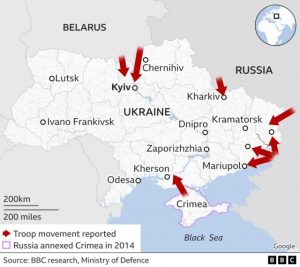
 Remember NotPetya? This was a campaign by the Sandworm APT in Russia the last time Russia invaded the Ukraine. It deleted hard drives around the world before it was through. There is a new variant call the HermeticWiper being deployed against Ukrainian business targets that has the same danger of spilling over into the rest of the world. Here are a couple of articles to check out.
Remember NotPetya? This was a campaign by the Sandworm APT in Russia the last time Russia invaded the Ukraine. It deleted hard drives around the world before it was through. There is a new variant call the HermeticWiper being deployed against Ukrainian business targets that has the same danger of spilling over into the rest of the world. Here are a couple of articles to check out.
Alert (AA22-057A)
Destructive Malware Targeting Organizations in Ukraine
Leading up to Russia’s unprovoked attack against Ukraine, threat actors deployed destructive malware against organizations in Ukraine to destroy computer systems and render them inoperable.
- On January 15, 2022, the Microsoft Threat Intelligence Center (MSTIC) disclosed that malware, known as WhisperGate, was being used to target organizations in Ukraine. According to Microsoft, WhisperGate is intended to be destructive and is designed to render targeted devices inoperable.
- On February 23, 2022, several cybersecurity researchers disclosed that malware known as HermeticWiper was being used against organizations in Ukraine. According to SentinelLabs, the malware targets Windows devices, manipulating the master boot record, which results in subsequent boot failure.
For TTPs and IOCs click through to the rest of the CISA alert
From KnowBe4
The Ukraine War Started A New Wiper Malware Spillover Risk
The war in Ukraine increases the risk of wiper malware to spill over. I’m sure you remember NotPetya, which caused billions of dollars of downtime damage. The WSJ reports that Symantec observed wiper malware was put in motion just hours before Russian tanks arrived in Ukraine.
The WSJ said: “The wiper malware—this version is being called HermeticWiper by researchers—could mark an escalation in cyberattacks against various Ukrainian targets, security experts said. Websites of government agencies and banks were disrupted on Wednesday, and on Thursday, that of the Kyiv Post, an English-language newspaper.”
“On Wednesday, Slovakia-based cyber firm ESET said it also detected the wiper strain on hundreds of machines in Ukraine, adding that timestamps indicated the malware had been created nearly two months ago in preparation for deployment.”
The WSJ noted that “On Thursday morning, CISA Director Jen Easterly tweeted a Wired magazine article on the 2017 NotPetya hack, which emanated from a Ukrainian accounting firm and caused billions in lost sales and other damage to businesses including FedEx Corp. and Merck & Co. Inc.”
“While there are no specific threats to the U.S. at this time, all orgs must be prepared for cyberattacks, whether targeted or not,” Ms. Easterly wrote.
So, we strongly recommend to:
- Make sure your backups work and test your restore function, not for just files but whole servers
- Patch all known vulnerabilities and test the patches
- Deploy strong MFA to as many employees as you can (some MFA can be easily circumvented)
- Step all employees through at least a 15-minute security awareness training module to keep them on their toes with security top of mind
And it pains me to say, that while you are at it, warn your users: Criminals will start new, devious charity campaigns that claim to help people in Ukraine. Remind your users to –only– use legit charities they are already familiar with and to never click on a link in an email of a charity claiming to help Ukraine war victims.
Blog post with links:
https://blog.knowbe4.com/heads-up-the-ukraine-war-started-a-new-wiper-malware-spillover-risk
MAR




About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com