 A quick Saturday digest of cybersecurity news articles from other sources.
A quick Saturday digest of cybersecurity news articles from other sources.
Windows 11: Understanding the system requirements and the security benefits
Security is a big part of Windows 11, but so is delivering productivity and a good experience with all the security features turned on.
Kaseya VSA Supply-Chain Ransomware Attack
Original release date: July 2, 2021
CISA is taking action to understand and address the recent supply-chain ransomware attack against Kaseya VSA and the multiple managed service providers (MSPs) that employ VSA software. CISA encourages organizations to review the Kaseya advisory and immediately follow their guidance to shutdown VSA servers.
(Note from the WyzGuy – Kaseya is a Remote Monitoring and Management (RMM) tool use by many managed service providers (MSP). Critically, this tool provides remote access and remote control of client computer systems. Kind of a bigger attack. Ask you MSP if they use Kaseya and what they are doing about this attack.)
CISA-FBI Guidance for MSPs and their Customers Affected by the Kaseya VSA Supply-Chain Ransomware Attack
Original release date: July 4, 2021
CISA and the Federal Bureau of Investigation (FBI) continue to respond to the recent supply-chain ransomware attack leveraging a vulnerability in Kaseya VSA software against multiple managed service providers (MSPs) and their customers. CISA and FBI strongly urge affected MSPs and their customers to follow the guidance on their web site.
PrintNightmare, Critical Windows Print Spooler Vulnerability
Original release date: June 30, 2021
The CERT Coordination Center (CERT/CC) has released a VulNote for a critical remote code execution vulnerability in the Windows Print spooler service, noting: “while Microsoft has released an update for CVE-2021-1675, it is important to realize that this update does not address the public exploits that also identify as CVE-2021-1675.” An attacker can exploit this vulnerability—nicknamed PrintNightmare—to take control of an affected system.
CISA encourages administrators to disable the Windows Print spooler service in Domain Controllers and systems that do not print. Additionally, administrators should employ the following best practice from Microsoft’s how-to guides, published January 11, 2021: “Due to the possibility for exposure, domain controllers and Active Directory admin systems need to have the Print spooler service disabled. The recommended way to do this is using a Group Policy Object.”
SMB Worm “Indexsinas” Uses Lateral Movement to Infect Whole Networks
This is a serious crypto-mining exploit. Guardicore Labs exposes new details of a massive attack campaign dubbed Indexsinas (also known as “NSABuffMiner”) which breaches networks through SMB servers and makes aggressive use of lateral movement to propagate. The attack campaign targets Windows servers vulnerable to EternalBlue (MS17-010) and still infects machines worldwide.
The Mirai Botnet Attack and Revenge of the Internet of Things
Once upon a time in early 2016, we were talking with pen tester Ken Munro about the security of IoT gadgetry — everything from wireless doorbells to coffee makers and other household appliances. I remember his answer when I asked about basic security in these devices. His reply: “You’re making a big step there, which is assuming that the manufacturer gave any thought to an attack from a hacker at all.” More…
NSA-CISA-NCSC-FBI Joint Cybersecurity Advisory on Russian GRU Brute Force Campaign
Original release date: July 1, 2021
The National Security Agency (NSA), Cybersecurity and Infrastructure Security Agency (CISA), Federal Bureau of Investigation (FBI), and the UK’s National Cyber Security Centre (NCSC) have released Joint Cybersecurity Advisory (CSA): Russian GRU Conducting Global Brute Force Campaign to Compromise Enterprise and Cloud Environments.
The CSA provides details on the campaign, which is being conducted by the Russian General Staff Main Intelligence Directorate (GRU) 85th Main Special Service Center (GTsSS). The campaign uses a Kubernetes® cluster in brute force access attempts against the enterprise and cloud environments of government and private sector targets worldwide. After obtaining credentials via brute force, the GTsSS uses a variety of known vulnerabilities for further network access via remote code execution and lateral movement.
CISA strongly encourages users and administrators to review the Joint CSA for GTSS tactics, techniques, and procedures, as well as mitigation strategies.
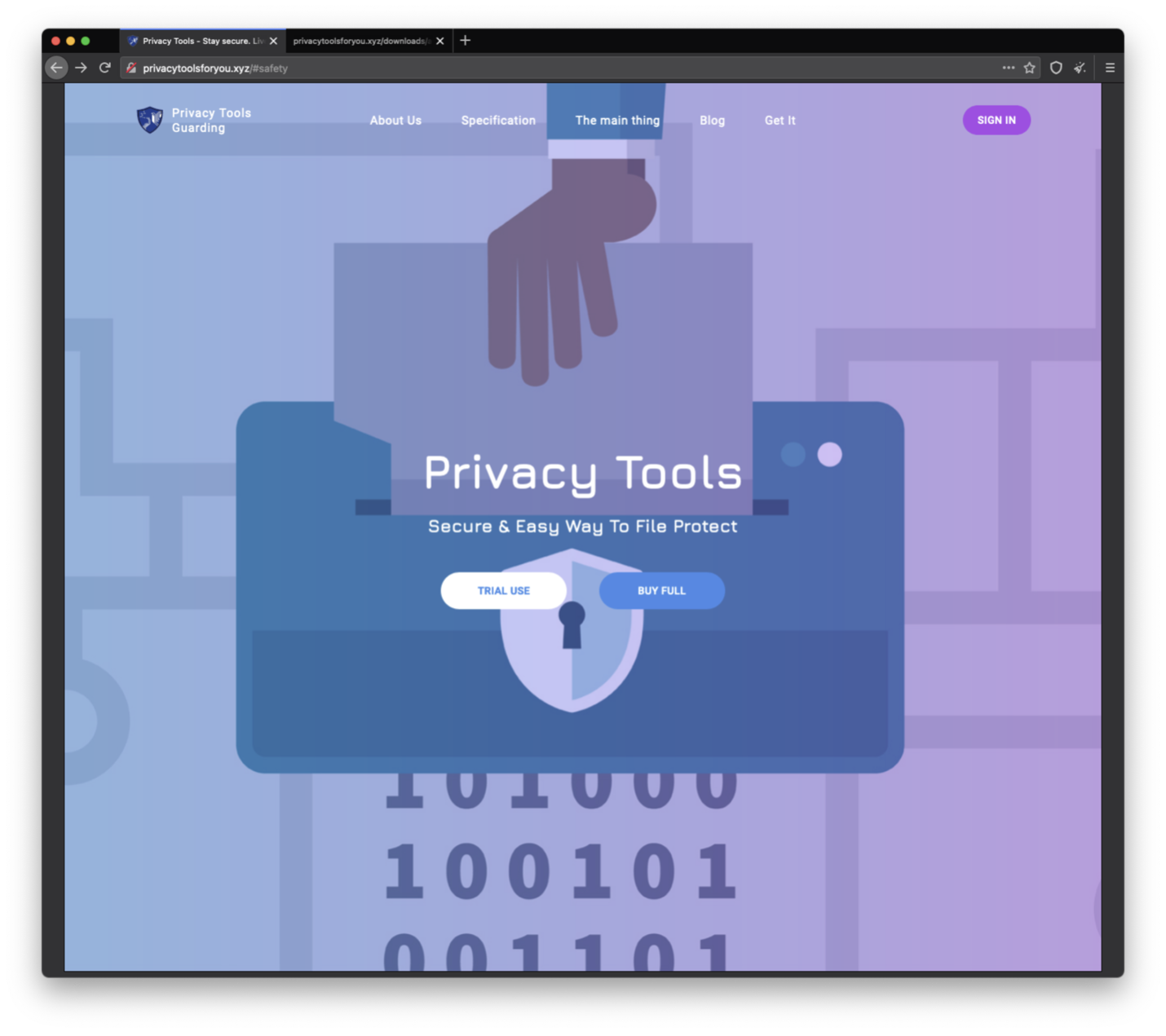
Malware Masquerades as Privacy Tool
- Threat actors created a detailed, legitimate looking “Privacy Tools” website to trick victims into downloading malware.
- The Privacy Tools site purports to offer file protection via encryption and decryption services but leads to the installation of multiple malware families.
- Smoke Loader is downloaded first as the malicious executable which drops follow-on malware including Racoon Stealer and RedLine malware.
Fake Privacy Tools website shown below. More…
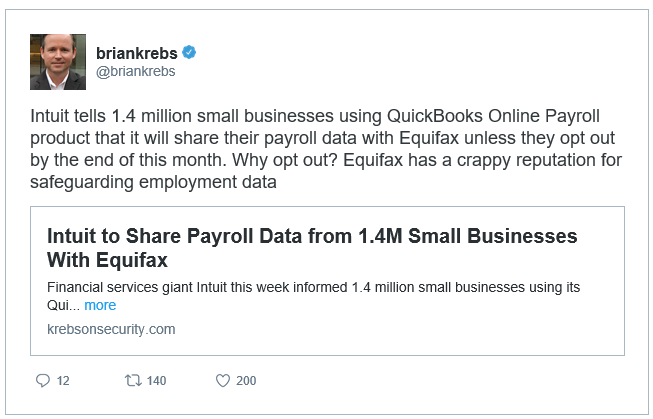
Intuit to Share Payroll Data from 1.4M Small Businesses With Equifax
Thanks Intuit! Are you nuts? This should be strictly OPT-IN not OPT-OUT. For the following reasons.
- Federal Trade Commission Fines Equifax and Facebook
Hot on the heals on each other, Equifax and Facebook have each settled for large fines in unrelated privacy and data breach cases. All I can say is “about time” and “is that all?” The FTC has fined Facebook $5 billion for data misuse and other issues related to Cambridge Anal…
- What You Can Do After The Equifax Breach
Wanted for insider trading and consumer fraud, and impersonating someone who gives a damn about information security. The Equifax breach has been all over the news this weekend, and it should be. This is worse than they are telling us. It most certainly DOES affect you, if you are adult and ha…
Share
JUL




About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com