 A quick Saturday digest of cybersecurity news articles from other sources.
A quick Saturday digest of cybersecurity news articles from other sources.
How to expand your search sources
Explore search services beyond Google and Bing for a wider range of results, customization and privacy options.
If you search the web in English, you most likely use Google. Search engine market share lists consistently show Google at more than 80% market share, with Microsoft’s Bing a distant second at around 8% market share. On mobile devices, even Apple selects Google as the default search provider.
For searches with a single specific and factual answer, your choice between Google, Bing or another search provider may not matter. For example, both search engines provide rapid and accurate results when you want to know what year the IBM PC was first manufactured (1981) or which team won the Men’s 2022 FIFA World Cup (Argentina).
However, when your intent is to glean information from a wide range of sources, it makes sense to query different search engines. For example, searching both Google and Bing for “edge computing best practices” or “use vi and tmux” provides slightly different sets of linked pages to review.
The search alternatives covered in the full article include not only truly independent search sources but also secondary search services. These secondary search services often depend on Bing or Google results that the service then filters and sorts differently than the source search indexes.
Google as a tool to search for information is getting worse.
> [I f***ing hate Google anymore. 5 years ago you would have searched that and found a definite answer and guide on how to find … Read More
5G vs 6G: What’s the difference?
In a world of constant technological evolution, it can be hard to keep up with the latest advancements. Here, we compare 5G and 6G networks to help you understand the differences between the two.
Twitter tells users: Pay up if you want to keep using insecure 2FA
Ironically, Twitter Blue users will be allowed to keep using the very 2FA process that’s not considered secure enough for everyone else.
GoDaddy admits: Crooks hit us with malware, poisoned customer websites
New report admits that attackers were detected in the network about three months ago, and may have been attacking for about three years.
Cloudflare Blocks Record DDoS Attack as Threats Surge
The attacks, which originated from more than 30,000 different IP addresses, targeted websites including a gaming provider, cryptocurrency companies, hosting providers, and cloud computing platforms.
Some SQL Injection commands to try
Some MySQL tricks to break some #WAFs by @brutelogic
SELECT-1e1FROM`test`
SELECT~1.FROM`test`
SELECT\NFROM`test`
SELECT@^1.FROM`test`
SELECT-id-1.FROM`test`
credits: @brutelogic
Also check out the great SQL Cheat Sheet post at PC & Network Downloads – SQL Cheat Sheet
Coinbase breached by social engineers, employee data stolen
Another day, another “sophisticated” attack. This time, the company has handily included some useful advice along with its mea culpa…
IBM: Most ransomware blocked last year, but cyberattacks are moving faster
A new study from IBM Security suggests cyber-attackers are taking side routes that are less visible, and they are getting much faster at infiltrating perimeters.
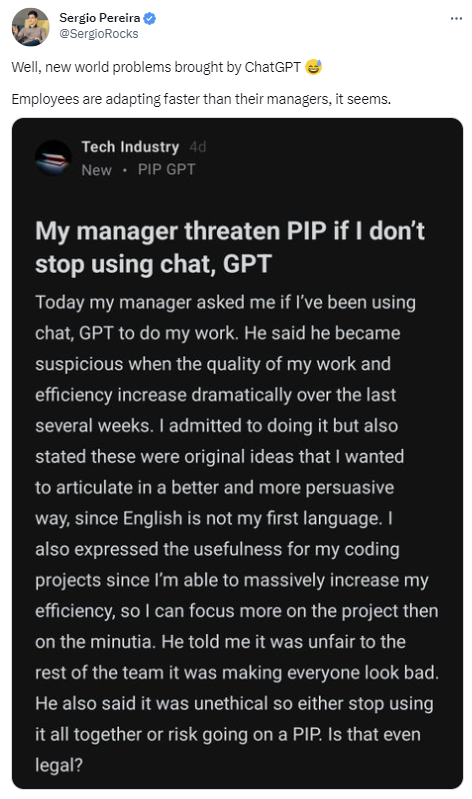
Fun with ChatGPT
I remember a story/urban legend about a coder who allegedly outsourced all his projects to a coding team in India, basically splitting his salary with his dev team. He got caught because he was the only coder to leave on time and 5:00 pm and never worked a weekend. Seems like ChatGPT has removed the requirement to pay your dev team.
CISA Urges Increased Vigilance One Year After Russia’s Invasion of Ukraine
Original Release Date: February 23, 2023
CISA assesses that the United States and European nations may experience disruptive and defacement attacks against websites in an attempt to sow chaos and societal discord on February 24, 2023, the anniversary of Russia’s 2022 invasion of Ukraine. CISA urges organizations and individuals to increase their cyber vigilance in response to this potential threat.
In response to the heightened geopolitical tensions resulting from Russia’s full-scale invasion of Ukraine, CISA maintains public cybersecurity resources, including Shields Up—a one-stop webpage that provides resources to increase organizational vigilance and keep the public informed about current cybersecurity threats. CISA recommends that all organizations review and consider implementing the below guidance:
- DDoS Attack Guidance for Organizations and Federal Agencies
- Shields Up webpage, which includes guidance on:
- Increasing organizational vigilance
- Implementing cybersecurity best practices
- Increasing resilience and preparing for rapid response
- Lowering the threshold for threat and information sharing
Share
MAR





About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com