 On Wednesday we took a look at Facebook scams. But what about LinkedIn? Because of LinkedIn’s professional focus, the scams are a little different, but use many of the same tactics. LinkedIn scams are more likely to draw on information from your professional profile, and tend to be employment or income related. Here they are:
On Wednesday we took a look at Facebook scams. But what about LinkedIn? Because of LinkedIn’s professional focus, the scams are a little different, but use many of the same tactics. LinkedIn scams are more likely to draw on information from your professional profile, and tend to be employment or income related. Here they are:
- Whaling attacks – What?! We have talked about phishing and spearphishing, ...
SEP

 Everybody, it seems, is on Facebook, and the numbers back it up, with over 1 billion members worldwide. So naturally, anytime you get a crowd of people this large, the cyber-criminals are going to be all over it.
Everybody, it seems, is on Facebook, and the numbers back it up, with over 1 billion members worldwide. So naturally, anytime you get a crowd of people this large, the cyber-criminals are going to be all over it. We warned our readers about the
We warned our readers about the 
 Phishing is still the overwhelming go-to choice for cyber-criminals launching an attack. Over 90% of computer system breaches start with a phishing email in an inbox. Finding ways to unmask these impostors is a good first step are protecting yourself from a phishing exploit. Let’s look at this first example, apparently from a law firm about a legal action.
Phishing is still the overwhelming go-to choice for cyber-criminals launching an attack. Over 90% of computer system breaches start with a phishing email in an inbox. Finding ways to unmask these impostors is a good first step are protecting yourself from a phishing exploit. Let’s look at this first example, apparently from a law firm about a legal action.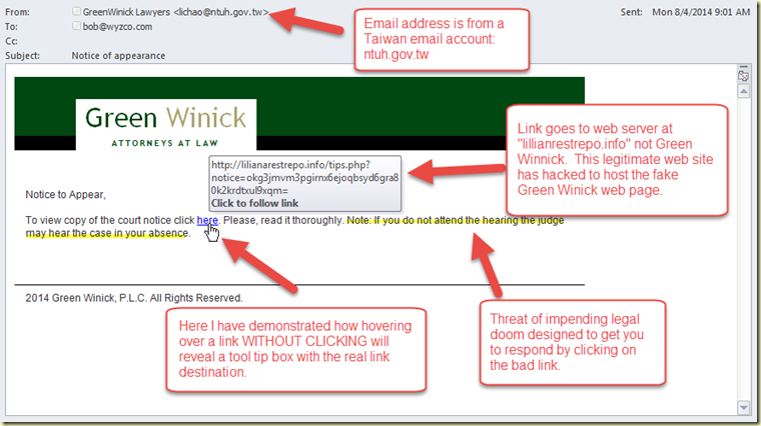
 DARPA (Defense Advanced Research Projects Agency) recently held a contest to explore the feasibility of automating the process of finding vulnerabilities on a group of target computers, and automatically fixing the vulnerabilities. Using a game format similar to “capture the flag,” on Aug. 5,at the Paris Las Vegas hotel, seven teams of programmers, hackers and researchers set a cybersecurity milestone.
DARPA (Defense Advanced Research Projects Agency) recently held a contest to explore the feasibility of automating the process of finding vulnerabilities on a group of target computers, and automatically fixing the vulnerabilities. Using a game format similar to “capture the flag,” on Aug. 5,at the Paris Las Vegas hotel, seven teams of programmers, hackers and researchers set a cybersecurity milestone. Here is a short list of applications that I use frequently when undertaking a penetration test of vulnerability scan. I don’t use all of these all the time, but they are probably the most popular tools in the security community. We start with Kali, the Swiss Army knife of exploitation tools. What can’t Kali do? Then we look several stand alone tools for host enumeration, port scanning, packet sniffing, vulnerability detection, ...
Here is a short list of applications that I use frequently when undertaking a penetration test of vulnerability scan. I don’t use all of these all the time, but they are probably the most popular tools in the security community. We start with Kali, the Swiss Army knife of exploitation tools. What can’t Kali do? Then we look several stand alone tools for host enumeration, port scanning, packet sniffing, vulnerability detection, ... Not sure how funny this is. According to
Not sure how funny this is. According to  Holy acronyms Batman! What the heck does this headline mean? Well, the National Institute for Standards and Technology (NIST) has removed two-factor authentication (TFA) via short-messaging service (SMS) from the approved list of two-factor authentication methods. The reason is that SMS is an unencrypted service, and the lack of encryption makes it too insecure for use in Federal authentication systems. NIST is recommending that all ...
Holy acronyms Batman! What the heck does this headline mean? Well, the National Institute for Standards and Technology (NIST) has removed two-factor authentication (TFA) via short-messaging service (SMS) from the approved list of two-factor authentication methods. The reason is that SMS is an unencrypted service, and the lack of encryption makes it too insecure for use in Federal authentication systems. NIST is recommending that all ... I am a firm believer in, and user of two-factor authentication (TFA or 2FA). Heck, if there was three-factor authentication I would probably sign up. The two most popular authenticator apps are Authy and Google Authenticator. I primarily use Google Authenticator wherever I can. I use SMS when Authenticator isn’t an option, or won’t work. I had trouble, for instance, getting Facebook to work ...
I am a firm believer in, and user of two-factor authentication (TFA or 2FA). Heck, if there was three-factor authentication I would probably sign up. The two most popular authenticator apps are Authy and Google Authenticator. I primarily use Google Authenticator wherever I can. I use SMS when Authenticator isn’t an option, or won’t work. I had trouble, for instance, getting Facebook to work ...