 Phishing Email Alerts
Phishing Email Alerts
Straight from my Inbox or from reliable sources on the Internet.
Today I am launching a new recurring topic that I am calling the Friday Phish Fry. Each Friday I will be posting examples of clever phish that made it past my spam filters and into my inbox. I will be highlighting the email and explaining how to know that this email is a fake. The purpose of these Friday posts are two-part: The first is to feature new phish as they are deployed by cyber-criminals and other bad actors, so my readers will be warned of new exploits. The second is to help my readers to learn how to detect and dissect a phish so they can tell it for a genuine email.
Friday Phish Fry joins Saturday’s Weekend Update and Sunday Funnies as posts on a recurring theme. Please join me on Friday to see what the bad guys have created this week.
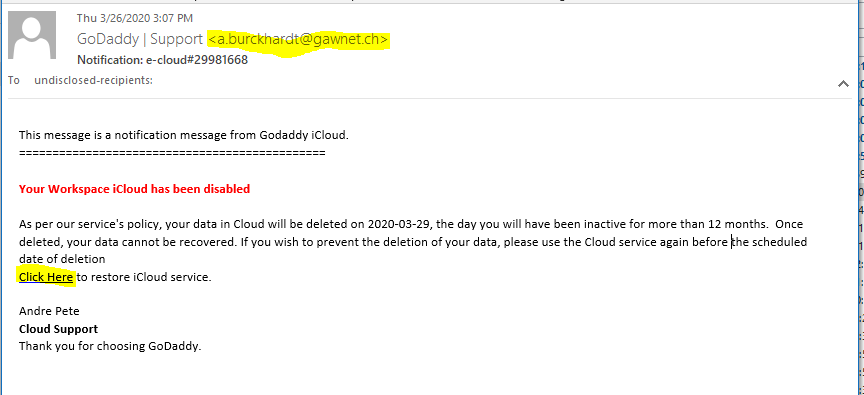
Our first candidate is am email from GoDaddy about your iCloud storage. The first clue that this email is a phish is that iCloud is an Apple product, not a GoDaddy offering. The email address of the sender is not using a GoDaddy email domain, but instead appears to be from gawnet.ch, a Swiss country code. GoDaddy | Support <a.burckhardt@gawnet.ch>. The Click here link goes to the web page at mac.atlantianmysteryschool.org, again, not a GoDaddy domain. The leading mac indicates this is a subdomain, which is suspicious. As of March 29, Virustotal is not flagging this web address as suspicious. When I clicked on the link, I got a “website coming soon” page, This is a GoDaddy Domain that was registered on 2016-06-18. So this is an old abandoned or forgotten domain that may have been hijacked. Here’s the email:
Watch out! Scummy scammers target home deliveries – from Sophos
Anxiously waiting for a home delivery? Don’t be tricked by a message that says there’s a problem with your address, Click through to see examples…
In the following email is allegedly from hosting company 1&1 IONOS, but the email domain of the sender is T-online.de, which is a German domain. All of the links in the first paragraph resolve to vps.fillrite.me. Virustotal found this link to be malicious.
[DON’T HIT THE PANIC BUTTON] “You Are Infected” – Bad Guys Launch an Evil New Corona Virus Attack – from KnowBe4
Malicious actors continue to craft ruthlessly aggressive, evil email attacks tailored to leverage mounting fears and anxieties surrounding the COVID-19 global pandemic among employees in the office and at home. In the latest Coronavirus-themed phishing email reported to KnowBe4 by customers using the Phish Alert Button (PAB), bad guys try to exploit the very worst fear among email recipients: the fear of infection.
Hitting the Panic Button
Late Friday night March 27, 2020, we spotted a new phishing email warning the recipients that they have been exposed to the Coronavirus through personal contact with a “colleague/friend/family member” and directing them to download a malicious attachment and proceed immediately to the hospital. This email is simple, succinct, and alarming. Moreover, it spoofs a hospital, lending additional credibility to this particular social engineering scheme, which is clearly designed to elicit a panicked response from readers and override any form of rational, measured thought. The attached Excel file is billed as a “pre-filled” form that victims should bring with them to the hospital. In fact, that form is a malicious, macro-laden Office document that is at the time of this report detected by only a handful of major anti-virus applications. This malware’s capabilities are incredibly sophisticated and dangerous.
FBI Warns of Stimulus Check Scams – from KnowBe4
The FBI’s Internet Crime Complaint Center (IC3) issued an alert warning of coronavirus-related phishing attacks, particularly surrounding economic stimulus checks. The news that the US government is likely to send upwards of $1,000 to most Americans has created a golden opportunity for scammers, especially since the delivery method for the cash is still uncertain.
“Look out for phishing emails asking you to verify your personal information in order to receive an economic stimulus check from the government,” the FBI says. “While talk of economic stimulus checks has been in the news cycle, government agencies are not sending unsolicited emails seeking your private information in order to send you money.”
https://otx.alienvault.com/pulse/5e8242f59b8b637793daf071/
How to stay on top of coronavirus scams – and all the others too – from Sophos
The bad news is that you have to watch out for a plethora of new coronavirus cyberscams, as well as all the old stuff, too…
I have redacted any client information from this email. There are a couple tips in this phish. First, the sending email address, while it loots like it MIGHT be legit, is not correct for the email server being used. The second it the link under the “Release message now” button goes to a suspicious address
Testing the link on VirusTotal produced an inconclusive result. Nevertheless, I am adding this to the Phish Fry.
———- Original Message ———-
From: “redacted.com Server Alert” <wallabees@prairieridgeconsulting.net> (This address is spoofed)
To: gus@redacted.com
Date: April 1, 2020 at 2:12 AM
Subject: gus@redacted.com have pending messages on redacted.com server
667% spike in email phishing attacks due to coronavirus fears
New data from Barracuda shows cybercriminals are taking advantage of people’s concerns during the COVID-19 pandemic.
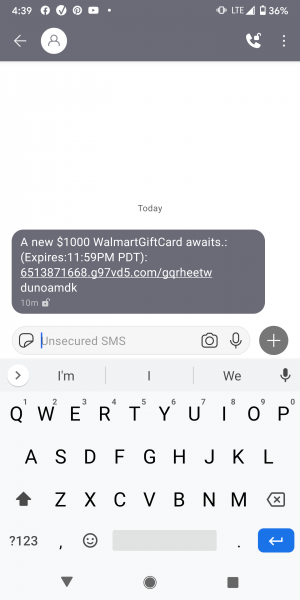
And lets not overlook fake SMS emails – called Smishing.
Share
APR







About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com