 A quick Saturday digest of cybersecurity news articles from other sources.
A quick Saturday digest of cybersecurity news articles from other sources.
BlueBorne Bluetooth Vulnerabilities
09/12/2017 05:26 PM EDT Original release date: September 12, 2017
US-CERT is aware of a collection of Bluetooth vulnerabilities, known as BlueBorne, potentially affecting millions of unpatched mobile phones, computers, and Internet of Things (IoT) devices. A remote attacker could exploit several of these vulnerabilities to take control ...
Continue Reading →OCT





 I am a firm believer in, and user of two-factor authentication (TFA or 2FA). Heck, if there was three-factor authentication I would probably sign up. The two most popular authenticator apps are Authy and Google Authenticator. I primarily use Google Authenticator wherever I can. I use SMS when Authenticator isn’t an option, or won’t work. I had trouble, for instance, getting Facebook to work ...
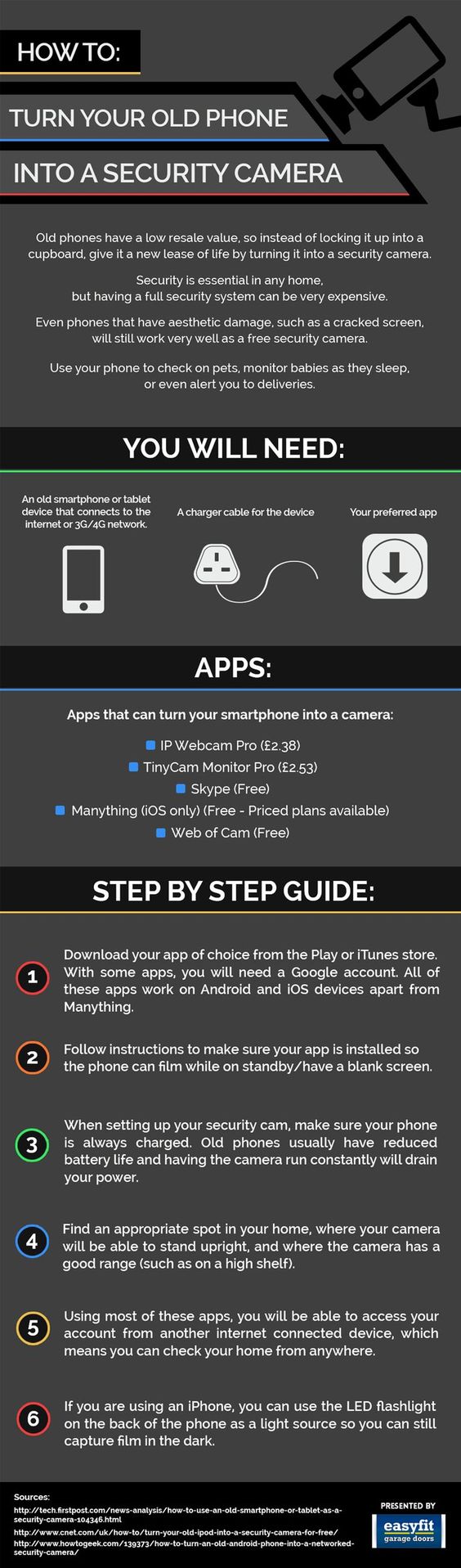
I am a firm believer in, and user of two-factor authentication (TFA or 2FA). Heck, if there was three-factor authentication I would probably sign up. The two most popular authenticator apps are Authy and Google Authenticator. I primarily use Google Authenticator wherever I can. I use SMS when Authenticator isn’t an option, or won’t work. I had trouble, for instance, getting Facebook to work ... Mobile smart devices have all the capabilities of a laptop or computer. What this means from a cybersecurity perspective is that they are every bit as vulnerable as a laptop or desktop computer. The fact that they are small makes them easy for a thief to slip in a pocket or backpack and carry away, along with your personal information, contacts, pictures, geo-location history, and a raft of critical and revealing ...
Mobile smart devices have all the capabilities of a laptop or computer. What this means from a cybersecurity perspective is that they are every bit as vulnerable as a laptop or desktop computer. The fact that they are small makes them easy for a thief to slip in a pocket or backpack and carry away, along with your personal information, contacts, pictures, geo-location history, and a raft of critical and revealing ...