 Last week we went deep on the subject of just how bad losing control of your email account can be. Today we are wrapping up the four-part series with solutions to help you prevent email account compromise from happening, how to detect if it has already happened to you, and how to recover if that is the case.
Last week we went deep on the subject of just how bad losing control of your email account can be. Today we are wrapping up the four-part series with solutions to help you prevent email account compromise from happening, how to detect if it has already happened to you, and how to recover if that is the case.
Prevention is the best solution. Your email account is one of the crown jewels of your online life, and needs to be protected accordingly. Here is a list of my recommendations
- Never click on an email link – When you get an email that looks like it came from your email service, do not click on the link. Just log into your account the normal way, usually from a saved bookmark on your browser toolbar. If you don’t click the link, you can’t be tricked by the fake landing page. This works for any online account or service provider.
- Password length – In a world where passwords are cracked by machines, length is strength. Make sure your email password is at least 12 characters long.
- Two-factor authentication – Most email service providers offer two-factor authentication, also called 2FA or TFA. Sign in to your email account settings (Click on your avatar in the upper right corner.) Find the security settings from the menu. Then activate 2FA on your account. When you log in with your user ID and password, 2FA will provide a 6 digit one-time passcode to enter on the second log-in screen, usually via SMS to your smart phone. Your attacker now needs both your password and your phone to log in to your account. Leave the security page open, we will be back.
- Set up account recovery options –
- Recovery email address -You will need a recovery email address on another service. Most of us already have at least two. Android phone owners get a Gmail account whether you need it or not.
- Recovery phone number – Now add a recovery phone number or even two.
- Secret recovery questions – Then set up your secret questions and answers. I have friends who provide fake answers to make this impossible to crack through online research. (Your grandfather’s middle name is on Ancestry.com) Just keep track of your answers if you choose to make them up. In the event your account is compromised, or you just forget your password, you will need these avenues of recovery.
Early detection is your next best option. These tips will help you stay in control.
 Set up security alerts – You can have your email service provider notify you by email or text message every time there is a log-in to your account. You want to turn this on. Yes, you will get an alert every time you log in. But if someone logs into your email account from Bulgaria, you will be notified immediately, and can take steps to change your password and recover your account.
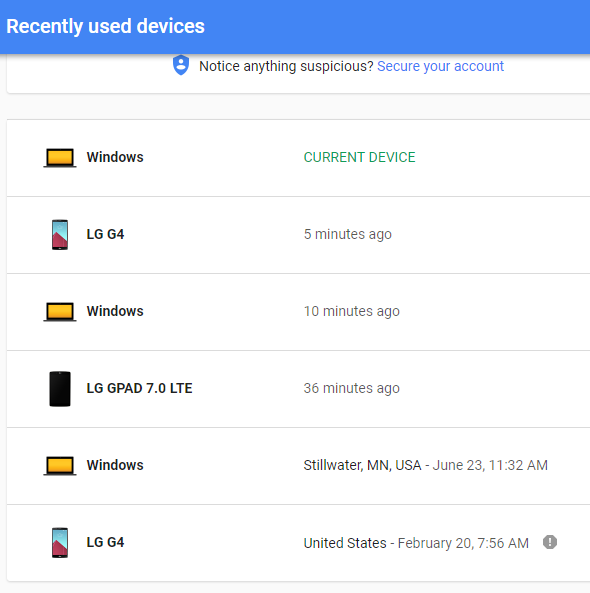
Set up security alerts – You can have your email service provider notify you by email or text message every time there is a log-in to your account. You want to turn this on. Yes, you will get an alert every time you log in. But if someone logs into your email account from Bulgaria, you will be notified immediately, and can take steps to change your password and recover your account.- Check recent usage – Google, Yahoo, and most other email service providers will keep track of recent log-ins by device type, IP address, geographical location, and connection date and time. On the first image to the right (Gmail),
 the last item LG G4 has an exclamation point. This is an old phone I no longer have, but Google flagged it because it hadn’t logged in lately. I had an option to remove the device.
the last item LG G4 has an exclamation point. This is an old phone I no longer have, but Google flagged it because it hadn’t logged in lately. I had an option to remove the device.
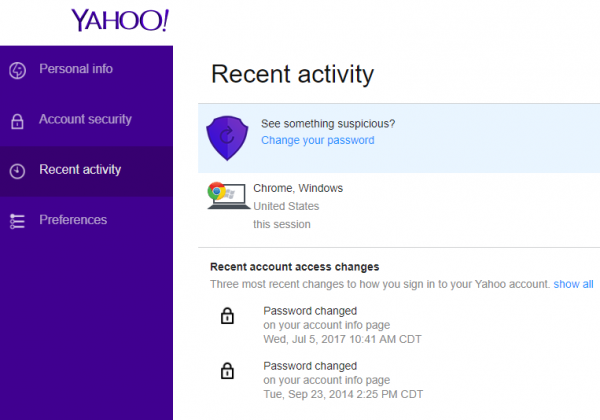
On the Yahoo example, clicking on the connection revealed most of the details. It also showed that I had recently changed my account password. If log-ins and password changes show up when you haven’t been in your account, that is an indication that your account has been accessed by another and is now compromised. If someone logs into your account from a foreign country, or event another city, that is another indication of compromise.
In the event your account has been hacked, change the password and secret question information. It is always a good idea to report the attack to the security or abuse email address for your service provider. Filing a report at the FBI’s Internet Crime Complaint Center can be a good idea as well.
And thanks for sticking with me, I hope you found this series of articles informative and beneficial.
More information:
Share
JUL




About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com