Are you are the owner of a business, or the CEO or other C-level employee? You are prime target for cyber-criminals. Specifically, your email account is a highly desirable target that can be used to impersonate you for invoicing, payment interception, or wire transfer fraud.
If you think you are too small to be a target, you are wrong. I worked on a case of a seven-person company whose owner had an MSN email account. They sent an invoice by email to a customer, and that email was followed by a second email with bank routing information that came from the attacker. The customer paid the attacker over $6000 in a wire transfer. Evidently this cyber-criminal was not very experienced, and the customer’s bank was able to retrieve the funds almost a week later. This is usually not the case. I have personally worked with companies who have lost amounts in the tens of thousands of dollars, and read of cases where losses were in the hundreds of thousands and even millions.
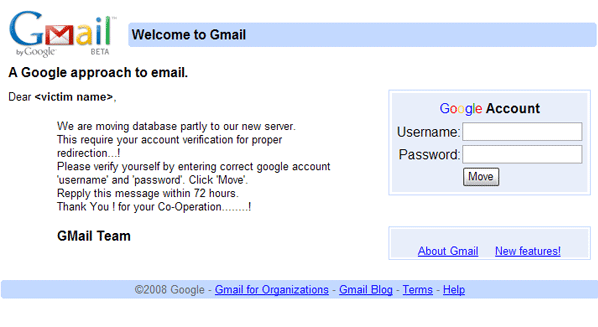
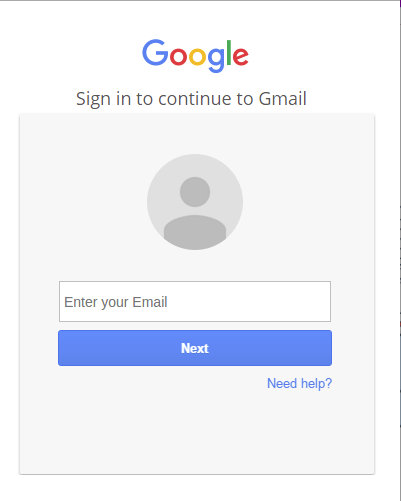
Here’s how it works. The first step is to gain control of your email account by acquiring your email password. This is typically achieved through the use of a phishing email designed to look like it came from your email provider. Usually there is a link to click, and the link will take you to a replica web page, called a landing page, where you are to enter your email address and password. The example shown does not even require a landing page, filling in the form on the email itself sends your credentials to the attacker. Passwords can also be purchased in list form on the Dark Web, so this can happen to you even without the phishing email.
Once they have the ability to log in to your account, they attacker will watch, read, and learn about you and your business. Depending on what they learn during the surveillance phase, they will move on to the attack phase. This can work a number of different ways, but understand that the emails the attacker sends will be coming from your legitimate email account, and this allows them to impersonate you. Monetizing the exploit will usually happen one of these ways:
- They will wait for you to invoice a client, and then follow your invoice email with an email containing bank routing instructions that will allow the attacker to capture the payment.
- They will create their own invoice with the necessary bank routing instructions, and send it to one or more of your clients.
- They will send an invoice to your accounts payable person that was forwarded from your email account. You (the boss) will be instructing the AP staff to pay the invoice. Often this happens without question from the AP staff.
- If you travel for business or pleasure, they will take advantage of your absence to send a wire transfer request to your CFO or other person in your company responsible for bank transactions. The request will be supported by a plausible scenario that may be known by your staff, such as the purchase of parts, supplies, or services, or the acquisition of another company.
Once payment is made to the bank account controlled by the attacker, the funds are usually sent through a series of bank accounts and may be eventually converted to BitCoin for some other untraceable funding service. After 24 hours, it is usually difficult or impossible to recovery the funds.
The attacker does not need to have staff or infrastructure to run this exploit, as is required for something like a ransomware exploit. This can be a solo operation, within the abilities of almost any cyber-criminal. This is why it has become the most popular and profitable exploit for cyber-criminals.
The easiest way to see if your account has been hijacked is to check the login locations on the security page of your email account. If someone is logging into your email account from an IP address in Pakistan or Vietnam, then you have probably been hacked. The solution is to change your password, and update all of the security information. While you are at it, look for any unexplained email forwarders to other email accounts that don’t belong to you.
I covered this issue in a four part series last month, and you can read more about this exploit at the following links.
More information:
- What Can I Do With A Hijacked Email Account? Part 1
- What Can I Do With A Hijacked Email Account? Part 2
- Email Account Hijacking – Part 3 Extending the Exploit
- Email Account Hijacking – Part 4 Prevention and Dectection
AUG




About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com