 A quick Saturday digest of cybersecurity news articles from other sources.
A quick Saturday digest of cybersecurity news articles from other sources.
Senate renews warrantless collection of web histories
Does all this COVID-19 related ruling by Executive Order give you the Constitutional willies? Well, the Legislative Branch is doing its best to keep pace in the race to see which branch of the government can violate our rights the most. The government can keep on surveilling your online life without a warrant. An amendment to ban it failed by just one vote in the Senate. Only the House can end this intrusion into our private lives.
PrintDemon – patch this ancient Windows printer bug!
Bugs can last a long time… even if you thought you removed them years ago.
Update now! Windows gets another bumper patch update
After a flurry of zero-day vulnerabilities in recent editions, May’s Patch Tuesday finally gives Windows users a month off having to fix ‘big’ exploited or public flaws. The catch is it’s still one of the biggest patch rounds Microsoft has ever released, featuring 111 CVE-level bug fixes (the record being March’s 115 fixes), nearly half of which are in Windows itself.
A Huge Hunk of Space Debris Fell to Earth
The 20-ton object, part of a Chinese rocket, is one of the largest ever to fall uncontrolled from space. My comment: What- bio-war isn’t bad enough? Now the Chinese attack us from space?
Mirai and Hoaxcalls Botnets Target Legacy Symantec Web Gateways
As part of Unit 42’s efforts to proactively monitor threats circulating in the wild, I recently came across new Hoaxcalls and Mirai botnet campaigns targeting a post-authentication Remote Code Execution vulnerability in Symantec Secure Web Gateway 5.0.2.8, which is a product that became end-of-life (EOL) in 2015 and end-of-support-life (EOSL) in 2019. There is no evidence to support any other firmware versions are vulnerable at this point in time and these findings have been shared with Symantec. They confirmed the currently exploited vulnerability is no longer present in Symantec Web Gateway 5.2.8. Symantec also wanted to emphasize the point that this vulnerability does not impact Secure Web Gateway solutions, including ProxySG and Web Security Services.
Vendetta New Threat Actor from Europe
Starting in April this year, 360 Baize Lab intercepted a large number of attack samples from an unknown hacker organization. The hacker organization sent a phishing email to the victim by forging a police station investigation letter, COVID-19 detection notice, etc. , Through the backdoor virus to control the victim’s machine, steal valuable sensitive data related to the target. The PDB path of the virus samples used by the organization points to a user named “Vendetta”, and we will later also name the hacker organization Vendetta.
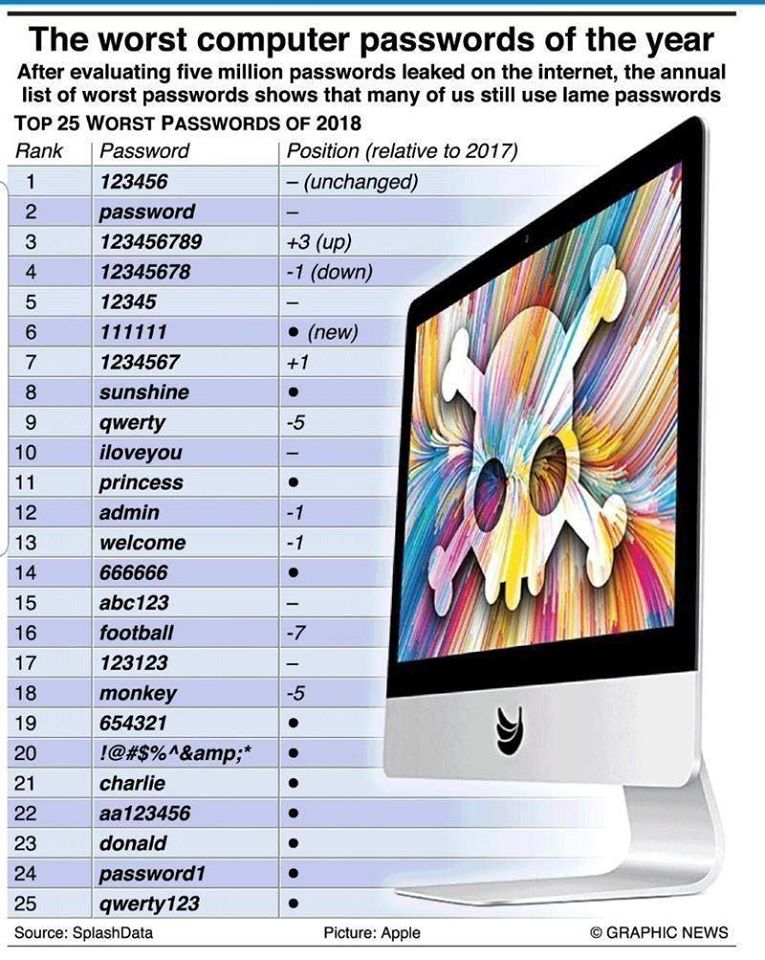
Worst Passwords
Celebrity Cyber Extortion: Law Firm to the Stars Hit by Ransomware Attack
A long list of powerful stars and media companies are nervous right now, wondering if their legal dealings might soon be spilled onto the web for the world to see. And if a hacker group’s claims are true, there seems to be only one way around it: the celebrity lawyers must pay a ransom. You might call it the ultimate Hollywood hush-money payment. The law firm is based in New York, with a client list that extends from Broadway to Beverly Hills. Cybercriminals hit Grubman, Shire, Meiselas & Sacks in early April with a strain of ransomware called REvil, a key feature of which is its ability to exfiltrate data to use as extortion—as in, pay up or we’ll publish your stuff. In fact, entertainment publication Variety says the hackers have already started by leaking a page from one of Madonna’s contracts—one piece of 756 MB worth… Read more
Managed Service Provider Cognizant CEO Details Ransomware ‘Perfect Storm’
Talk about kicking a company when it’s down. First, the coronavirus pandemic cuts into profits. Then, a ransomware attack adds tens of millions in financial damage to your company, followed by a hit on your roll out of work-from-home for the team. This is Cognizant’s story, revealed in its recent earnings call. The world’s largest IT managed services firm confirmed in mid-April it was hit with Maze… Read more
World’s Largest Sovereign Wealth Fund Falls for 10 Million Social Engineering Attack
The Norwegian Investment Fund has been swindled out of 10 million dollars by fraudsters who pulled off a social engineering attack that the Norfund called “an advanced data breach” but what is commonly known as a Business Email Compromise, aka CEO fraud.
Norfund is the world’s largest sovereign wealth fund—created from saved North Sea Oil revenues and currently worth over a trillion dollars— admitted that a hacker was able to manipulate the organization into routing a loan intended for a Cambodian microfinance organization into an account controlled by cyber criminals.
As a result, in March, 100m Kroner was lost. The investment fund says the money appears to have been diverted from the organization in Cambodia to Mexico. Local and international police have been brought in to investigate the matter. There are not yet a lot of details about this attack, which may have been a simple compromised email account, perhaps several pwned workstations fully under control of the bad guys, or a fully compromised network. Read more…
MAY




About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com