![]() This week we are taking a deeper look at VPN services courtesy of a guest post from The Gadget Enthusiast.
This week we are taking a deeper look at VPN services courtesy of a guest post from The Gadget Enthusiast.
Unless you’re living under a rock for the past 10 years or so, you’ll know that VPN stands for the “virtual private network.”
It is a service that lets you access any website over the web, from anywhere, securely by routing your data and keeping the connection private.
A secure tunnel is formed between you and your destination, and data is encrypted by the VPN server to ensure your privacy.
But most people’s knowledge about VPNs ends right here.
I mean they obviously know what a VPN is: but don’t know how a VPN works, its different uses (except using it to access p*rn sites), and on which devices they can use it.
So, if there’s a geek within you, keep reading.
Actually, there are two classes of virtual private networks (VPNs): Network-based and Client-based.
- In network-based VPNs, two different networks are connected to have a private network between them. For example, connecting two branches or offices of the same company or different companies over the public internet.
- In client-based VPNs, a user with a laptop or smartphone can connect to its private office network, or a website, for resource-sharing regardless of its physical location. This second type of VPNs is more commonly used.
That being said, these are not the only scenarios where a VPN can be used.
In fact, dedicated leased lines from the ISP to local sites were used to connect between the sites, in the past. VPN technology has advantages over the traditional leased lines like bandwidth utilization, encryption, cost efficiency, etc.
How a VPN Works
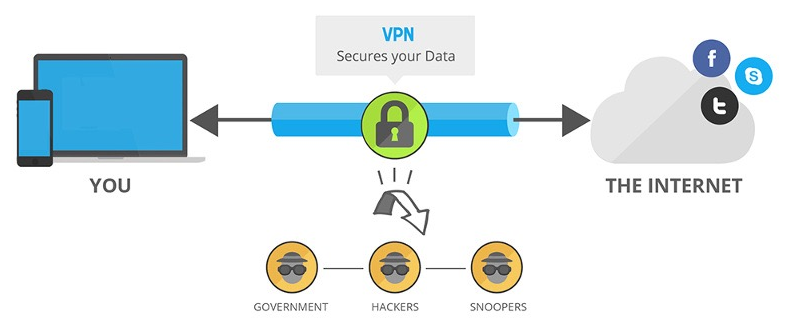
Picture Credits: seahaggdistillery.com
The usual process of how a VPN works (from a user’s point-of-view) goes something like this:
You start a VPN software/app from a VPN service and connect through one of their available servers (which are located in different places around the globe).
That service, then, creates a secure tunnel between your device and your destination, and your IP address is replaced by the one given by that VPN service.
After this, your requested data is processed from the VPN server on your behalf. Since all the traffic passing through the VPN server is encrypted, no one can decipher it – even if they manage to intercept it somehow.
The above picture rightfully illustrates how a VPN works, but watch out the following video for further explanation.
Are VPNs Entirely Legit?
VPNs are legal in most of the countries around the world. In regions like the Americas and Western Europe, there’s no restriction on the usage of VPN services.
The important thing for you to note here, however, is that what matters most is your physical location, not the location of the service/website you’re trying to access.
The countries where 3rd-party VPN usage is generally discouraged, include China, North Korea, Iraq, United Arab Emirates, and Iran.
Do VPNs Make Us Really Anonymous?
 No, a VPN cannot make you completely anonymous.
No, a VPN cannot make you completely anonymous.
Just think about how much cyber-crimes will be increased if anyone becomes completely anonymous only by using a VPN.
VPN is just a secure tunnel from your PC to your requested website. Although this tunnel is tough to be hacked, you can be tracked with some effort.
It actually depends upon your VPN service provider because many of them have your data and if they share your information and data with any law enforcement agency, you can be tracked back very quickly.
If you want to be truly anonymous, you need to use the VPN that does not record your online activities in their server, and those are usually paid VPNs.
Who Wants to Steal Your Online Data?
Many of us think that it’s only the hackers or “bad people” who want to have a sneak peek on our online data even though they’re just one part of the equation.
Large tech corporations take your data and sell it to advertisers. These advertisers, then, classify your profile into different consumer sections and then send you targeted ads about their product/services.
Social media sites may take footprints of your online activity (the links you click on, the media you share/like, and how much time you spend on their sites, etc.) to improve website design or implement new features to keep users engaged.
But this is just the tip of the iceberg. From insurance companies to Big data scientists to actual governments, there’s a lot of people looking for your data.
We will continue this article in our next post.
More information:
ShareMAY




About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com