 Phishing Email Alerts
Phishing Email Alerts
Catch of the Day: Why We Don’t Do Product Endorsements
Chef’s Special: Spoofing SharePoint Phish
Examples of clever phish that made it past my spam filters and into my Inbox, or from clients, or reliable sources on the Internet.
I would be delighted to accept suspicious phishing examples from you. Please forward your email to phish@wyzguys.com.
My intention is to provide a warning, examples of current phishing scams, related articles, and education about how these scams and exploits work, and how to detect them in your own inbox. If the pictures are too small or extend off the page, double-clicking on them will open them up in a photo viewer app.
Why We Don’t Do Product Endorsements
I generally do not write product endorsements or reviews in this blog unless I have used the product myself for a long time. Product endorsements and reviews would be one way I could “monetize” this blog, and develop a perpetual income stream (aka “internet riches”) but I have so far avoided that. Any recommendations in this blog are only incidental, and part of the story.
I do accept articles from guest authors, though, and I understand that the link back to their website helps with traffic and Google ranking, and I am ok with that, at least for now.
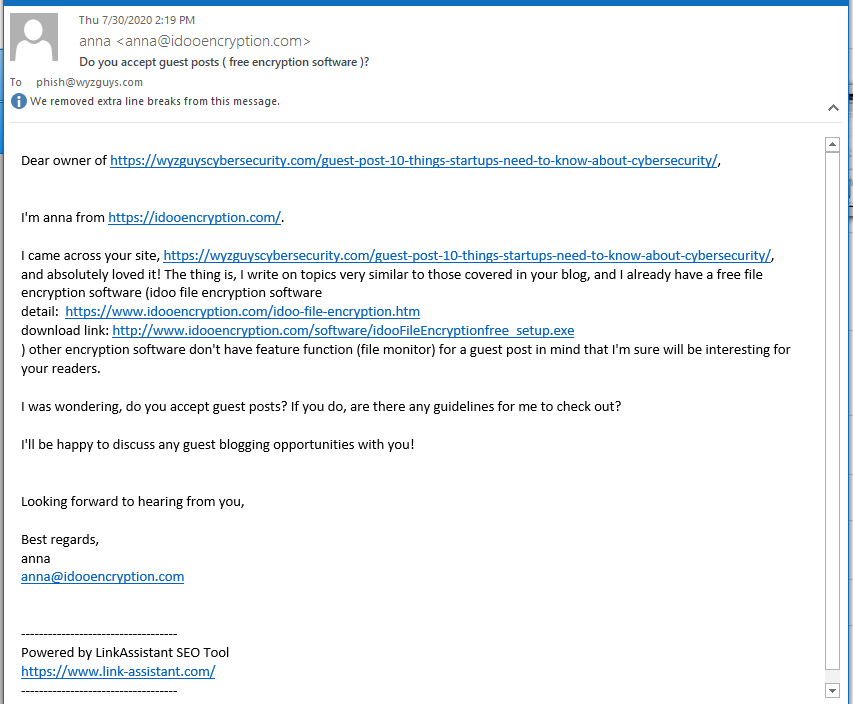
I got an inquiry about a guest post that was clearly going to involve a product endorsement from a source I have not worked with previously, for some sort of encryption software. So I responded to her email, and explained the rules, such as they are. Her inquiry and my response are below.
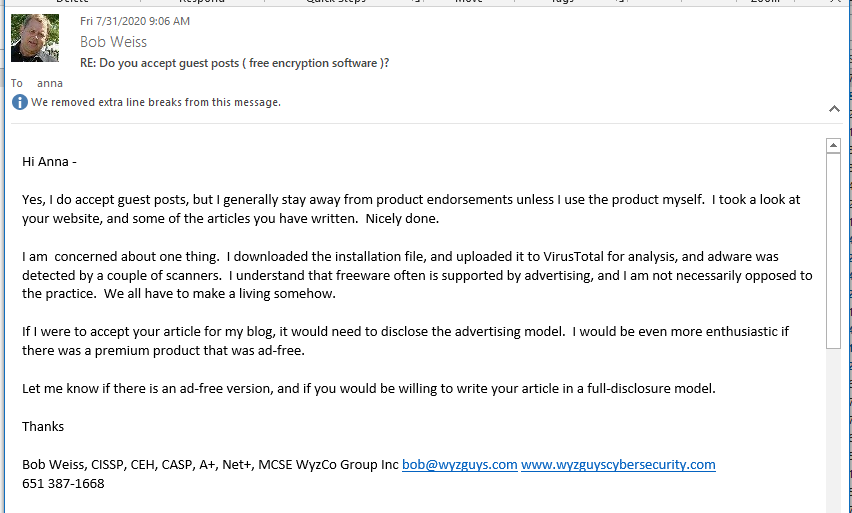
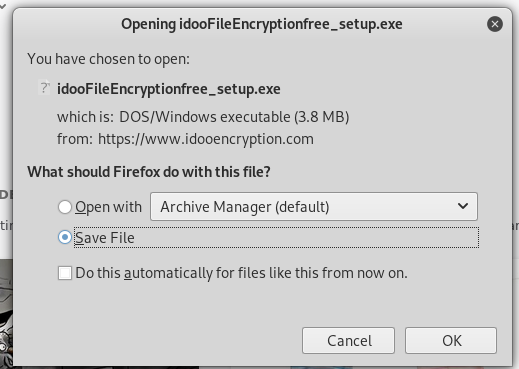
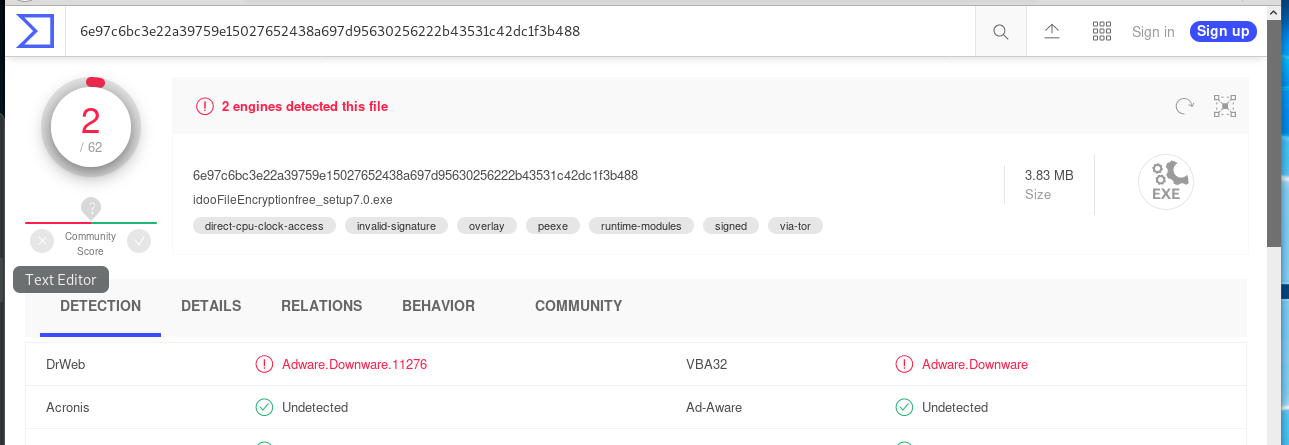
I downloaded the product and submitted the executable installation code to VirusTotal for analysis. The application was flagged for adware, which is unfortunate, but not surprising. Many freeware applications use an advertising model to support operations and pay the author for his or her time. Often there is a paid premium version that removes or disables the advertising feature.
I explained to Anna that I would accept the article only if the advertising feature were revealed in her article. I have not heard back from her yet, and perhaps I won’t. But having advertisers tracking your encryption application is a bad idea.
The process of analyzing the application code was interesting and worthy of this space. Just for the record, anyone submitting an article to me goes through a fairly rigorous background check, and all links are examined and verified. This is to protect the website, my visitors, and my reputation from any malicious activity.
The next time you are thinking about trying a freeware or paid application from an organization that you are not familiar with, download the installation file and upload it to VirusTotal before you install it. You might find some hitchhikers like I did.
Spoofing SharePoint Phish
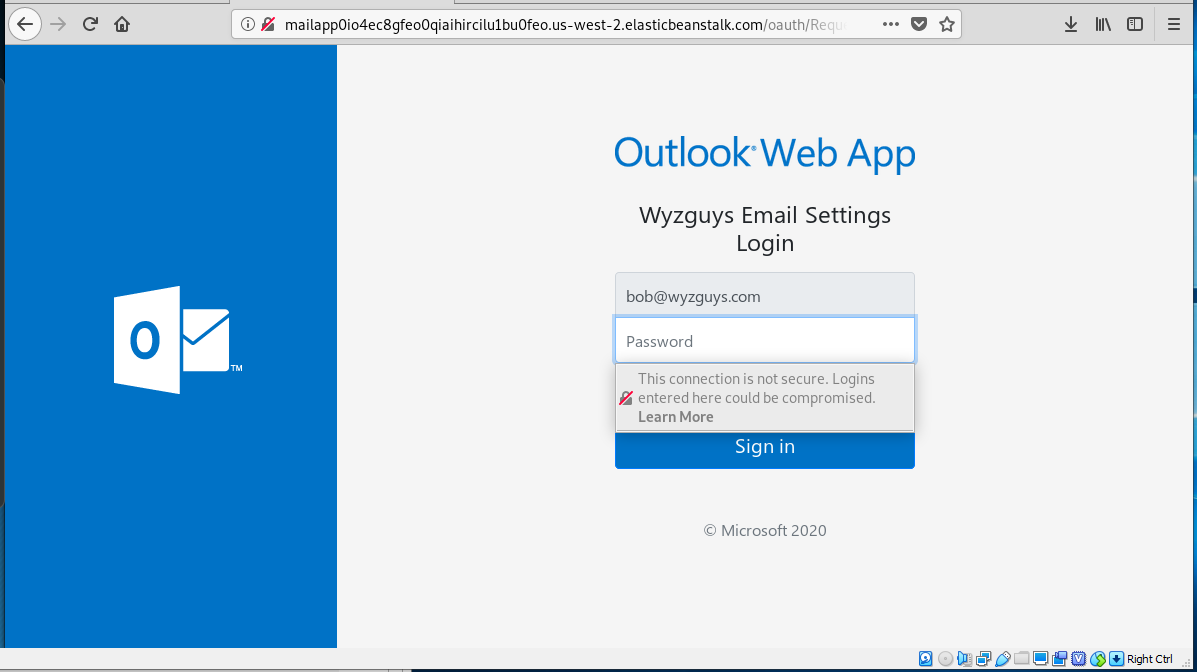
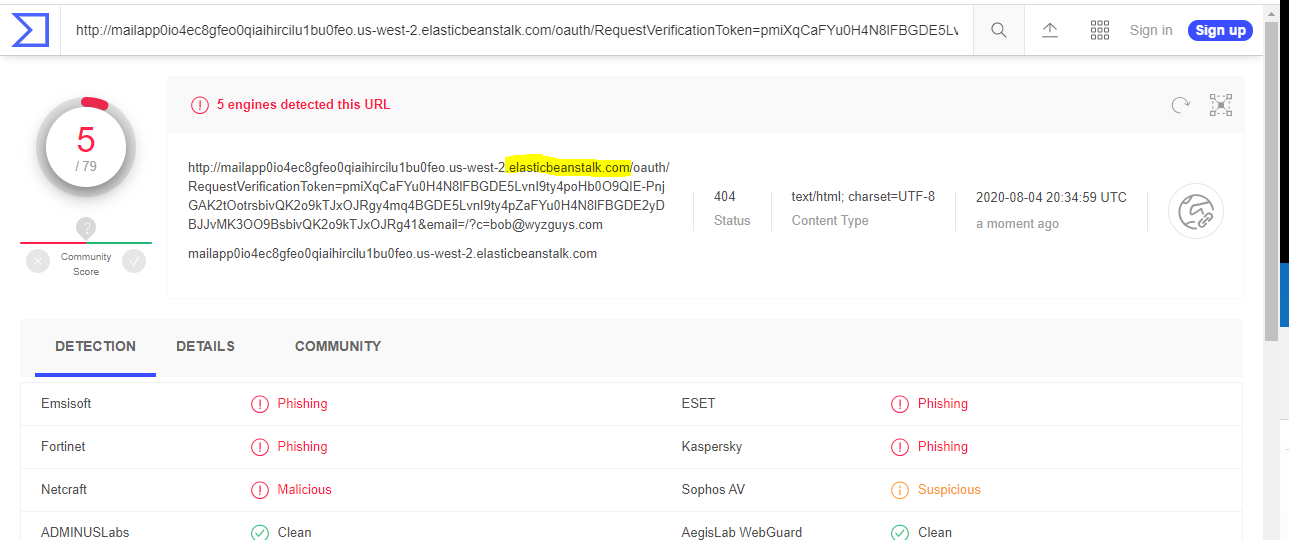
Using Office 365 in phishing exploits has become a popular ploy for cyber-criminals. Here’s an example I received. It looks like I have been send a sharing link to a quarterly financial report using Microsoft Excel. The link resolved to a long link with the domain name elasticbeanstalk.com in it. Goofy domain names are cause for suspicion. The sender email address appears to be me.
Here is the landing page. This appears to be an Office365 credential harvesting operation. Clicking on the password box displayed a warning panel, and entering a fake password spawned an error message.
VirusTotal identified the link as phishing related. Keep an eye out for this and similar exploits using Excel, Word, and Outlook. The goal here is to get your user credentials and take over your Office 365 account.
Arresting Voice Message
Here is a transcription of part of a vishing (voice phishing) exploit. My Google Voice system did not catch all of the recording, but evidently some branch of the government wants to have me arrested. These automated telephone messages are always a fraud. Just hang up. I have, many times, and no one has come to arrest me yet.
Spam or Phish?
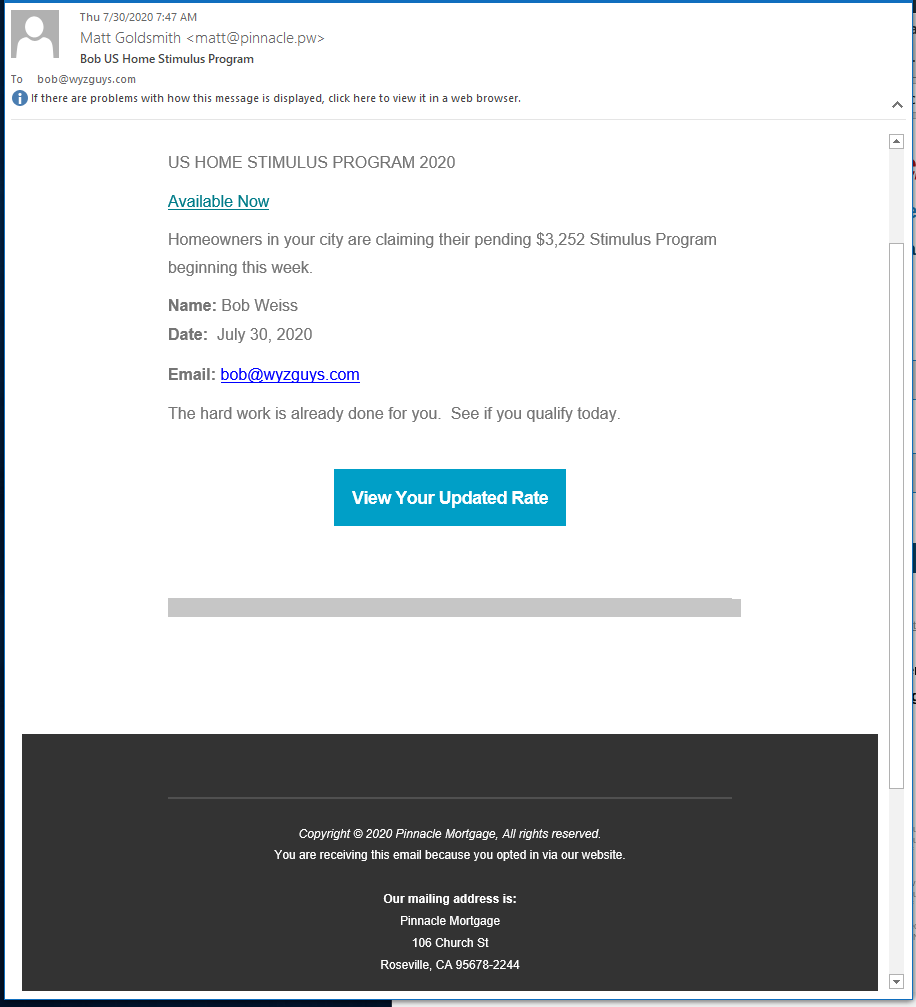
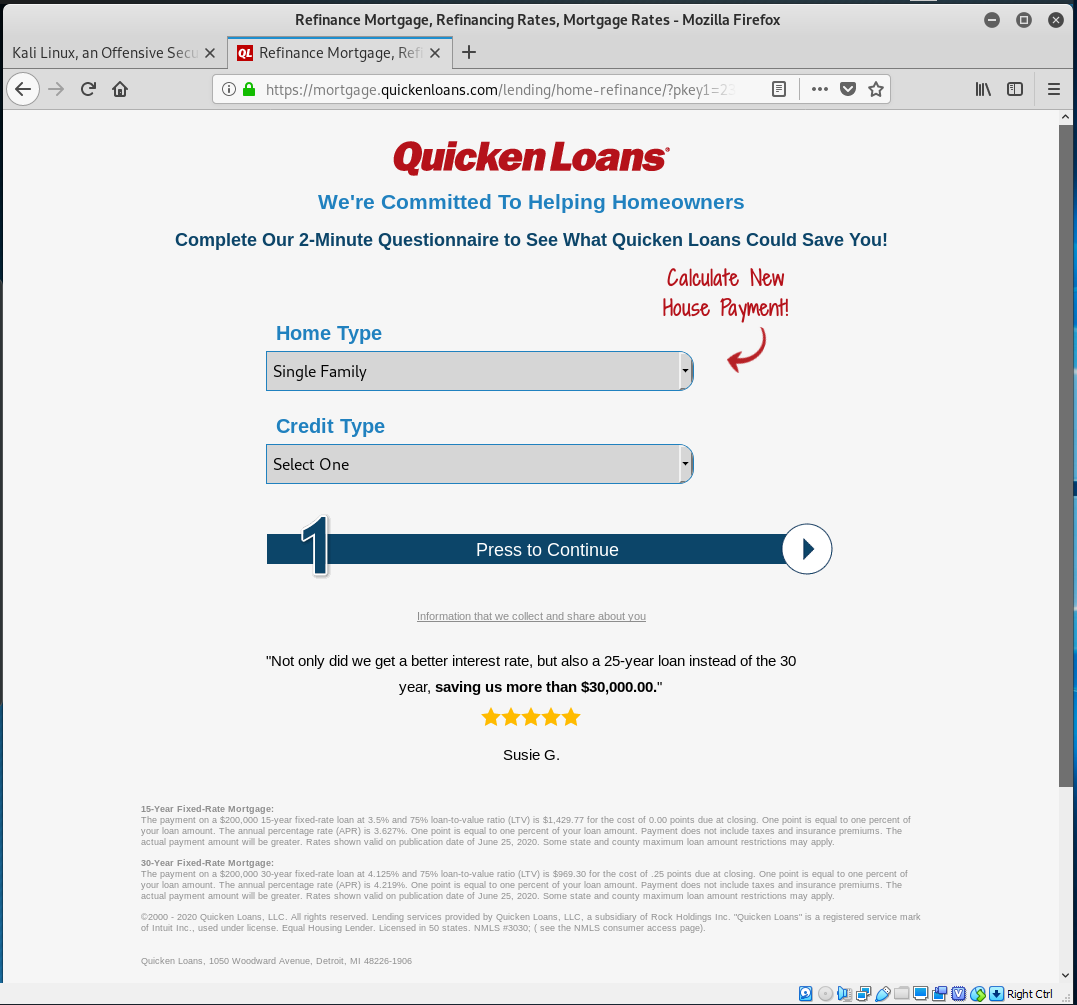
I got this email and it looked phishy to me, but turned out to be affiliate marketing spam from a company called Pinnacle Mortgage. The View Rate button resolved to https://pinnacle.us17.list-manage.com/track/click?u=97fec901dcfb3e7fab34b1560&id=af05d31857&e=e3a7c98481, which was redirected to a genuine Quicken Loans page at https://mortgage.quickenloans.com/lending/home-refinance/?pkey1=233&pkey2=41706&pkey3=1007&sourceid=lmb-54867-113582-233.
So this time? Spam.
More Spam From National Credit Report
I reported earlier in Friday Phish Fry about the spamming service I accidentally subscribed to with National Credit Report. Here’s another example of their handy-work. In this email they suggest that there have been two derogatory credit marks, but when I checked my credit score through Experian, everything was fine, of course. Not chasing the links on this one, but they did resolve to nationalcreditreport.com again.
Never click through the link on these sorts of emails. If it is anything credit related, you can check it out online directly with Experian, Equifax, or TransUnion, or your credit card provider may provide free credit scores and reports. Just use someone else that you trust.
Click Bank Phish or Spam
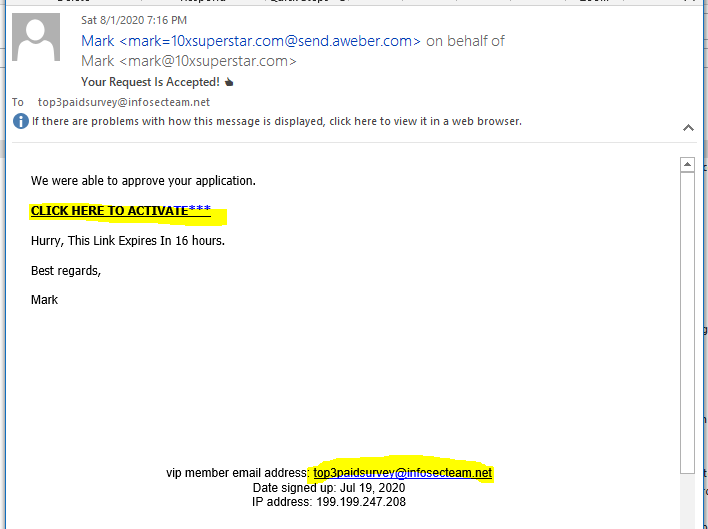
Not even sure what the message means with this phish. They DID NOT approve my application, the one I didn’t make. But I should CLICK HERE TO ACTIVATE. This email has the usual sender problems, and was sent to the email address I created for another scam. So I basically got myself into a spam group.
The CLICK HERE link resolved to https://clicks.aweber.com/y/ct/?l=DsKc7&m=8prgRRr5rwJUcg26&b=h0y8IvHVMt.YbMIpaecW8Q and was redirected to https://www.trackyour.link/perpincome/?link=aweber&hop=media898&vendor=perpincome&pagetype=watch&index=9. Virustotal reported both links as “Suspicious.”
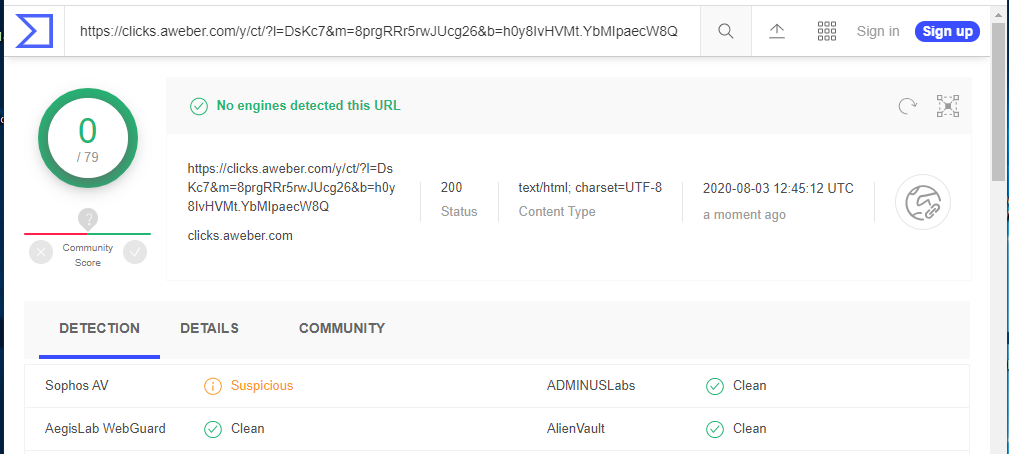 The landing page was basically a come-on for a Click Bank sign-up. This is another instant Internet riches scheme for the foolish and gullible.
The landing page was basically a come-on for a Click Bank sign-up. This is another instant Internet riches scheme for the foolish and gullible.
Voicemail-Themed Phishing Attacks Are on the Rise
Researchers at Zscaler warn of an increase in voicemail-themed phishing campaigns designed to steal credentials for enterprise applications. The emails purport to be automatically generated notifications from enterprise applications, like Office 365 and Outlook, informing recipients that they’ve received a voicemail from a caller.
The messages include an HTML attachment that will redirect the user to the phishing site, where they’ll be asked to enter their credentials in order to log in and hear the message.
Interestingly, Zscaler found that one of these campaigns used Google’s reCAPTCHA to prevent web crawlers from accessing the site and flagging the site as malicious.
The researchers also observed a campaign that spoofed Cisco’s Unity Connection voicemail portal using the domain “secure[.]ciscovoicemail[.]cf.“ When the user clicks to listen to their voicemail, they’ll be taken to a page that asks them to select their email provider from a list of options: Office 365, Mimecast, Outlook, Gmail, Yahoo, and “Others.”
Clicking on any of these options would take the user to a phishing page that spoofed the login page of the service they selected. Choosing “Others” would present the user with a generic login portal.
Zscaler concludes that users should follow security best practices in order to avoid falling for these attacks. “This threat actor leverages well-crafted social engineering techniques and combines them with evasion tactics designed to bypass automated URL analysis solutions to achieve better success in reaching users and stealing their credentials,” the researchers write.
“As an extra precaution, users should not open attachments in emails sent from untrusted or unknown sources. As a best practice, in general, users should verify the URL in the address bar of the browser before entering any credentials.”
It’s also worth noting that voicemail-themed phishing campaigns aren’t new, but the fact that they’re growing more common means this tactic is still effective. If a user knows that attackers frequently use fake voicemail notifications as phishbait, they can recognize these attacks immediately.
New-school security awareness training can help your employees stay up to date with evolving phishing trends, as well as reminding them about the fundamentals of social engineering.
Share
AUG








About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com