 A quick Saturday digest of cybersecurity news articles from other sources.
A quick Saturday digest of cybersecurity news articles from other sources.
Cyberbullying Toolkit for Children – An Effective Guide to Help Them Deal with It
While social media has made communication more efficient, it has also paved the way for problems like cyberbullying. Such issues often have drastic consequences and leave a lasting impact on young minds. Therefore, providing a cyberbullying toolkit for children to help them effectively deal with its negative influences is the need of the hour. So, let us begin by understanding what cyberbullying looks like and how we can help kids identify it.
What Is Cyberbullying?
The United Nations International Children’s Emergency Fund (UNICEF) has defined cyberbullying in the following words.
“Cyberbullying is bullying with the use of digital technologies. It can take place on social media, messaging platforms, gaming platforms, and mobile phones. It is repeated behavior, aimed at scaring, angering or shaming the targeted individuals.”
Cyberbullying can occur in the form of nasty comments, name-calling, false claims, accusations, belittling, and the like. In reality, cyberbullying is precisely like regular old bullying. The only difference is that it happens online, and kids may not know who is targeting them.
Therefore, parents need to help kids effectively deal with it by providing them with a cyberbullying toolkit for children. It is the best way to help abolish the detrimental impacts of this issue on their mental health. More…
Microsoft Warns Against Recent, Complex, Ransomware Campaign
Microsoft has observed a threat actor that’s been running a phishing campaign since August 2022. The threat actor, which Microsoft tracks as “DEV-0569,” is using phishing emails to distribute malicious installers for legitimate apps, including TeamViewer, Microsoft Teams, Adobe Flash Player, Zoom and AnyDesk. The phishing campaign leads to the installation of ransomware and information-stealing malware.
“Historical observation of [a] typical DEV-0569 attack begins with malicious links delivered to targets via malicious ads, fake forum pages, blog comments, or through phishing emails,” the researchers write. “These links lead to malicious files signed by the attacker using a legitimate certificate.
“The malicious files, which are malware downloaders known as BATLOADER, pose as installers or updates for legitimate applications like Microsoft Teams or Zoom. When launched, BATLOADER uses MSI Custom Actions to launch malicious PowerShell activity or run batch scripts to aid in disabling security solutions and lead to the delivery of various encrypted malware payloads that are decrypted and launched with PowerShell commands.”
In the most recent campaign, the threat actor is using website contact forms, legitimate software depositories and Google Ads to distribute their links.
“In late October 2022, Microsoft researchers identified a DEV-0569 malvertising campaign leveraging Google Ads that point to the legitimate traffic distribution system (TDS) Keitaro, which provides capabilities to customize advertising campaigns via tracking ad traffic and user- or device-based filtering,” the researchers write.
“Microsoft observed that the TDS redirects the user to a legitimate download site, or under certain conditions, to the malicious BATLOADER download site. Microsoft reported this abuse to Google for awareness and consideration for action. Using Keitaro, DEV-0569 can use traffic filtering provided by Keitaro to deliver their payloads to specified IP ranges and targets. This traffic filtering can also aid DEV-0569 in avoiding IP ranges of known security sandboxing solutions.”
Blog post with links:
https://blog.knowbe4.com/a-recent-complex-ransomware-campaign
5 Top Scams to Watch Out for This Holiday Season
Here is a 3-minute article that we suggest you copy/paste and send to all your users:
“The holiday season is a time when people are especially vulnerable to scams. This is because they are busy and often have their guard down. Criminals take advantage of this by circulating fake e-gift cards, posing as charities, targeting specific demographics, and so on. In this 3-minute article, we will discuss ‘Google’s five most popular scams’ being circulated this holiday season. So if you want to be aware of the dangers lurking online, then keep reading!
- E-gift card scams
- Charities
- Demographic Targeting
- Subscription renewals
- Crypto scams
“With the holiday season in full swing, so are gift card and prize scams. These scammers will often lie about being a known contact of yours to try and get you to buy them a gift card, or they may offer an amazing prize in exchange for your credit card information. If you receive any suspicious emails like this from someone claiming to be your friend, make sure to confirm it with them through another method before doing anything further. And as always, if something seems too good to be true, it probably is.
“Be wary of scammers and phishing attempts; they actually worsen during the holiday season. This would not only hurt those who fall for the scams, but also charities that could’ve benefited from donations. For example, an attacker may pretend to be associated with a charity related to current events or one with a familiar name. If someone contacts you asking for money via personal email or another method, beware that it might be fraudulent.
“With more people shopping online and sharing personal information this holiday season, scammers are taking advantage by targeting consumers with fraud that seems more realistic. For example, you might get an email from what looks like your child’s school PTA about a holiday fundraiser.
“But if you click on the link in the email, it could take you to a fake website where you’re asked to enter sensitive information like your credit card number or Social Security Number. These types of scams can be difficult to identify because they seem so personalized. But if you’re aware of potential threats and know what to look for, you can help protect yourself against them.
“Scammers love to target people at the end of the year, and one particularly nasty version of these emails spoofs antivirus services. They lure victims with promises of improved security, but if you take a closer look at the sender’s email address, you can usually spot these scams pretty easily.
“Cryptocurrency-based scammers are more prevalent during times of higher crypto usage, like now. They often use a cryptocurrency wallet to collect payment and may threaten their victim if they don’t receive the funds. Gmail usually sends a warning about these kinds of emails, but it’s helpful to know how to spot them on your own too. Some key things to look out for that signal fraud include typos, strange email addresses, and demands for payment.
“By being aware of these five popular scams circulating this holiday season, you can protect yourself and your loved ones from potential fraud.”
Blog post with links:
https://blog.knowbe4.com/send-this-to-your-users-5-top-scams-to-watch-out-for-this-holiday-season
Voice-scamming site “iSpoof” seized, 100s arrested in massive crackdown
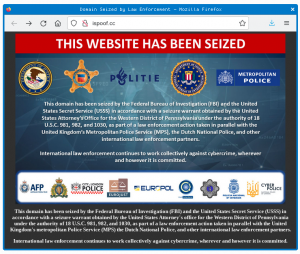 Those numbers or names that pop up when a call comes up? They’re OK as a hint of who’s calling, but THEY PROVE NOTHING.
Those numbers or names that pop up when a call comes up? They’re OK as a hint of who’s calling, but THEY PROVE NOTHING.
These days, most of us have telephones that display the number that’s calling before we answer. This “feature” actually goes right back to the 1960s, and it’s known in North American English as Caller ID, although it doesn’t actually identify the caller, just the caller’s number. Elsewhere in the English-speaking world, you’ll see the name CLI used instead, short for Calling Line Identification, which seems at first glance to be a better, more precise term.
But here’s the thing: whether you call it Caller ID or CLI, it’s no more use in identifying the caller’s actual phone number than the From: header in an email is at identifying the sender of an email. More..
Share
DEC




About the Author:
I am a cybersecurity and IT instructor, cybersecurity analyst, pen-tester, trainer, and speaker. I am an owner of the WyzCo Group Inc. In addition to consulting on security products and services, I also conduct security audits, compliance audits, vulnerability assessments and penetration tests. I also teach Cybersecurity Awareness Training classes. I work as an information technology and cybersecurity instructor for several training and certification organizations. I have worked in corporate, military, government, and workforce development training environments I am a frequent speaker at professional conferences such as the Minnesota Bloggers Conference, Secure360 Security Conference in 2016, 2017, 2018, 2019, the (ISC)2 World Congress 2016, and the ISSA International Conference 2017, and many local community organizations, including Chambers of Commerce, SCORE, and several school districts. I have been blogging on cybersecurity since 2006 at http://wyzguyscybersecurity.com