 Phishing Email Alerts
Phishing Email Alerts
Catch of the Day: Wells Fargo Identity Theft Phish – A trifecta – bank account, personal information, and a credit card. On the Dark Web this is called a Fullz.
Chef’s Special: Phishing attacks impersonate QuickBooks invoices ahead of July 15 tax deadline
Examples of clever phish that made it past my spam filters and into my Inbox, or from clients, or reliable sources on the Internet.
I would be delighted to accept suspicious phishing examples from you. Please forward your email to phish@wyzguys.com.
My intention is to provide a warning, examples of current phishing scams, related articles, and education about how these scams and exploits work, and how to detect them in your own inbox.
Wells Fargo Identity Theft Phish
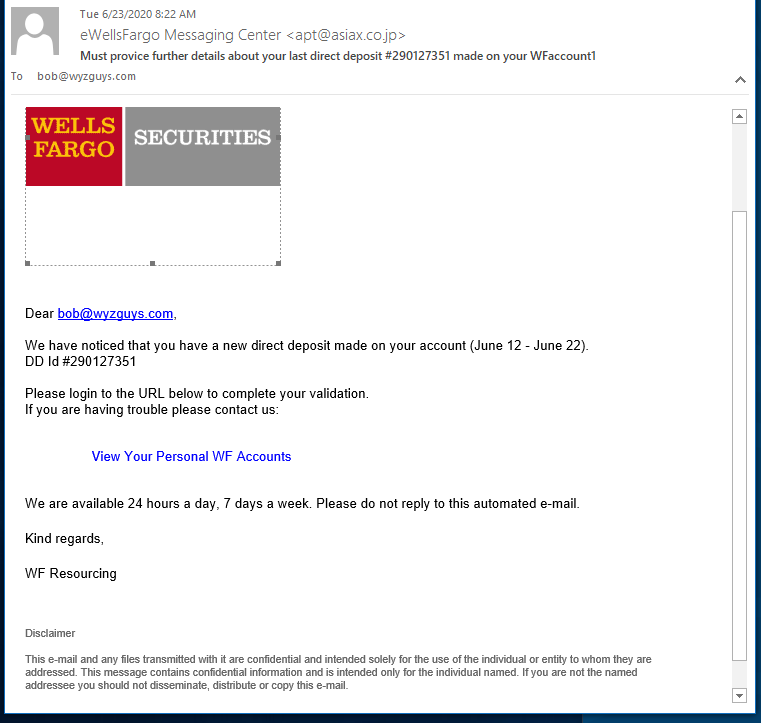
You don’t see one like this every day. This fabulously engineered phishing exploit starts out with good news, someone made a direct deposit in your account. Who doesn’t like free money? Click, and you’ve been pwned.
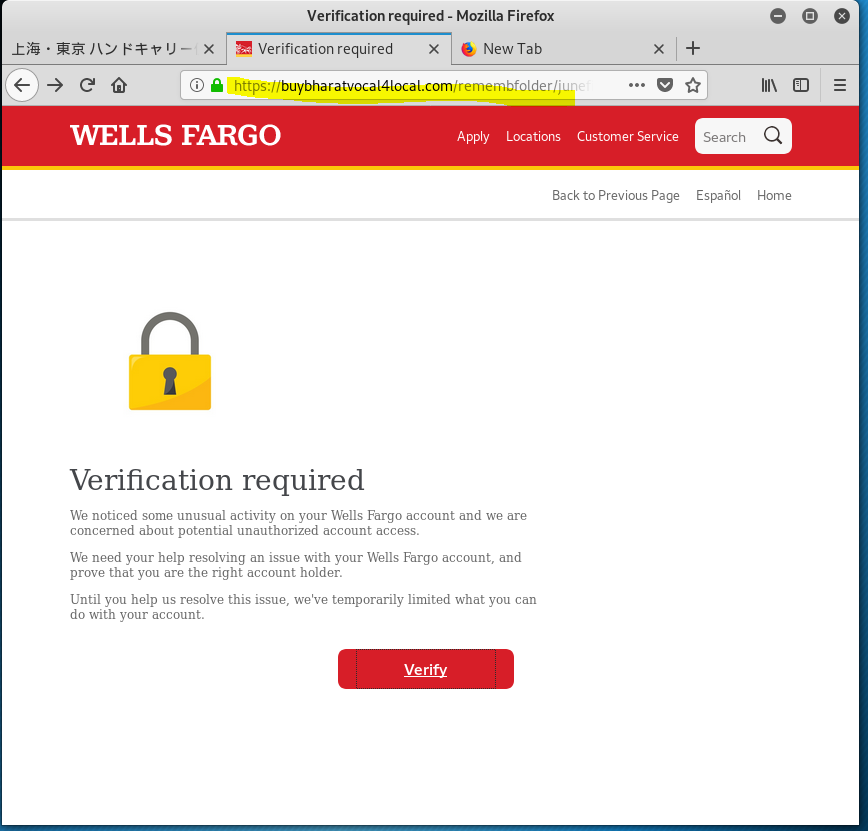
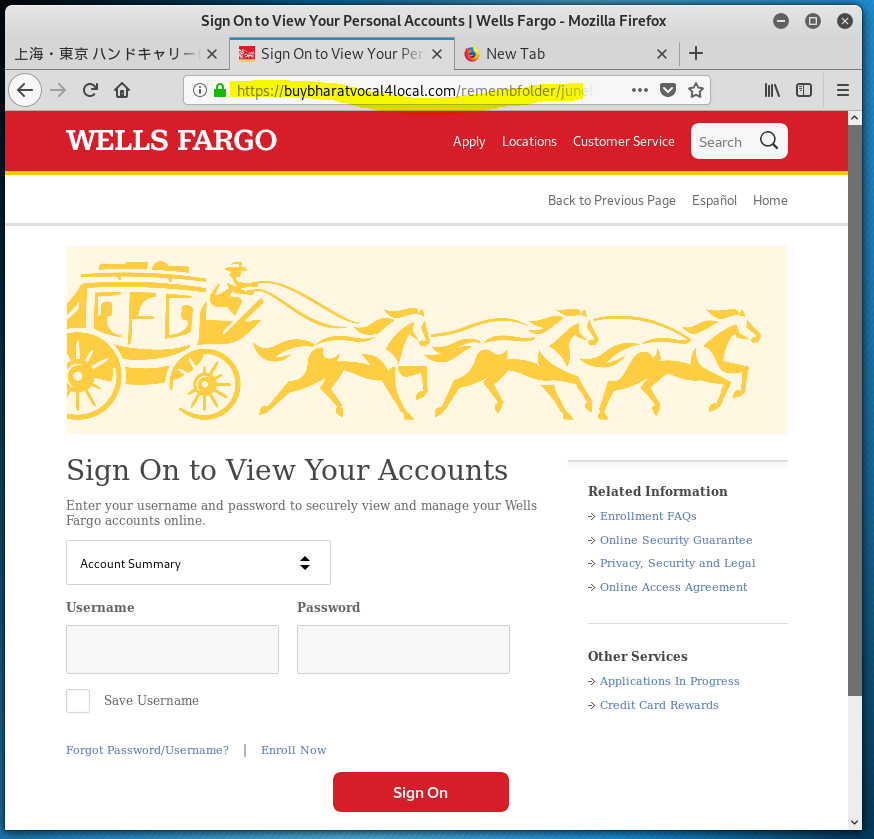
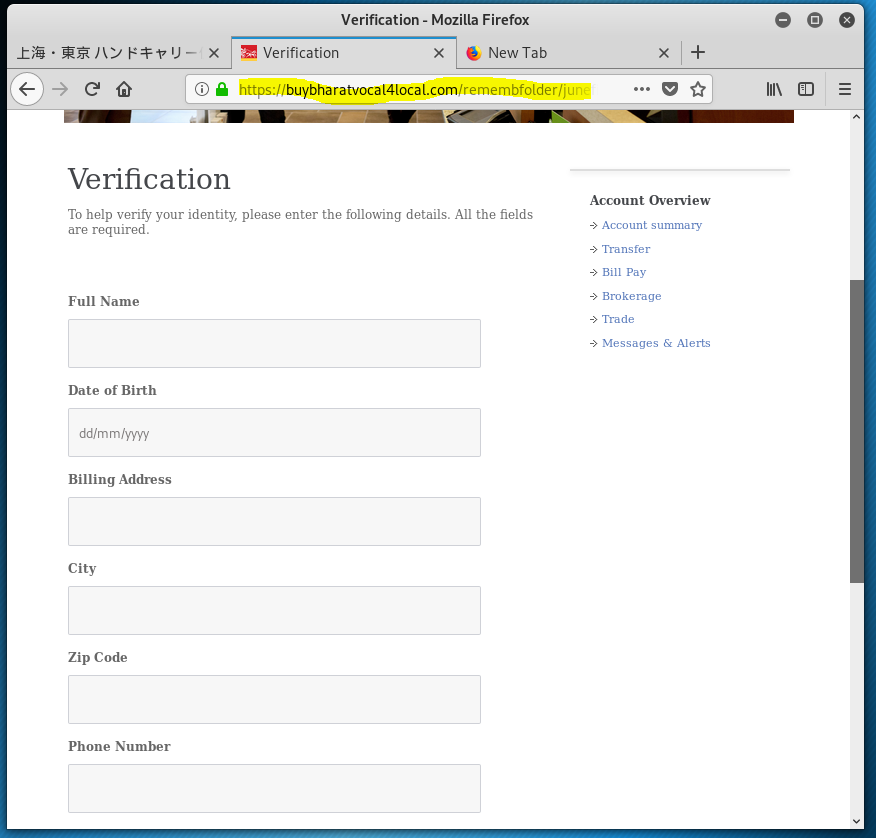
Not only does this phish want your Well Fargo Banking and Financial account credentials, but as I clicked through the multiple landing pages, this phishing exploit asked for personal information including street address, phone number, birth date, SSN, and driver’s license. On the next page they asked for credit card information. The fifth and final screen was an actual Wells Fargo login screen. If you followed all the way through, you coughed up every bit if information the attacker would need to log on to your Wells Fargo account and clean it out.
The email domain was hijacked from a Japanese air freight company. (WellsFargo Messaging Center <apt@asiax.co.jp>) The View Your Personal WF Accounts resolved to http://sagoodesign.com/firstgroupus. VirusTotal identified this as a phishing address. From there I was redirected to the first landing page at https://buybharatvocal4local.com/remembfolder/junefileswf/intro.html. From there I kept clicking, going deeper into this highly sophisticated identity theft and bank account hijacking exploit. The quality of the landing pages was very high, as you will see.
The website that is hosting these landing pages was hijacked. The last image in this case is the home page for https://buybharatvocal4local.com Buy Bharat V4L
The second landing page – user ID and password collected
The third landing page – Name address, phone, birth date, SSN, and driver’s licence information collected.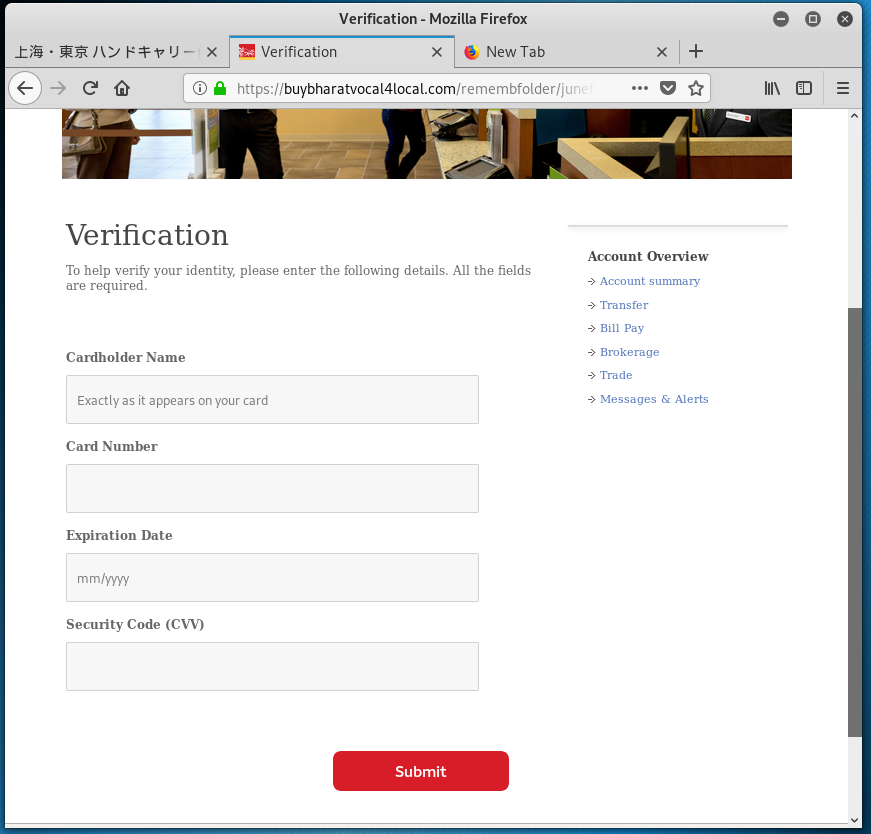
The fourth landing page – Got the credit card
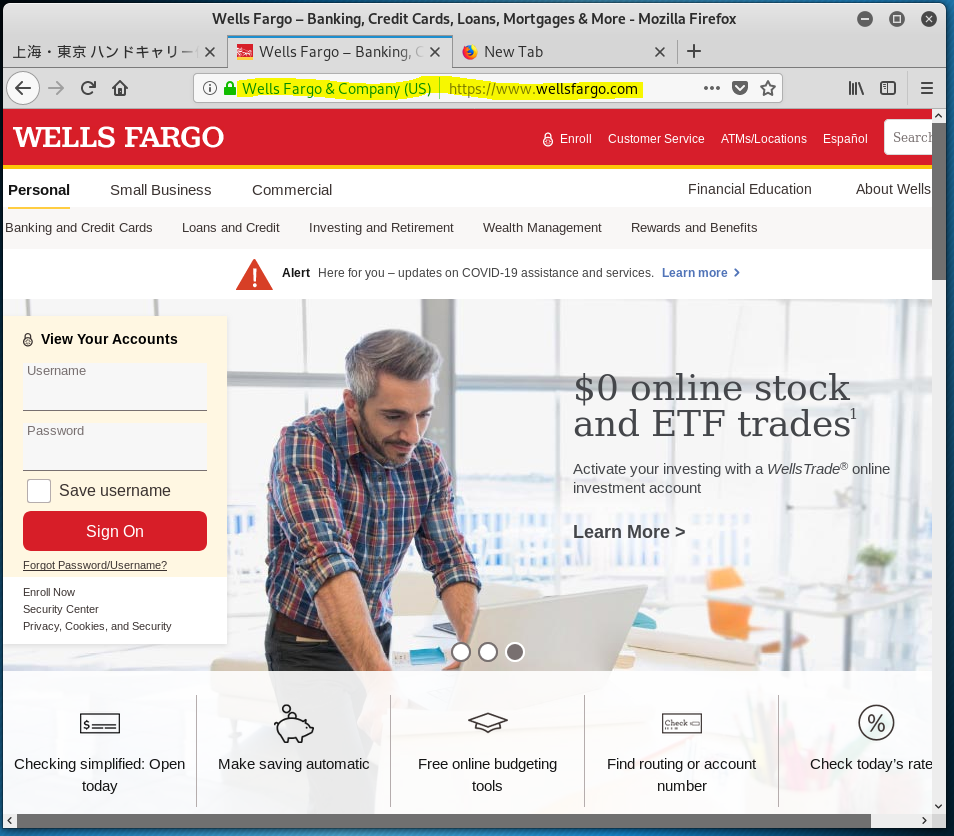
The best for last – I was sent to a LEGITIMATE Wells Fargo login page.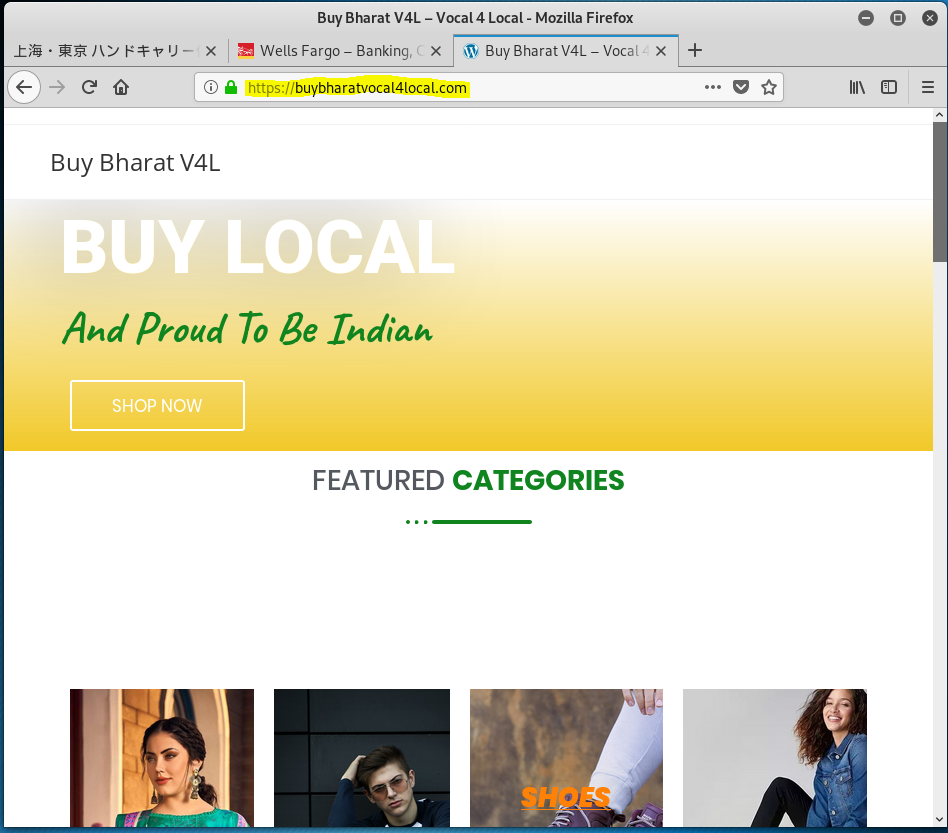
The victim website that is hosting the fake landing pagesThe is an excellent piece of social engineering. The perpetrator got the bank account, personal info, and a credit card – a trifecta!
What about foreign language phish?
I received a phish that was written in Chinese. The email domain is chunqiu-group.com. ICAAN WHOIS shows that this domain has been registered in 2016 and the registration goes through 2028, so this is not a recently registered domain to be used for a quick phishing campaign. More likely the sender’s email was spoofed or hijacked. There was not website I could find on this domain.
The mail header showed the email had started it journet in China from this mail server: Received: from fqggwvv (42.235.172.200) by mail4.chunqiu-group.com. It is looking more like this is a case of email account hijacking, since the email started life on the sender domain’s email server..
The Subject line 请尽快升级邮箱恢复正常使用 translates to Normal Usage. Out of curiosity, I translated the rest of the email and it appears to be a typical “take some action or we will disable your service” phish.
I clicked in the bottom blue bar: 点击完成升级 Completed box. The click-through resolved to http://dfrmk.smevmail<dot>com/?email=support@wyzmail.com. The landing page displayed an error message: 您当前浏览器不支持或操作系统语言设置非中文,无法访问本站!This is a non-Chinese, non-Chinese sentence system! Long story short, if you get an email in a language you can’t read, there is a good chance it is a phish, spam, or at least very seriously lost.
This email may also be a legitimate response email created when an automated sign-up bot signed my email address up for an unwanted service, as part of an email bomb campaign.
Just delete emails like this, unless they are arriving in a torrential volume, in which case you are being spam bombed by a bot. Read this article: How to Survive an Email Bomb Attack
Contact Form Spam and Phish
If you run a website, as I do, then you are familiar with a variety of spam that is generated by the contact form on your website. Spammers and phishers know that a message generated by the contact form on your website will go straight into your inbox, because the source domain is your own, and trusted by your mail system.
Many of the form spam I receive invites me to subscribe to a service that will send automated form spam on my behalf. As if I would ever participate in this charade. The best way to prevent this from happening is to add a CAPTCHA to the form on your web site. This should prevent automated bots from successfully sending email from the form. This will also prevent your site from being used in a Form Spam Email Bomb (see above).
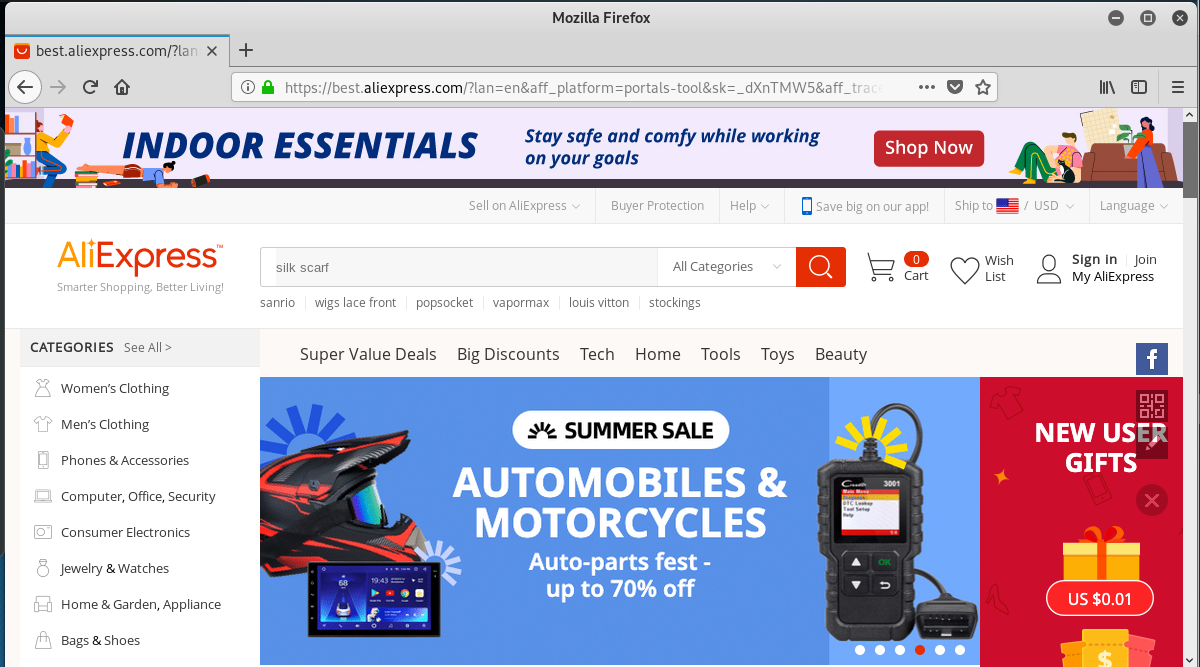
This contact form email appears to be from an unhappy customer. Since we do no shipping here, it is easy for me to recognize this as a scam. The link https://imgurgallery.com/dc34rf was actually bounced to https://best.aliexpress.com/?lan=en&aff_platform=portals-tool&sk=_dXnTMW5&aff_trace_key=516c9c6618e74c0fbbd9f2e97cb9f063-1592748212329-01508-_dXnTMW5&terminal_id=85873192c1c34c7fba199c865e22346d&aff_request_id=516c9c6618e74c0fbbd9f2e97cb9f063-1592748212329-01508-_dXnTMW5. This appears to be a straight up click-fraud exploit, where the sender is rewarded for sending traffic to Ali Express. The long encoding is likely an affiliate marketing ID.
Short of the CAPTCHA fix, there is nothing to be done but delete these emails. If you try to block them with your spam filter, you will block everything coming to your own email account.
The email:
The Ali Express landing page:
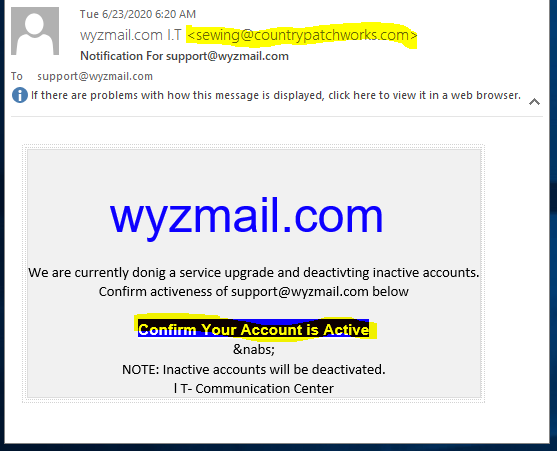
Confirm Your Account – Give Away Your Password
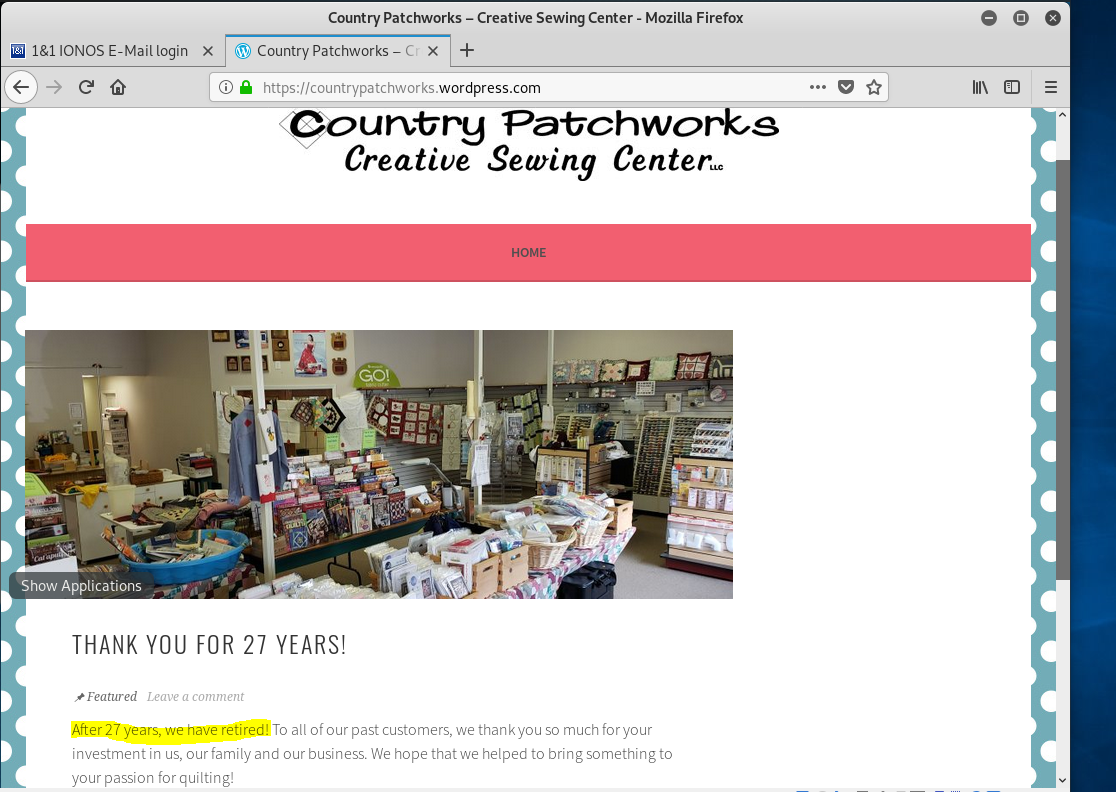
Here is yet another credential-stealing phish on an IONOS theme. The sender’s email domain countrypatchworks<dot>com belongs to an quilting business that is out of business. “After 27 years we have retired.” The site is on WordPress.com. A good reminder is that the old junk, websites, and media accounts you abandon on the web get a second life as part of a phishing scam. (see home page below).
The Phish
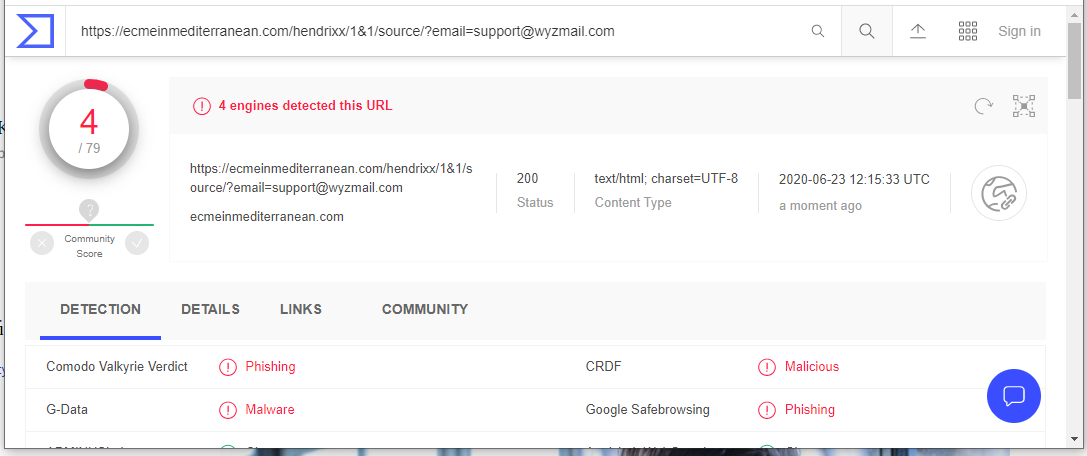
The link bar, Confirm Your Account is Active resolves to https://ecmeinmediterranean.com/hendrixx/1&1/source/?email=support@wyzmail.com.
VirusTotal found this to be a phishing site.
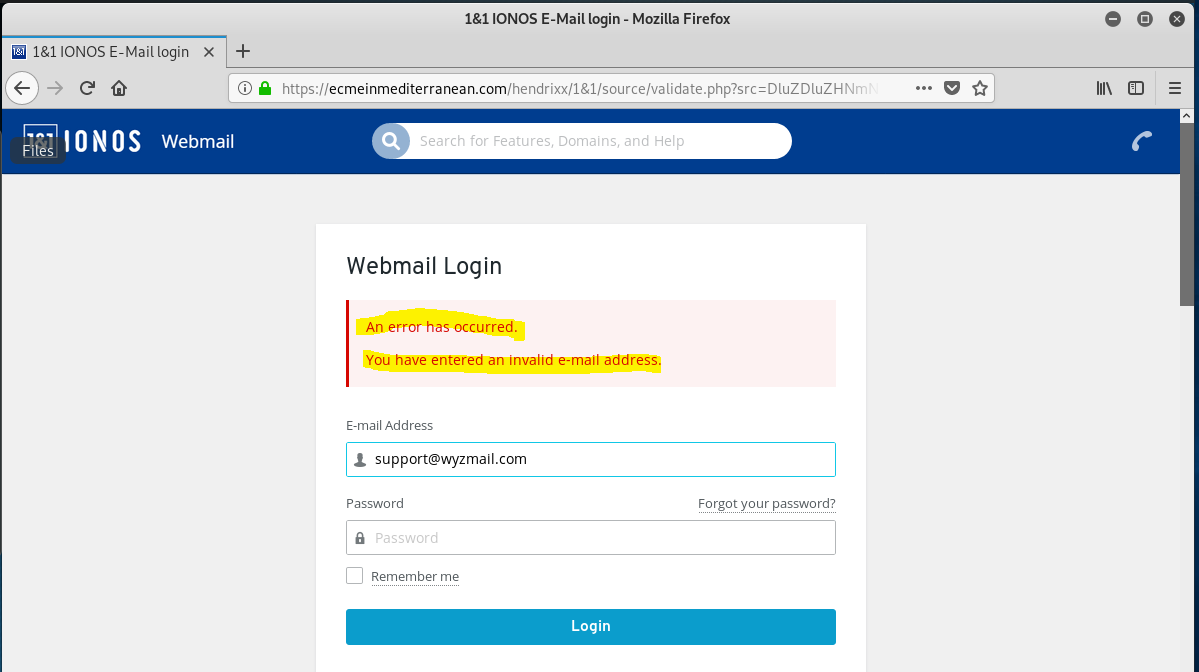
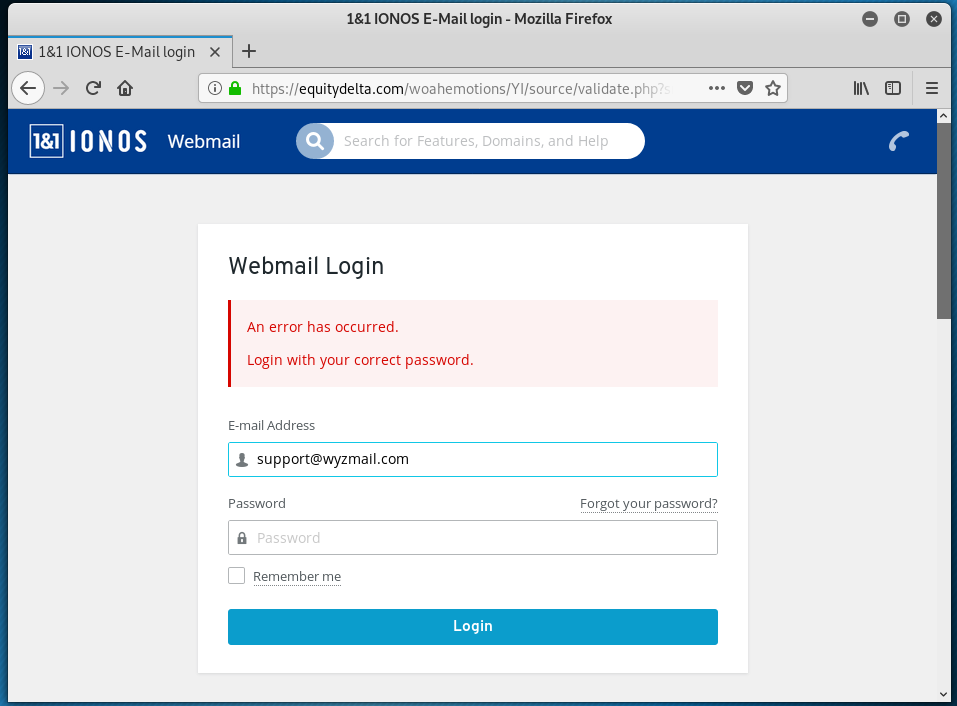
And here is the landing page after entering my “password”. Notice the error message.
Nearly all emails asking for you to confirm your account, or threatening to closes your account due to “inactivity” as phishing scams like this one. To confirm, DO NOT click on the link but go directly to the website using your own browser bookmark, or by typing the URL into the address bar, the old school way.
Try, Try Again…
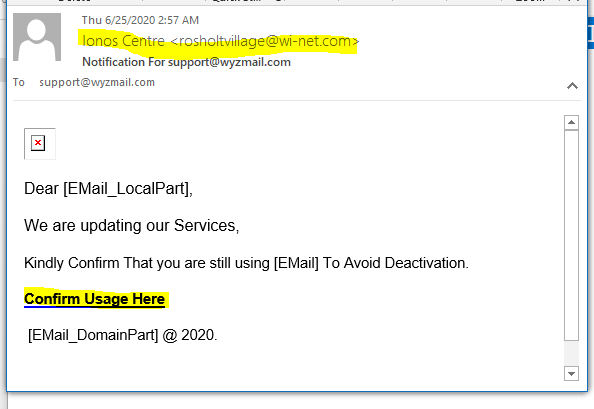
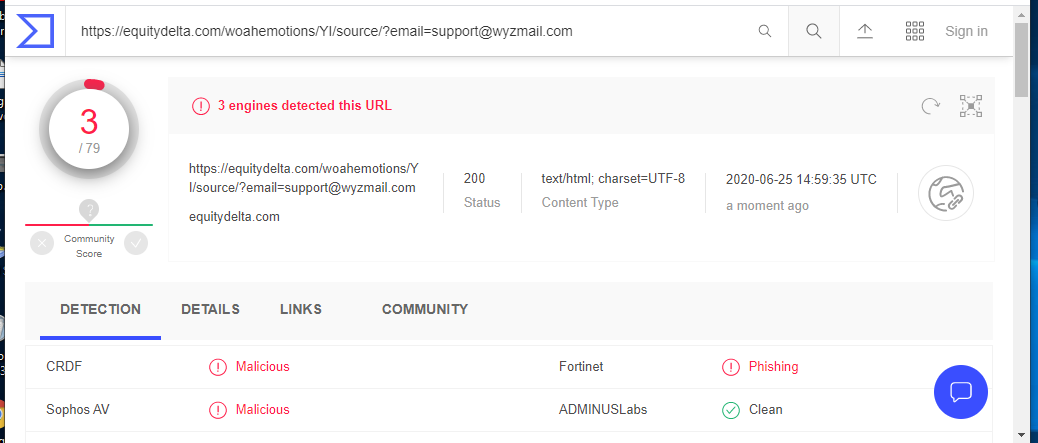
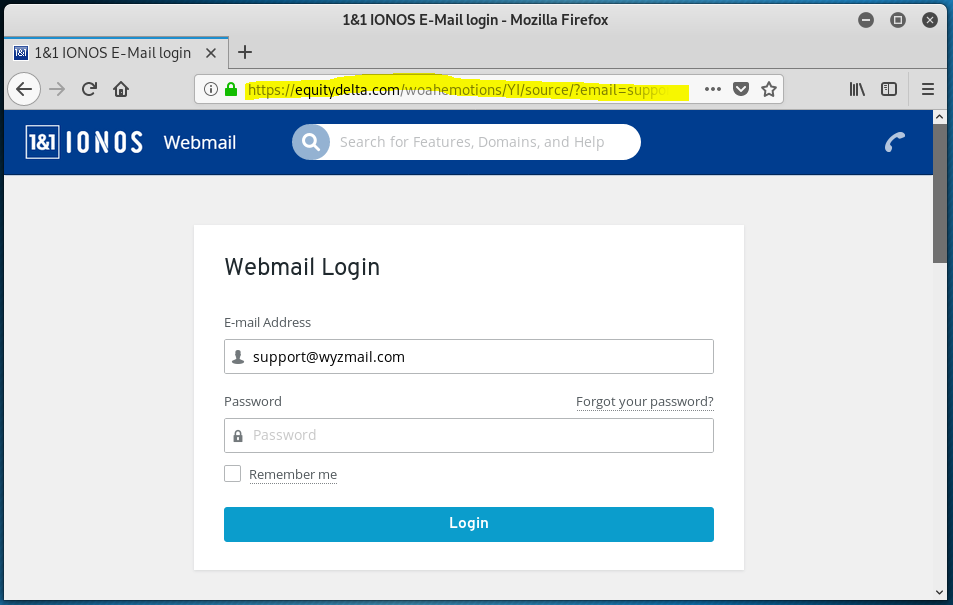
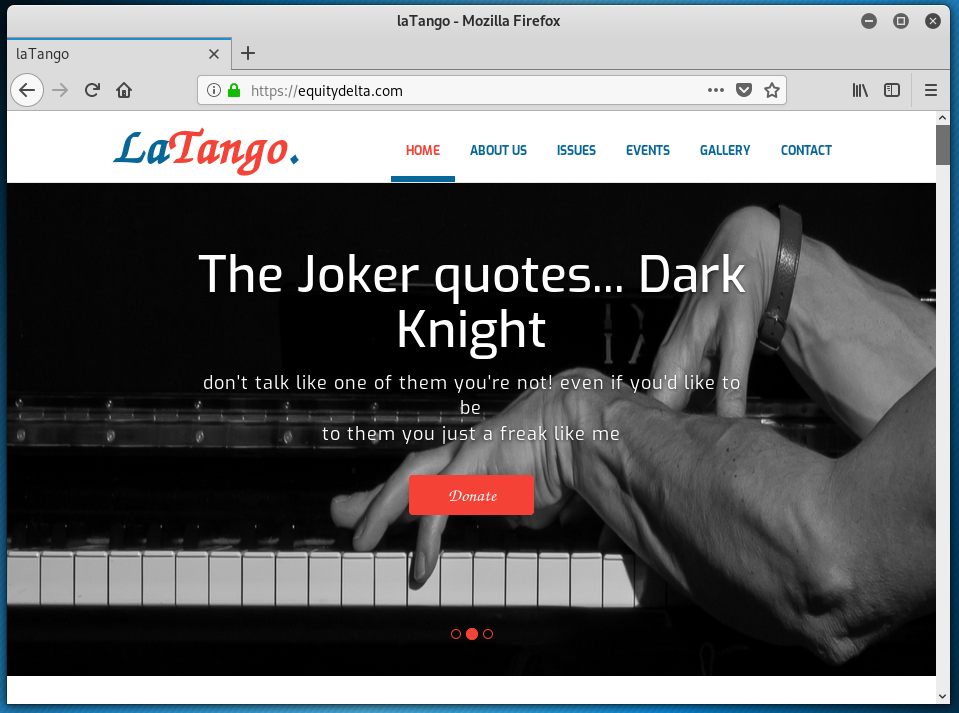
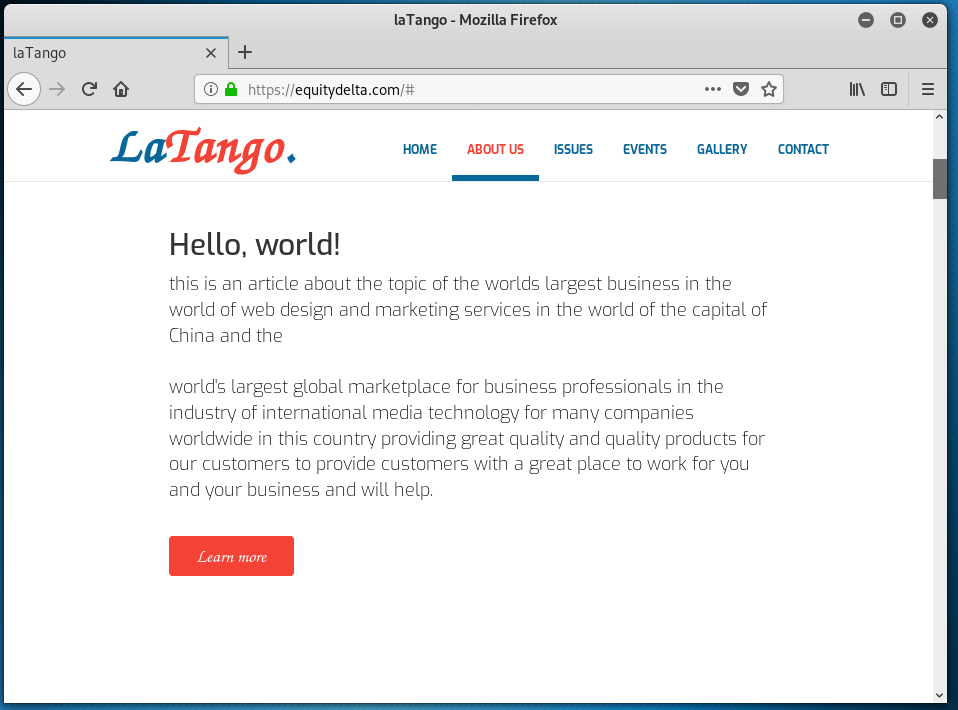
This may be the last IONOS branded phish I will post for a while, because they all are variations on a theme. The sending email domain is clearly wrong. The Confirm Usage Here link resolves to https://equitydelta<dot>com/woahemotions/YI/source/?email=support@wyzmail.com. The landing page is a basic email credential stealing login form. Virustotal shows this to be a known phishing site. The actual site homepage appears to be for a web site that is for a music or entertainment business, and still under development.
All I can say is treat any emails that appear to come from your email service provider with suspicion. Log into your email account using your bookmark or shortcut, or type their web address into the address bar directly. DO NOT CLICK ON THE PROVIDED LINK!!
From Sophos Naked Security:
Anatomy of a survey scam – how innocent questions can rip you off
We take part in a fraudulent survey so you don’t have to. Show your friends and family how these scams unfold. Click through the link to see images of the entire survey scam.
Phishing attacks impersonate QuickBooks invoices ahead of July 15 tax deadline
Targeting the CEO and others in an organization, the attacks spotted by cybersecurity firm Darktrace were detected due to artificial intelligence.
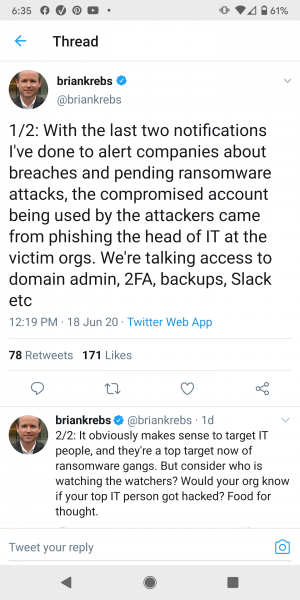
Brian Krebs tweets about spearphishing campaigns targeting IT and cybersec professionals
I have written about this issue previously. Attacks against IT departments and IT service companies are intensifying because IT staff and MSPs have all the passwords to all the accounts and customers.
Share
JUN









About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com