Phishing Email Alerts
Catch of the Day: 419 Homeland Security Scam
Chef’s Special: IONOS Credential Phish
Examples of clever phish that made it past my spam filters and into my Inbox, or from clients, or reliable sources on the Internet.
I would be delighted to accept suspicious phishing examples from you. Please forward your email to phish@wyzguys.com.
My intention is to provide a warning, examples of current phishing scams, related articles, and education about how these scams and exploits work, and how to detect them in your own inbox. If the pictures are too small or extend off the page, double-clicking on them will open them up in a photo viewer app.
IONOS Phish
Here is an email from “Costumer Care.” Evidently this is a Halloween themed phishing email? No, just a spelling confusion between customer and costumer. The link in this email resolves to https://cartago.casacastillo.cl/-/?8723051301?bob@wyzguys.com. This was identified on VirusTotal as a phishing link by Google Safe Browsing.
This leads to a typical credentials stealing landing page.
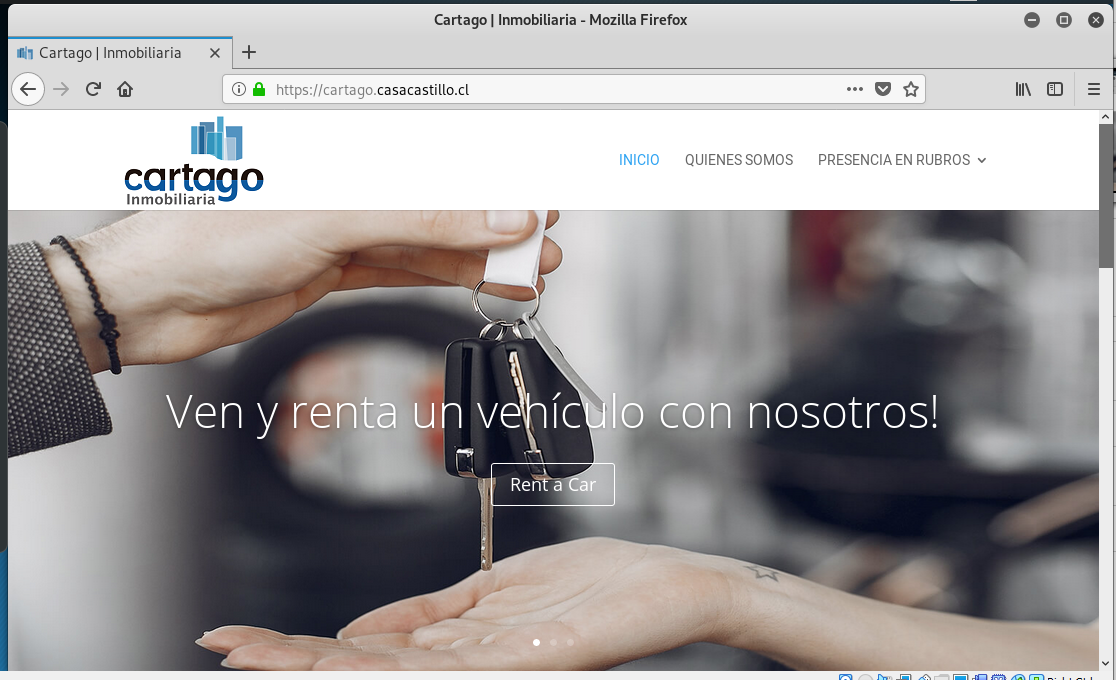
And the home page of the hijacked website used to host the landing page.
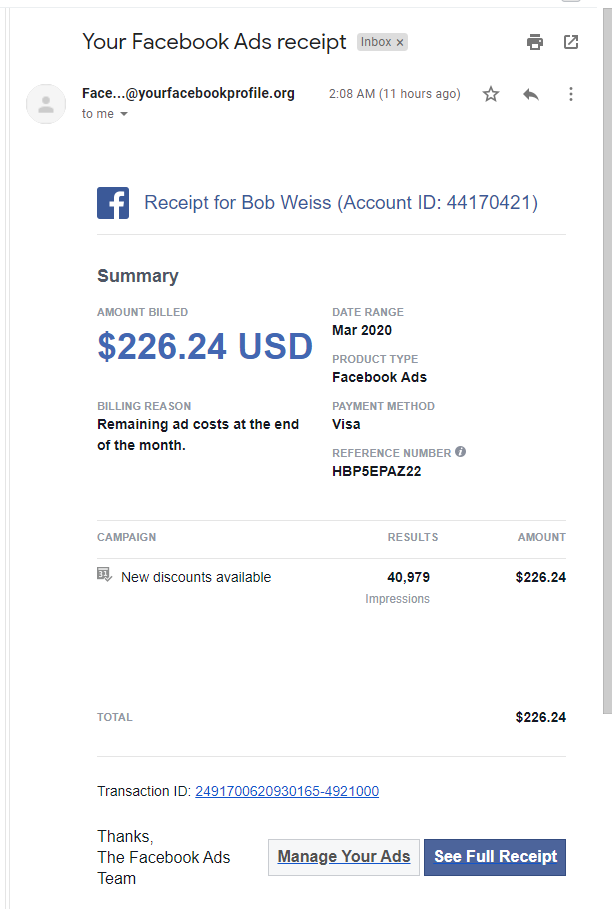
419 Homeland Security Scam Email
I don’t see as many of these “Nigerian Prince” advance fee frauds as I once did. But here’s a doozy submitted by a client. In this case he is masquerading as a Department of Homeland Security official. I can’t believe the length of this yarn, 1315 words. It goes on forever. I have posted the full text a Word doc titled 2020-10-28-419-letter
Simulated Phish from Infosec
Since starting at Infosec Institute, I have been introduced to some of the company’s products that support employee cybersecurity awareness training. On of those products is a simulated phishing platform to test the phishing detection and avoidance capabilities of your staff. Here’s a recent example from my own inbox. Can you tell what clues there are that this is fake?
Top 10 Brands Used in Phishing Email Attacks
If you have an email inbox, you’ve seen them. Emails claiming to come from a brand you know, but in reality, they are a “spoof” or copycat of an email from that company. These brand phishing attacks often involve sending you a branded email or text message with a URL link similar to the real thing. And now we know which brand names are used (and abused) to target individuals most often… Read more
Share
OCT








About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com