 Phishing Email Alerts
Phishing Email Alerts
Examples of clever phish that made it past my spam filters and into my Inbox, or from reliable sources on the Internet.
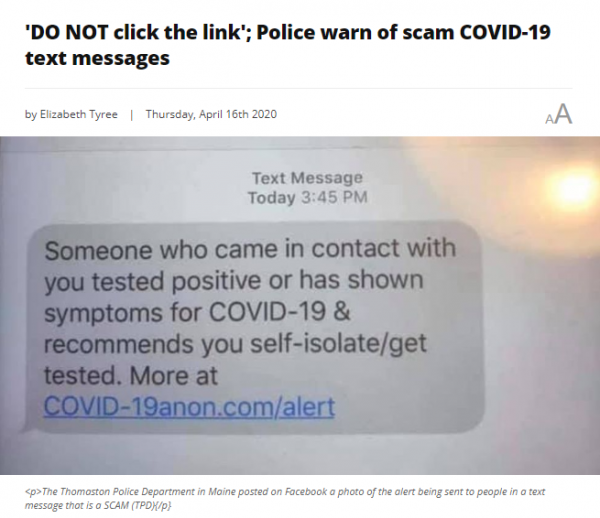
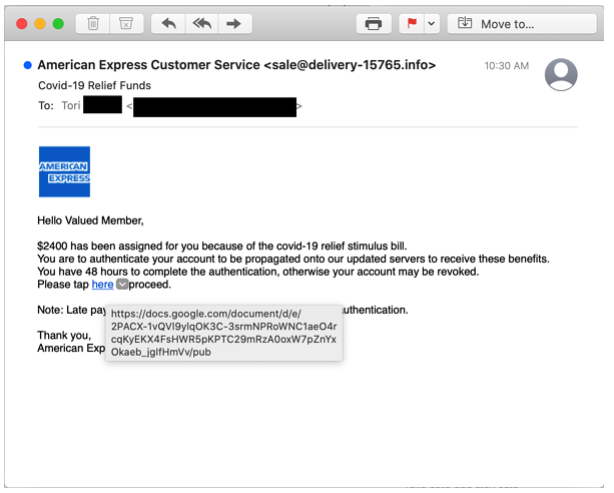
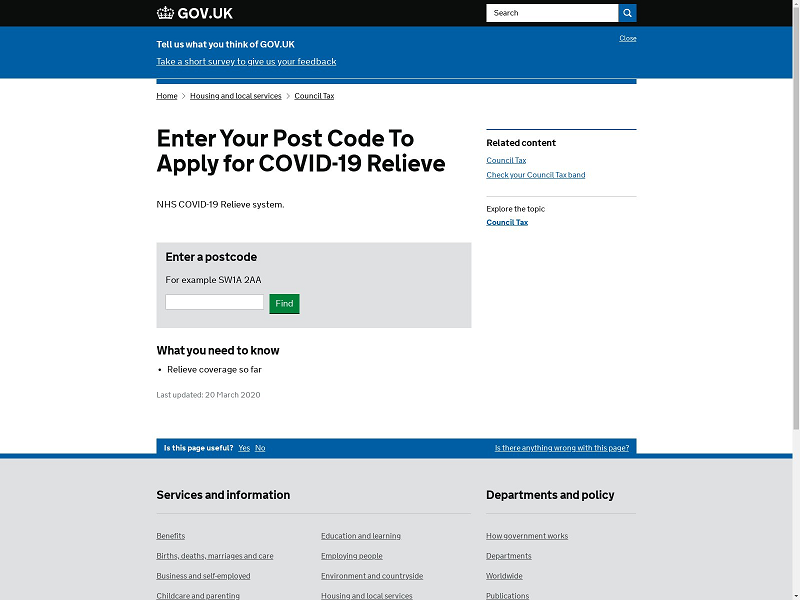
Late Entry: COVID-19 infection alert is fake.
Emails and text message about COVID-19 infections or information need to be treated with the utmost suspicion. Do not click through the links, or with emails, open any attachments.
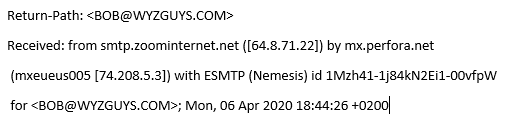
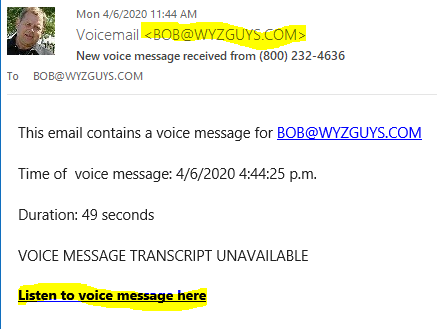
Voicemail Phish
In this email, I am both the sender and the receiver, which is odd. Here is the email header, which shows the last mail server was smtp.zoominternet.net.
Link to “Listen to voice message here” resolves to https://commercialserragrande.com.br/ wp-content/[plugins/smart-logo-showcase-lite/js/?ap__=bob@wyzguys.com. This appears to be a corrupted plugin on a WordPress site in Brazil. In turn it resolves to https://fourthandfifty.com/wp-include/public_html/fourth/homes/1150/hs7rkd/enterpassword.php?b1iDGD1586201162a5918e0840d7739243a29130b764419ba5918e0840d7739243a29130b764419ba5918e0840d7739243a29130b764419ba5918e0840d7739243a29130b764419ba5918e0840d7739243a29130b764419b&AP___=BOB@WYZGUYS.COM&error=
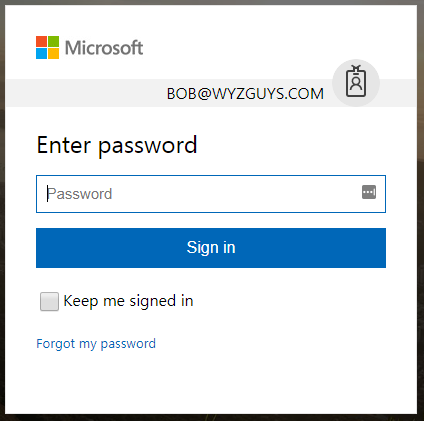
This displays a fake Microsoft Office365 login screen. This exploit is apparently trying to steal your Office365 password.
KnowBe4 Provides Data on COVID-19 Phishing Activity
This is why I started the Phish Fry. Looks like the same “infection” rate as the actual disease. Be safe – out there AND online. Click through link for full article.
Click through to the article on KnowBe4.
AA20-099A: COVID-19 Exploited by Malicious Cyber Actors
Original release date: April 8, 2020 – From CISA/US-CERT
APT groups are using the COVID-19 pandemic as part of their cyber operations. These cyber threat actors will often masquerade as trusted entities. Their activity includes using coronavirus-themed phishing messages or malicious applications, often masquerading as trusted entities that may have been previously compromised. Their goals and targets are consistent with long-standing priorities such as espionage and “hack-and-leak” operations. Cybercriminals are using the pandemic for commercial gain, deploying a variety of ransomware and other malware. Read more...
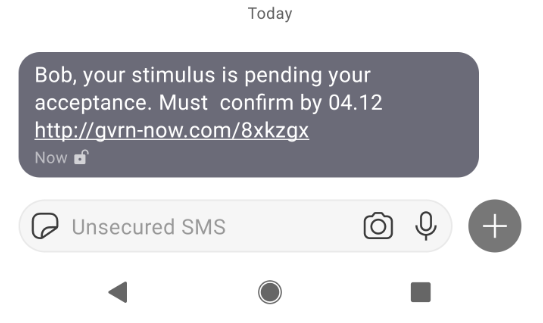
Fake Stimulus Payment SMS
Sextortion emails and porn scams are back – don’t let them scare you!
There is no video and the whole thing is a scam to prey on your fears.
Malicious coronavirus-themed apps target Android devices
Purporting to offer help and info on COVID-19, the apps can let hackers take control of devices to access files, contacts, the calendar, and more, according to Check Point Research. None of the apps come from an official store such as Google Play. Instead, they’re hosted on new coronavirus-themed domains, which Check Point researchers believe were created for the sole purpose of tricking unsuspecting users.
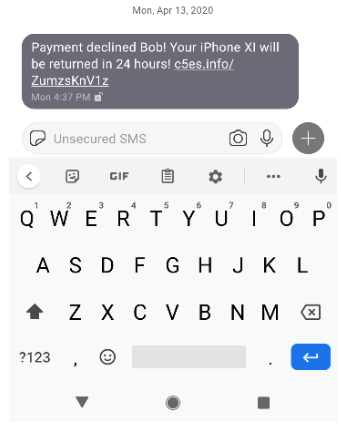
Fake iPhone SMS phish
I don’t even like iPhones. Why would I order one?
Share
APR






About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com