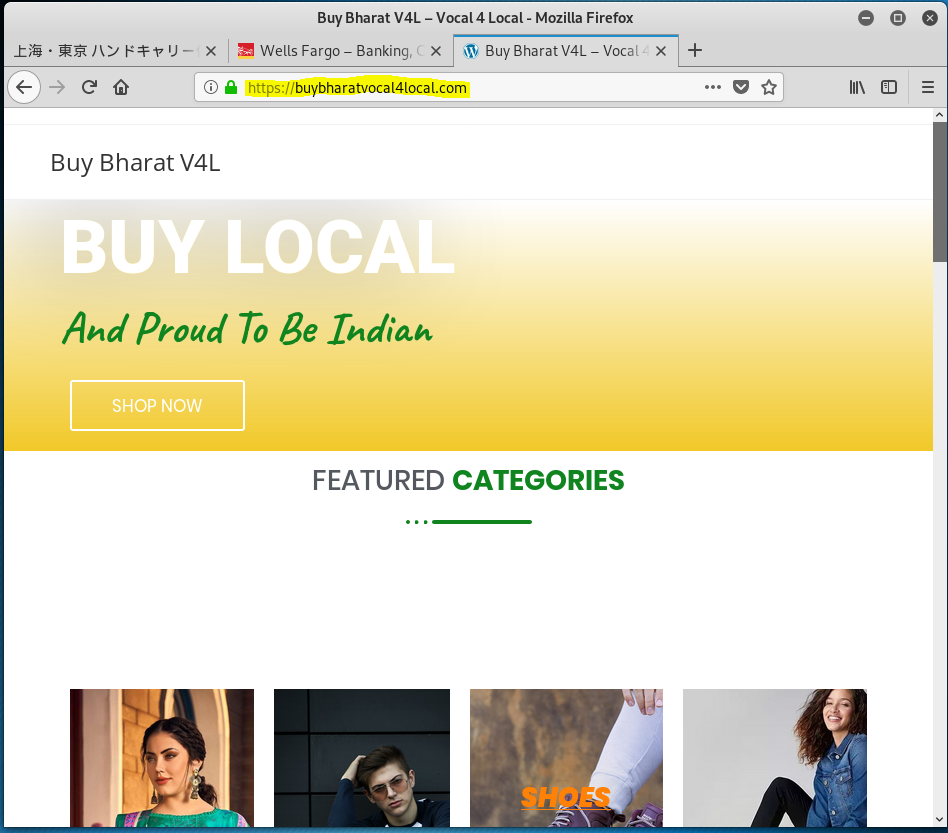
The victim website that is hosting the fake landing pagesThe is an excellent piece of social engineering. The perpetrator got the bank account, personal info, and a credit card – a trifecta!
ShareOCT






About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com