Phishing Email Alerts
Catch of the Day: PayPal Invoice Phish
Chef’s Special: Chase Phish
Examples of clever phish that made it past my spam filters and into my Inbox, or from clients, or reliable sources on the Internet.
I would be delighted to accept suspicious phishing examples from you. Please forward your email to phish@wyzguys.com.
My intention is to provide a warning, examples of current phishing scams, related articles, and education about how these scams and exploits work, and how to detect them in your own inbox. If the pictures are too small or extend off the page, double-clicking on them will open them up in a photo viewer app.
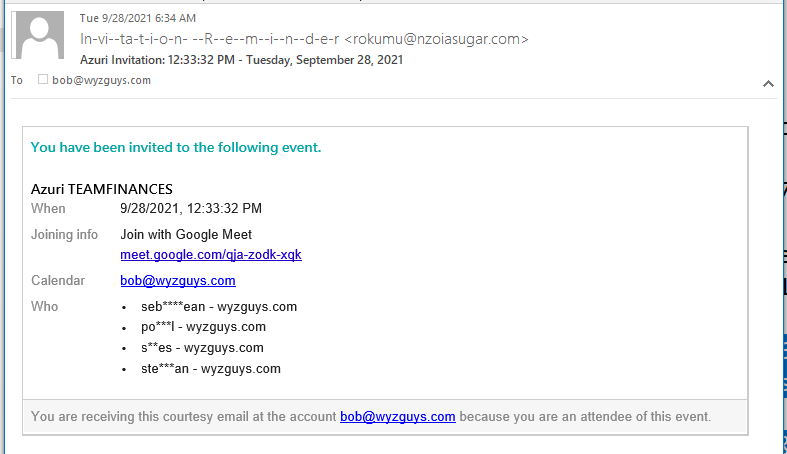
Invitation Phish
When you receive an invitation to a webinar, online Teams meeting, or Zoom event, please be certain that the invitation is legitimate. I received this email about a Google meeting of some kind.
the meet.google.com link really resolved to this URL: https://servedby.flashtalking.com/click/1/106233;3692435;2805280;211;0/?ft_width=1&ft_height=2&gdpr=${GDPR}&gdpr_consent=${GDPR_CONSENT_78}&us_privacy=${US_PRIVACY}&ft_section=26199274_309994132_502648299_154470308&ft_custom=309994132&url=https%3A%2F%2Fdelphisocial.com%2Fror%2Ff54caee25e7153dfa3704ba0071b61d1%2Fbob%40wyzguys.com
There is a lot of special encoding called “percent encoding” that is used to replaced special characters in URLS. Wikipedia explains “Percent-encoding, also known as URL encoding, is a method to encode arbitrary data in a Uniform Resource Identifier (URI) using only the limited US-ASCII characters legal within a URI. Although it is known as URL encoding, it is also used more generally within the main Uniform Resource Identifier (URI) set, which includes both Uniform Resource Locator (URL) and Uniform Resource Name (URN).” You can see an example in the link above, at the end, where my email address is shown as %2Fbob%40wyzguys.com. The @2f is a forward slash / and the %40 is the @ sign.
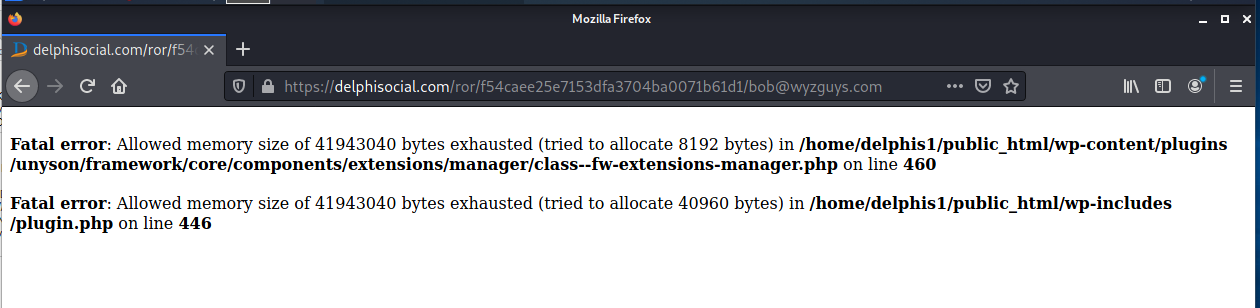
The landing page had problems, so I was not able to determine what the exploit was attempting, but it appears to be playing with WordPress configuration files.
Again, just make sure this is really a meeting before clicking through.
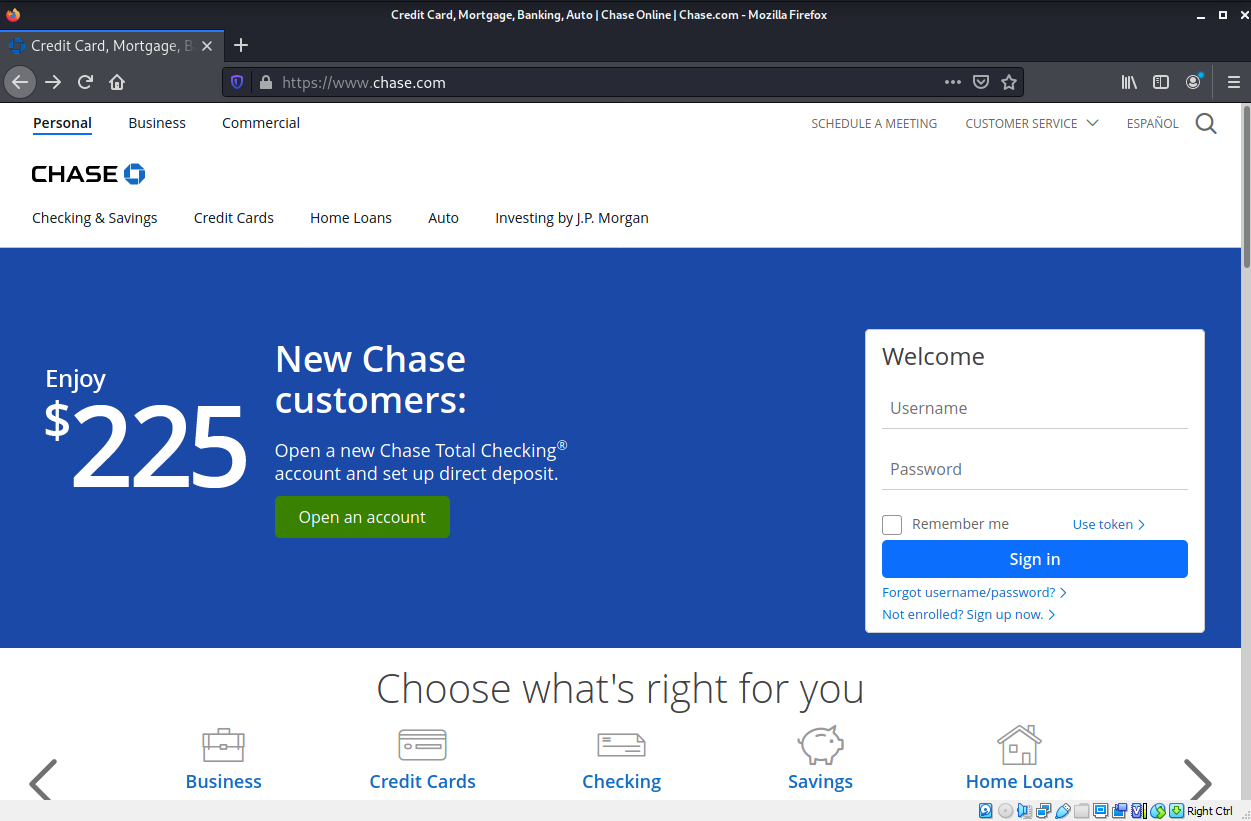
Chase Unusual Activity Phish
This one had me going, because the links resolved to an actual chase.com home page. The email is clearly fraudulent, the sender address is wrong for the domain, and it was sent to an email account I never use for setting up a web user account.
The Verify Identity button link resolved to https://s.id/GXUK5 which was redirected to https://secure01b.chase.com/web/auth/enrollment#/enroll/auth/signout;params=session which redirected to https://www.chase.com/. This is a legitimate home page. I think an intervening credential harvesting login was either missed in error by the attacker, or has been removed already. The way this was suppose to work is probably a lot like the Wells Fargo exploit I explored previously.
So this is the real deal, but I would still recommend against using this link to log in to any Chase account you might have.
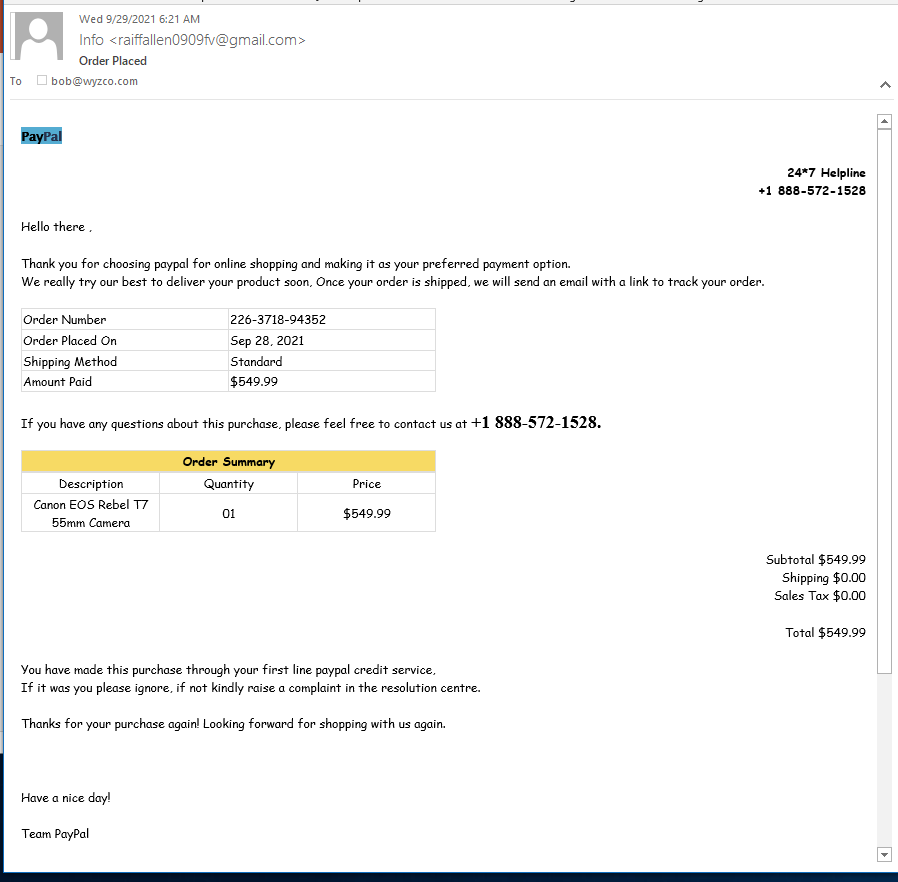
PayPal Invoice Phish
And here’s another scam directly the victim to call a toll-free support number. DO NOT make the call. If you must, open a case with PayPal directly from their web site.
Share
OCT






About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com