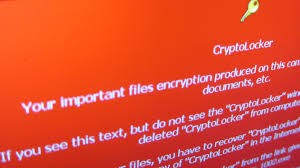
Are you are the owner of a business, or the CEO or other C-level employee? You are prime target for cyber-criminals. Specifically, your email account is a highly desirable target that can be used to impersonate you for invoicing, payment interception, or wire transfer fraud.
If you think you are too small to be a target, you are wrong. I worked on a case of a seven-person company whose owner had an MSN email account. They sent an invoice by email ...
Continue Reading →AUG