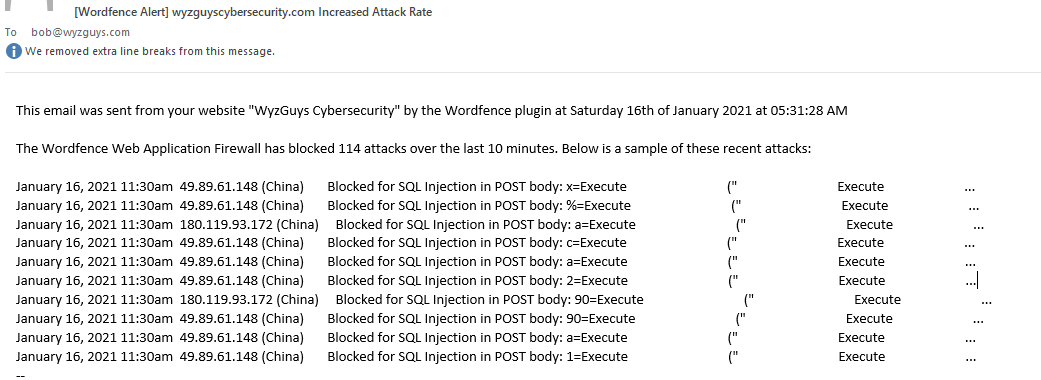
SQL injection is one of the top ten web site and web application exploits, according to OWASP, the Online Web Application Security Project. I use Wordfence, a popular security plugin on my website, and occasionally Wordfence sends sends reports like the one below. Double clicking on the picture will open it in a photo viewer, and allow you to see it full size.
What we see here are two concurrent automated attacks from two different IP addresses in China. A sample of the injection code looks like this:
x=Execute (” Execute …
%=Execute (” Execute …
a=Execute (” Execute …
SQL injection or SQLi is a popular topic for cybersecurity certification exam questions, which is why I am writing this article. There are links below to resources at OWASP and from the Portswigger blog that can help you learn more about SQLi and how to recognize it.
Of course, if you operate, support, or design web sites and web applications, SQLi should be at the top of your list, too. SQLi can be used to examine a database, copy and exfiltrate database records, and maliciously modify database information (think changing all your prices to one cent), or delete tables and entire databases. SQLi can be used to interfere with application instructions as well.
Check out the excellent article on PortSwigger if you want to go deeper on this topic.
More information:
- OWASP SQL Injection
- OWASP Top 10
- PortSwigger SQL post
- W3 Schools SQL Tutorial
- PC & Network Downloads – SQL Cheat Sheet
Share
FEB




About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com