Phishing Email Alerts
Catch of the Day: OneDrive DocuSign Phish
Chef’s Special: IONOS Fake Invoice Phish
Examples of clever phish that made it past my spam filters and into my Inbox, or from clients, or reliable sources on the Internet.
I would be delighted to accept suspicious phishing examples from you. Please forward your email to phish@wyzguys.com.
My intention is to provide a warning, examples of current phishing scams, related articles, and education about how these scams and exploits work, and how to detect them in your own inbox. If the pictures are too small or extend off the page, double-clicking on them will open them up in a photo viewer app.
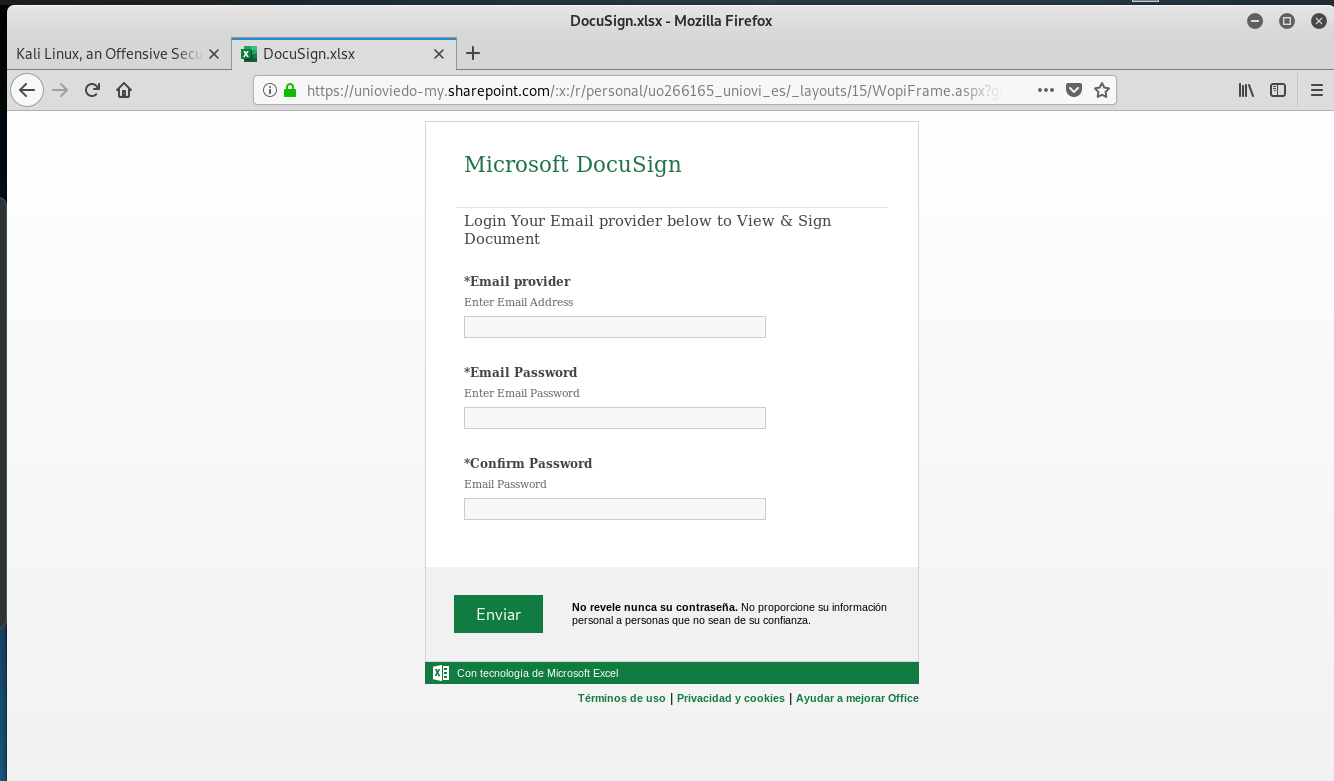
OneDrive Docusign Phish
This reasonably convincing exploit ends up as an email account credential stealing form. The links resolves to https://unioviedo-my.sharepoint.com/personal/uo266165_uniovi_es/_layouts/15/guestaccess.aspx?guestaccesstoken=<redacted>.
This exploit uses a real SharePoint page to improve credibility. Many phishing exploits will blend replica sites with genuine sites to trick you into giving away personal information.
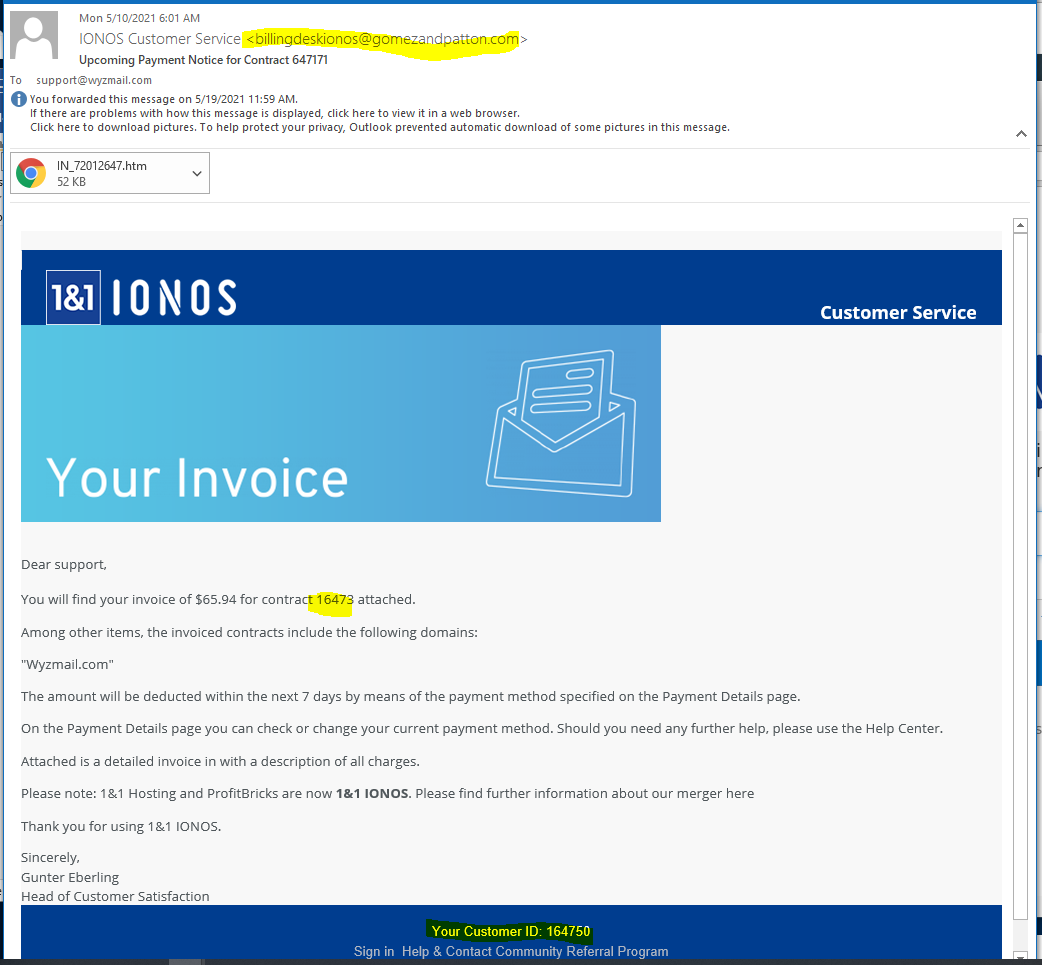
IONOS Fake Invoice Phish
This email looked so much like the real deal that I almost fell for it. The sender’s email address was an obvious clue, and the attachment should have been a PDF file not an HTM file. The contract numbers were wrong, too.
What I got when I opened the HTM file was a locally hosted web page that invited me to log in and send my credentials to the bad guys.
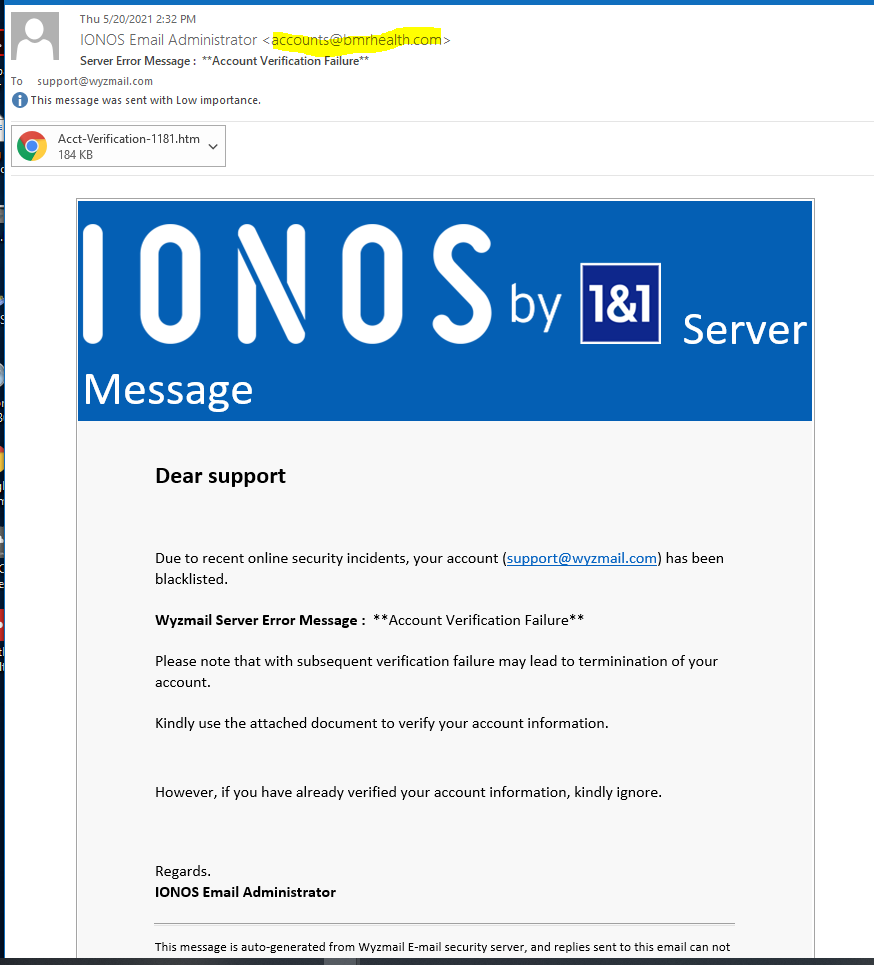
And Yet Another IONOS Phish
Seems like these exploits run in streaks, like a bunch of wanna-be phsihers just graduated from phishing school, and are trying the same exploit. This is another HMTL attachment containing a credential stealing web page,
Phishing Scammers Can Now Remove the ‘External Sender’ Email Warnings
With little more than some CSS and HTML coding, a security researcher demonstrates how easy it is to eliminate security warnings placed on email messages by security products.
Many organizations love the security feature where external emails are clearly marked, informing users so that anyone attempting to impersonate an internal user would raise suspicion. Hopefully, this will stop a phishing attack in its tracks.
But a clever security researcher, Louis Dion-Marcil, posted the results of his testing where he used some CSS code to simply hide the HTML-based warnings placed by a security software solution.
Noted in the Tweet’s comments was the fact that the HTML can just as easily be modified to indicate the email has been scanned and is legitimate.
This is very worrisome. Anytime users are asked to simply rely on technology to determine whether something is safe or is worthy of suspicion, the user tends to become complacent and blindly assumes that anything received is genuine.
However, impersonation is at an all-time high and tactics are improving each day to trick users into believing the sender is exactly who they claim they are. It’s critical that users be taught using security awareness training to remain vigilant, and not blindly trust security solution results. Remember, the bad guys work to evade detection by those very same products!
Blog post with link:
https://blog.knowbe4.com/phishing-scammers-remove-external-sender-email-warnings-impersonating-internal-users
New QuickBooks-Themed Phishing Attack Seeks to Infect Victims With Dridex Malware
I reported on this QuickBooks exploit last week if you want to see an example.
Purporting to be invoices and payment reminders, this new campaign targets users of the popular accounting software to install the banking trojan on its victims endpoints.
The bad guys have long known that emails involving the concept that the recipient owes money will get a response. They also know if you use a product or service that many people have already, you’ll equally get a response. Put them together and you have phishing magic.
That’s what security researchers at Bitdefender are seeing with this latest campaign of attacks on users of QuickBooks. Emails informing recipients of sizable amounts of money due is all it takes to get the click from the user:
The goal is to infect the victim endpoint with Dridex – a banking Trojan designed to steal banking credentials and other confidential information that can be used to access bank accounts and make fraudulent transactions. Dridex is commonly delivered via phishing emails that use malicious Microsoft Word and Excel documents as attachments.
The bad news is that the wide spread of smaller companies using QuickBooks makes this phish theming cast a pretty large net. Even if the recipient isn’t in Accounting or Finance, they may still wonder why does QuickBooks think the victim organization owes them a material amount of money.
This attack is pretty brilliant. So, you need to educate your users to avoid this and other scams like it. Remember, with Dridex the end result could be a completely wiped-out bank account, so taking the time to educate users will result in a very fast ROI.
Blog Post with links:
https://blog.knowbe4.com/new-quickbooks-themed-phishing-attack-seeks-to-infect-victims-with-dridex-malware
MAY







About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com